

CompTIA SecurityX Certification - (CAS-005) Exam Questions
Question 11 Single Choice
Which of the following features is supported by Kerberos but not by RADIUS?
Question 12 Single Choice
XYZ Training is concerned with the possibility of a data breach causing a financial loss to the company. After performing a risk analysis, the COO decides to purchase data breach insurance to protect the company from an incident. Which of the following best describes the company's risk response?
Question 13 Single Choice
You are configuring the ACL for the network perimeter firewall. You have just finished adding all the proper allow and deny rules. What should you place at the end of your ACL rules?
Question 14 Single Choice
Which of the following is used to maintain the overall integrity of a blockchain?
Question 15 Single Choice
XYZ Training is building a new video streaming service with support for digital encryption of the content. The development team needs to select a strong symmetric stream encryption cipher that operates well on both desktop and mobile devices. Which of the following algorithms should the development team select?
Question 16 Single Choice
You have been hired as a cybersecurity analyst for a privately-owned bank. Which of the following regulations would have the greatest impact on your bank's cybersecurity program?
Question 17 Single Choice
While conducting a security test to ensure that information about your company’s web server is protected from inadvertent disclosure, you request an HTML file from the webserver and receive the following output:
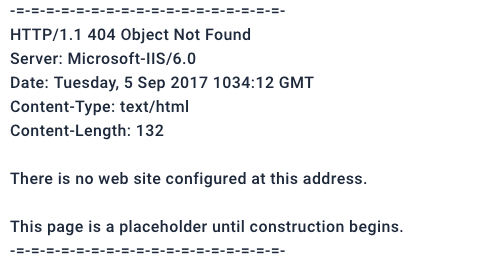
Which of the following actions should you take to remediate this vulnerability?
Question 18 Single Choice
What phase of the software development lifecycle is sometimes known as the acceptance, installation, and deployment phase?
Question 19 Single Choice
Which encryption type MOST likely is used for securing the key exchange during a client-to-server VPN connection?
Question 20 Single Choice
An organization implements a Domain-based Message Authentication, Reporting, and Conformance (DMARC) policy to prevent email spoofing. Despite the implementation, several phishing emails that appear to originate from the organization’s domain are being delivered to customers. A review of the DMARC settings shows the following configuration: Policy: None, SPF and DKIM alignment: Enabled, Reports: Enabled. What is the most likely cause of the phishing emails bypassing the DMARC protections?





