CompTIA A+ Certification - Core 2 (V15) - (220-1202) Exam Questions
Total Questions
Last Updated
1st Try Guaranteed

Experts Verified
Question 1 Single Choice
A user downloads an application with a plug-in that is designed to automatically prompt for a one-time password (OTP) when visiting a specific website. The plug-in installs without any warnings or errors. However, when the user visits the site for the first time, the OTP prompt does not appear, and the user is unable to log in.
Which of the following browser settings should the user configure?
Explanation

Click "Show Answer" to see the explanation here
Extensions/add-ins
Extensions (also known as add-ins or plug-ins) are small programs that enhance browser functionality—such as autofill tools, password managers, or OTP generators.
In this case, the plug-in that should trigger the OTP prompt is likely disabled or not configured correctly in the Extensions/Add-ins section of the browser.
To fix this:
Go to the browser’s settings (e.g., Chrome:
chrome://extensions)Ensure the plug-in is enabled
Check that it has permission to run on the intended website
❌ Other Options Explained:
Certificate validity
This setting deals with HTTPS and SSL/TLS certificates. It ensures websites use valid, secure certificates.
While important for overall security, it won’t affect whether a browser plug-in launches.Proxy settings
Proxies reroute internet traffic through an intermediary server.
Misconfigured proxies can prevent access to websites altogether, but they don’t block plug-ins from functioning.Trusted sources
This refers to download permissions or script execution, usually in corporate environments.
However, if the extension was already installed successfully, trusted sources wouldn’t impact its ability to run on a page.
Explanation
Extensions/add-ins
Extensions (also known as add-ins or plug-ins) are small programs that enhance browser functionality—such as autofill tools, password managers, or OTP generators.
In this case, the plug-in that should trigger the OTP prompt is likely disabled or not configured correctly in the Extensions/Add-ins section of the browser.
To fix this:
Go to the browser’s settings (e.g., Chrome:
chrome://extensions)Ensure the plug-in is enabled
Check that it has permission to run on the intended website
❌ Other Options Explained:
Certificate validity
This setting deals with HTTPS and SSL/TLS certificates. It ensures websites use valid, secure certificates.
While important for overall security, it won’t affect whether a browser plug-in launches.Proxy settings
Proxies reroute internet traffic through an intermediary server.
Misconfigured proxies can prevent access to websites altogether, but they don’t block plug-ins from functioning.Trusted sources
This refers to download permissions or script execution, usually in corporate environments.
However, if the extension was already installed successfully, trusted sources wouldn’t impact its ability to run on a page.
Question 2 Single Choice
Which of the following will automatically map network drives based on Group Policy configuration?
Explanation

Click "Show Answer" to see the explanation here
Log-in scripts
Log-in scripts are used within Group Policy to automate tasks during user login, such as mapping network drives, setting environment variables, and launching applications. These scripts can be assigned via Group Policy Objects (GPOs) and run automatically when a user logs into a system that is part of the domain.
❌ Other Options Explained:
Access control lists:
These define permissions (read, write, execute) for users on files or folders but are not used to map drives.Organizational units:
OUs are containers in Active Directory used for organizing users and computers, but they do not perform drive mapping themselves.Folder redirection:
This redirects the path of a folder to a network location (e.g., Documents), but it does not map network drives.
Explanation
Log-in scripts
Log-in scripts are used within Group Policy to automate tasks during user login, such as mapping network drives, setting environment variables, and launching applications. These scripts can be assigned via Group Policy Objects (GPOs) and run automatically when a user logs into a system that is part of the domain.
❌ Other Options Explained:
Access control lists:
These define permissions (read, write, execute) for users on files or folders but are not used to map drives.Organizational units:
OUs are containers in Active Directory used for organizing users and computers, but they do not perform drive mapping themselves.Folder redirection:
This redirects the path of a folder to a network location (e.g., Documents), but it does not map network drives.
Question 3 Single Choice
After a user recently installs a new scanner and the associated software on a computer, they notice the computer is now starting up very slowly. Which of the following is the best tool to troubleshoot this issue?
Explanation

Click "Show Answer" to see the explanation here
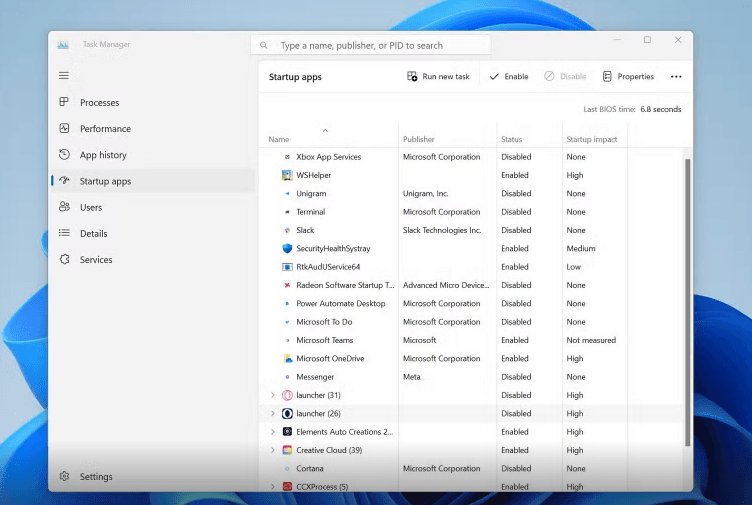
Task Manager
Task Manager helps identify and disable apps that slow down startup.
How to open in Windows 11:
Keyboard shortcut:
PressCtrl + Shift + Esc
(orCtrl + Alt + Delete> select Task Manager)Via Start menu:
Right-click the Start button (or pressWindows + X)
→ Select Task ManagerOnce open:
Go to the Startup apps tab
→ Look for the scanner software
→ Right-click and choose Disable if it's impacting performance
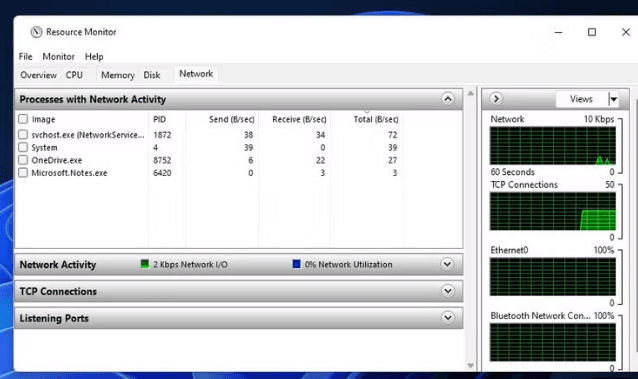
Other Options Explained:
Resource Monitor
Purpose:
Shows detailed resource usage (CPU, memory, disk, network), useful for deeper analysis.How to open in Windows 11:
Press
Windows + R, typeresmon, and pressEnterOR:
Open Task Manager > Go to the Performance tab > Click Open Resource Monitor at the bottom

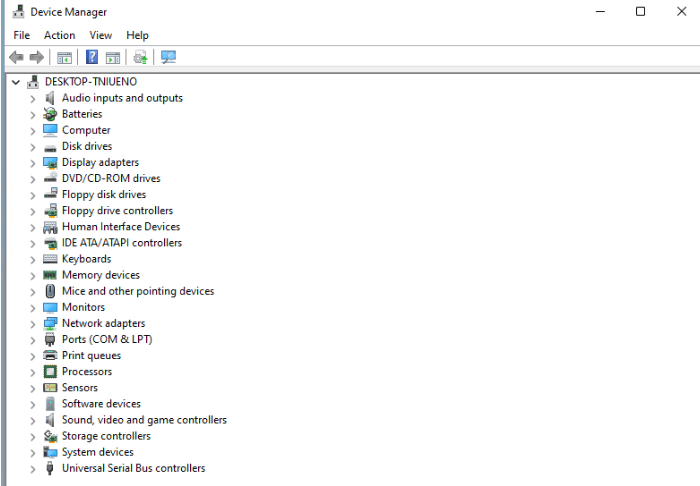
Device Manager
Purpose:
Used to view and manage device drivers (e.g., scanner hardware).How to open in Windows 11:
Right-click the Start button
→ Select Device ManagerOR:
PressWindows + R, typedevmgmt.msc, and pressEnterLook under Imaging devices or Printers to find the scanner
→ Right-click for Update, Disable, or Uninstall
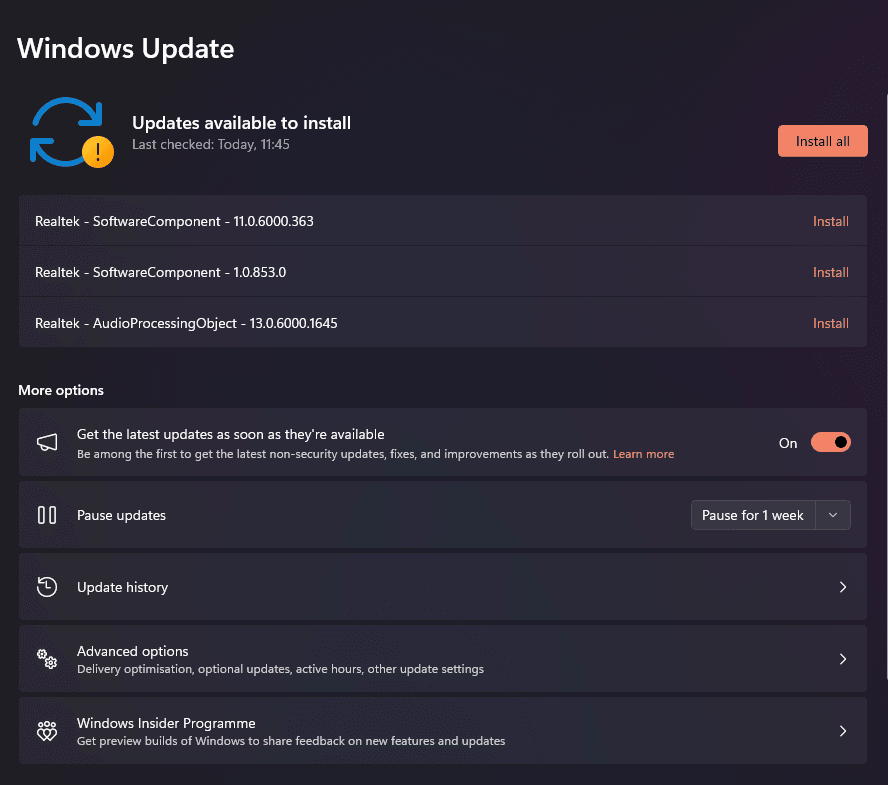
Windows Update
Purpose:
To check for driver and system updates that might improve performance.How to open in Windows 11:
Click Start > Settings
→ Go to Windows Update
→ Click Check for updatesYou can also type
Windows Updatein the search bar
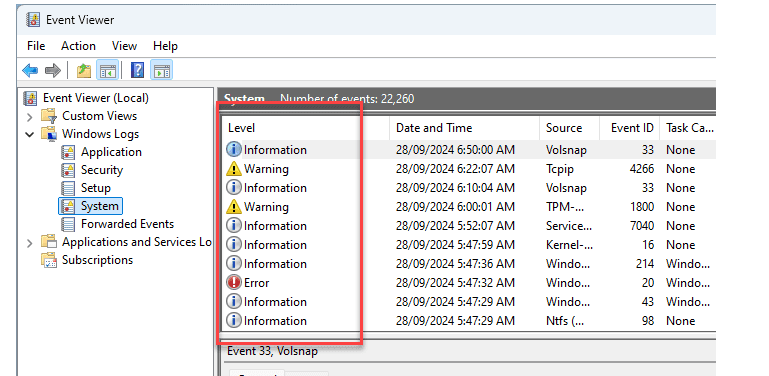
Event Viewer
Purpose:
Check logs for errors or warnings related to startup or the scanner.How to open in Windows 11:
Press
Windows + X
→ Select Event ViewerOR:
PressWindows + R, typeeventvwr.msc, and pressEnterNavigate to:
Windows Logs > System or Application
→ Look for Warnings or Errors around the time of startup

Explanation
Task Manager
Task Manager helps identify and disable apps that slow down startup.
How to open in Windows 11:
Keyboard shortcut:
PressCtrl + Shift + Esc
(orCtrl + Alt + Delete> select Task Manager)Via Start menu:
Right-click the Start button (or pressWindows + X)
→ Select Task ManagerOnce open:
Go to the Startup apps tab
→ Look for the scanner software
→ Right-click and choose Disable if it's impacting performance

Other Options Explained:
Resource Monitor
Purpose:
Shows detailed resource usage (CPU, memory, disk, network), useful for deeper analysis.How to open in Windows 11:
Press
Windows + R, typeresmon, and pressEnterOR:
Open Task Manager > Go to the Performance tab > Click Open Resource Monitor at the bottom

Device Manager
Purpose:
Used to view and manage device drivers (e.g., scanner hardware).How to open in Windows 11:
Right-click the Start button
→ Select Device ManagerOR:
PressWindows + R, typedevmgmt.msc, and pressEnterLook under Imaging devices or Printers to find the scanner
→ Right-click for Update, Disable, or Uninstall

Windows Update
Purpose:
To check for driver and system updates that might improve performance.How to open in Windows 11:
Click Start > Settings
→ Go to Windows Update
→ Click Check for updatesYou can also type
Windows Updatein the search bar

Event Viewer
Purpose:
Check logs for errors or warnings related to startup or the scanner.How to open in Windows 11:
Press
Windows + X
→ Select Event ViewerOR:
PressWindows + R, typeeventvwr.msc, and pressEnterNavigate to:
Windows Logs > System or Application
→ Look for Warnings or Errors around the time of startup

Question 4 Single Choice
A technician is working at a client office site, and the technician’s family member repeatedly calls and texts about a non-emergency situation. Which of the following should the technician do?
Explanation

Click "Show Answer" to see the explanation here
Put the phone on silent.
Explanation:
Putting the phone on silent is the most professional action. It minimizes distractions while still allowing the technician to focus on their job and maintain workplace etiquette. It also ensures the client sees that the technician is fully engaged in the work.
❌ Other Options:
Step aside and answer:
While this might seem polite, stepping away multiple times can appear unprofessional, especially for a non-emergency.Text a reply:
Actively replying during a client visit can still come across as inattentive or disrespectful, even if done quickly.Ignore the phone and continue working:
This may seem like a good idea, but it doesn’t stop the distractions. Repeated notifications can be disruptive unless the phone is silenced.
Explanation
Put the phone on silent.
Explanation:
Putting the phone on silent is the most professional action. It minimizes distractions while still allowing the technician to focus on their job and maintain workplace etiquette. It also ensures the client sees that the technician is fully engaged in the work.
❌ Other Options:
Step aside and answer:
While this might seem polite, stepping away multiple times can appear unprofessional, especially for a non-emergency.Text a reply:
Actively replying during a client visit can still come across as inattentive or disrespectful, even if done quickly.Ignore the phone and continue working:
This may seem like a good idea, but it doesn’t stop the distractions. Repeated notifications can be disruptive unless the phone is silenced.
Question 5 Single Choice
A technician is troubleshooting a PC that will not run Windows Defender. Windows Defender has been disabled, and no other antivirus is installed on the PC.
Which of the following would have caused this issue?
Explanation

Click "Show Answer" to see the explanation here
Rootkit
Explanation:
A rootkit is a type of stealthy malware designed to hide its presence and gain privileged access to a system. It can disable antivirus software like Windows Defender and remain hidden from detection tools. Since the system is not running any other antivirus, a rootkit is likely preventing Windows Defender from running to avoid being detected and removed.
❌ Ransomware
Ransomware encrypts files and locks users out of their systems, demanding payment to regain access. It doesn’t typically disable antivirus software in a stealthy way; instead, it announces itself.
❌ Spyware
Spyware monitors user activity and collects data, such as browsing habits and credentials. It may avoid detection, but it typically doesn't disable antivirus software at the system level like a rootkit does.
❌ Keylogger
A keylogger records keystrokes to capture sensitive information. It may run silently but is less likely to interfere with antivirus operations compared to a rootkit.
Explanation
Rootkit
Explanation:
A rootkit is a type of stealthy malware designed to hide its presence and gain privileged access to a system. It can disable antivirus software like Windows Defender and remain hidden from detection tools. Since the system is not running any other antivirus, a rootkit is likely preventing Windows Defender from running to avoid being detected and removed.
❌ Ransomware
Ransomware encrypts files and locks users out of their systems, demanding payment to regain access. It doesn’t typically disable antivirus software in a stealthy way; instead, it announces itself.
❌ Spyware
Spyware monitors user activity and collects data, such as browsing habits and credentials. It may avoid detection, but it typically doesn't disable antivirus software at the system level like a rootkit does.
❌ Keylogger
A keylogger records keystrokes to capture sensitive information. It may run silently but is less likely to interfere with antivirus operations compared to a rootkit.
Question 6 Single Choice
Which of the following should be used to configure automatic backups on macOS?
Explanation

Click "Show Answer" to see the explanation here
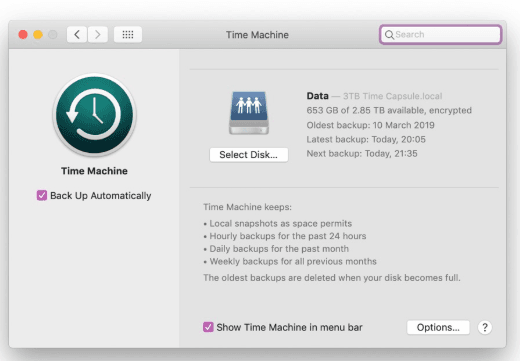
Time Machine
Time Machine is the built-in backup feature in macOS. It automatically backs up the entire system, including apps, music, photos, documents, and system files. You can easily restore the entire system or individual files from backups created with Time Machine. It also allows for scheduled automatic backups and can work with external drives or network locations.
❌ Other Options:
Mission Control
Mission Control is a macOS feature used for managing open windows, virtual desktops (Spaces), and full-screen apps. It has nothing to do with backups—its purpose is to improve multitasking and navigation.Disaster Recovery
This is a general IT term that refers to strategies for recovering systems after catastrophic failures. macOS doesn't have a tool named "Disaster Recovery." Backup tools like Time Machine may be part of a broader disaster recovery plan, but this is not the tool you’d select on a Mac.System Restore
System Restore is a feature in Windows, not macOS. It's used to roll back system files and settings to a previous state. macOS uses Time Machine instead.
Explanation
Time Machine
Time Machine is the built-in backup feature in macOS. It automatically backs up the entire system, including apps, music, photos, documents, and system files. You can easily restore the entire system or individual files from backups created with Time Machine. It also allows for scheduled automatic backups and can work with external drives or network locations.

❌ Other Options:
Mission Control
Mission Control is a macOS feature used for managing open windows, virtual desktops (Spaces), and full-screen apps. It has nothing to do with backups—its purpose is to improve multitasking and navigation.Disaster Recovery
This is a general IT term that refers to strategies for recovering systems after catastrophic failures. macOS doesn't have a tool named "Disaster Recovery." Backup tools like Time Machine may be part of a broader disaster recovery plan, but this is not the tool you’d select on a Mac.System Restore
System Restore is a feature in Windows, not macOS. It's used to roll back system files and settings to a previous state. macOS uses Time Machine instead.
Question 7 Single Choice
A customer reports that an Android phone will not allow the use of contactless electronic payment. Which of the following needs to be enabled to resolve the issue?
Explanation

Click "Show Answer" to see the explanation here
NFC (Near Field Communication) is the technology required for contactless electronic payments on Android phones (and iPhones). Services like Google Pay rely on NFC to communicate wirelessly with payment terminals by simply tapping or bringing the phone close to the reader. If NFC is disabled, the phone will not complete a tap-to-pay transaction.
To enable NFC on Android:
Go to Settings > Connected devices or Settings > Connection preferences
Tap NFC and toggle it on
❌ Other Options:
Wi-Fi
Wi-Fi is used for internet connectivity but is not needed for contactless payments. NFC works locally over a very short range and doesn’t require an internet connection during the transaction itself.Nearby Share
This is Android’s file-sharing feature, similar to Apple’s AirDrop. It uses Bluetooth and Wi-Fi Direct to share files between nearby devices—not used for payments.Bluetooth
Bluetooth enables wireless communication between devices like headphones or smartwatches. It is not used for contactless payments, and keeping it off does not affect payment features.
Explanation
NFC (Near Field Communication) is the technology required for contactless electronic payments on Android phones (and iPhones). Services like Google Pay rely on NFC to communicate wirelessly with payment terminals by simply tapping or bringing the phone close to the reader. If NFC is disabled, the phone will not complete a tap-to-pay transaction.
To enable NFC on Android:
Go to Settings > Connected devices or Settings > Connection preferences
Tap NFC and toggle it on
❌ Other Options:
Wi-Fi
Wi-Fi is used for internet connectivity but is not needed for contactless payments. NFC works locally over a very short range and doesn’t require an internet connection during the transaction itself.Nearby Share
This is Android’s file-sharing feature, similar to Apple’s AirDrop. It uses Bluetooth and Wi-Fi Direct to share files between nearby devices—not used for payments.Bluetooth
Bluetooth enables wireless communication between devices like headphones or smartwatches. It is not used for contactless payments, and keeping it off does not affect payment features.
Question 8 Single Choice
A user is unable to see transaction details on a website, and nothing happens when the user clicks the Details button.
Which of the following should the user do to fix this issue?
Explanation

Click "Show Answer" to see the explanation here
Disable the pop-up blocker
Many websites use pop-up windows to display transaction details, confirmations, or secondary content. If the browser’s pop-up blocker is enabled, it can silently block these windows from opening, making it seem like nothing happens when a button is clicked.
To fix this:
Go to your browser's settings (e.g., Chrome > Settings > Privacy & Security)
Look for Site Settings > Pop-ups and redirects
Allow pop-ups for the specific website
❌ Other Options Explained:
Clear the browser cache
This removes stored website files (like images or scripts) to fix loading/display issues. It helps if the page layout is broken or outdated data is causing problems, but not when pop-ups are blocked.Configure private browsing
This mode (also called Incognito) prevents the browser from saving history, cookies, or cached files. It’s useful for privacy but won’t solve issues related to blocked pop-ups or interactive buttons.Verify valid certificates
SSL certificates ensure a secure HTTPS connection. While an invalid certificate might block access to a whole website, it’s not related to a specific button failing to open details.
Explanation
Disable the pop-up blocker
Many websites use pop-up windows to display transaction details, confirmations, or secondary content. If the browser’s pop-up blocker is enabled, it can silently block these windows from opening, making it seem like nothing happens when a button is clicked.
To fix this:
Go to your browser's settings (e.g., Chrome > Settings > Privacy & Security)
Look for Site Settings > Pop-ups and redirects
Allow pop-ups for the specific website
❌ Other Options Explained:
Clear the browser cache
This removes stored website files (like images or scripts) to fix loading/display issues. It helps if the page layout is broken or outdated data is causing problems, but not when pop-ups are blocked.Configure private browsing
This mode (also called Incognito) prevents the browser from saving history, cookies, or cached files. It’s useful for privacy but won’t solve issues related to blocked pop-ups or interactive buttons.Verify valid certificates
SSL certificates ensure a secure HTTPS connection. While an invalid certificate might block access to a whole website, it’s not related to a specific button failing to open details.
Question 9 Single Choice
A security technician is reviewing options to monitor who enters restricted server rooms in a corporate building. The goal is to detect and log every individual who accesses the area.
Which of the following solutions should the technician implement?
Explanation

Click "Show Answer" to see the explanation here
Badge readers
Badge readers are access control devices that scan employee ID cards or badges to grant entry to secure locations.
They both detect and record who enters restricted areas, providing logs with timestamps and user identities—perfect for auditing access.
❌ Other Options Explained:
Bollards
These are physical barriers used to block vehicle access or protect buildings from collisions.
They do not detect or record who enters an area.Video surveillance
Cameras can monitor and visually record people entering an area, but they usually do not provide logs of individual identities unless used in conjunction with facial recognition or badge scans.Fence
A fence helps physically secure a perimeter, but it does not detect or track individual entries unless paired with other access controls.
Explanation
Badge readers
Badge readers are access control devices that scan employee ID cards or badges to grant entry to secure locations.
They both detect and record who enters restricted areas, providing logs with timestamps and user identities—perfect for auditing access.
❌ Other Options Explained:
Bollards
These are physical barriers used to block vehicle access or protect buildings from collisions.
They do not detect or record who enters an area.Video surveillance
Cameras can monitor and visually record people entering an area, but they usually do not provide logs of individual identities unless used in conjunction with facial recognition or badge scans.Fence
A fence helps physically secure a perimeter, but it does not detect or track individual entries unless paired with other access controls.
Question 10 Single Choice
A technician is trying to perform an in-place upgrade of a Windows operating system using a downloaded file. However, when the technician double-clicks the file, a prompt appears asking to mount a drive.
Which of the following file types did the technician most likely download?
Explanation

Click "Show Answer" to see the explanation here
.iso
An ISO file is a disk image file that contains the complete contents of a CD, DVD, or other disc.
To access the contents, the file must be mounted as a virtual drive or burned to physical media.
This is why Windows prompts the technician to mount the ISO before proceeding with the upgrade.
❌ Other Options Explained:
.msi
This is a Microsoft Installer file used to install applications, not operating systems. It runs directly—no need to mount anything..zip
A ZIP file is a compressed archive. It must be extracted (unzipped), but not mounted. ZIPs are often used to bundle documents or programs, not full OS images..exe
This is a Windows executable file. It is used to launch programs directly, including some OS installers. It would never require mounting.
Explanation
.iso
An ISO file is a disk image file that contains the complete contents of a CD, DVD, or other disc.
To access the contents, the file must be mounted as a virtual drive or burned to physical media.
This is why Windows prompts the technician to mount the ISO before proceeding with the upgrade.
❌ Other Options Explained:
.msi
This is a Microsoft Installer file used to install applications, not operating systems. It runs directly—no need to mount anything..zip
A ZIP file is a compressed archive. It must be extracted (unzipped), but not mounted. ZIPs are often used to bundle documents or programs, not full OS images..exe
This is a Windows executable file. It is used to launch programs directly, including some OS installers. It would never require mounting.