

CompTIA PenTest+ Certification - (PT0-003) Exam Questions
Question 11 Single Choice
Which technology allows devices to communicate when they are brought within close proximity, typically less than 4 inches (<10 centimeters)?
Question 12 Single Choice
During an assessment of a client's cloud-based services, you find that sensitive information, such as user credentials and personal data, is being stored in system logs. These can be exploited by attackers who gain access to these logs. What type of attack types does this scenario represent?
Question 13 Single Choice
A new piece of malware attempts to exfiltrate user data by hiding the traffic and sending it over a TLS-encrypted outbound traffic over random ports. What technology would be able to detect and block this type of traffic?
Question 14 Single Choice
Jake, a penetration tester, performs a lock-picking exercise at a client’s facility. He unlocks the main office door in less than two minutes using a standard lock-picking tool. What recommendation should Jake give to improve the physical security of the facility?
Question 15 Single Choice
You have completed your penetration test using cloud-based infrastructure for testing. What should be your next step in terms of managing this infrastructure?
Question 16 Single Choice
You have been asked to monitor any new devices that come online in a client's network that match a specific set of criteria related to their security configuration. Which feature in Shodan would you use to automate this process?
Question 17 Single Choice
Which of the following tools provides a penetration tester with PowerShell scripts that can maintain persistence and cover their tracks?
Question 18 Single Choice
What is the proper threat classification for a security breach that employs brute-force methods to compromise, degrade, or destroy systems?
Question 19 Single Choice
While conducting a penetration test against an organization, you gained access to the CEO's account. You log in as the CEO and send the following email:

Which of the following attacks are you utilizing in this scenario?
Question 20 Single Choice
You are reverse engineering a malware sample using the Strings tool when you notice the code inside appears to be obfuscated. You look at the following line of output on your screen:
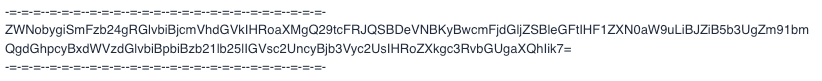
Based on the output above, which of the following methods do you believe the attacker used to prevent their malicious code from being easily read or analyzed?





