

Microsoft 365 Certified: Administrator Expert - (MS-102) Exam Questions
Question 11 Single Choice
As an administrator, you need to identify which users have..
Reset a user password
Removed site collection admin
Allowed users to create groups in Microsoft 365
Which Microsoft 365 functionality will you use?
Question 12 Single Choice
An organization has an on-premises Active Directory and its users are provisioned on Microsoft 365 to use Dynamics 365 Customer Engagement without Directory Synchronization.
The administrator now wants to configure Entra Connect to sync between On-Prem AD and Entra ID.
Which type of matching mechanism can be used initially to ensure that Entra Connect recognizes that they refer to the same user?
Question 13 Single Choice
An organization named GetCloudSkills.com has a Microsoft 365 tenant.
Unfortunately, malicious actors have targeted the organization, continuously sending phishing emails and documents to the managers.
The security department is closely monitoring all threats, and the company wants to use Microsoft 365 Defender to protect itself against these ongoing attacks.
What configuration option should be used to achieve this goal?
Question 14 Multiple Choice
GetCloudSkills has 500 Windows 11 devices protected using Microsoft Defender for Endpoint.
As the new security administrator, you have been tasked with reviewing all high-severity incidents that occurred in the last seven days.
Where should you navigate to within Microsoft 365 Defender to review these incidents?
Question 15 Single Choice
GetCloudSkills is an IT services company with 500 employees that operates globally.
Overview
The company has four offices in Germany located in Berlin, Hamburg, Frankfurt, and Manheim, and offers health services.
Current Infrastructure
GetCloudSkills has a domain name, getcloudskills.com, which is connected to Azure Active Directory through Entra Connect. The company recently purchased a Microsoft 365 subscription and utilizes the on-prem Quest syslog-ng Store box to collect system event logs. The syslog-ng Store Box is a high-performance, high-reliability log management appliance
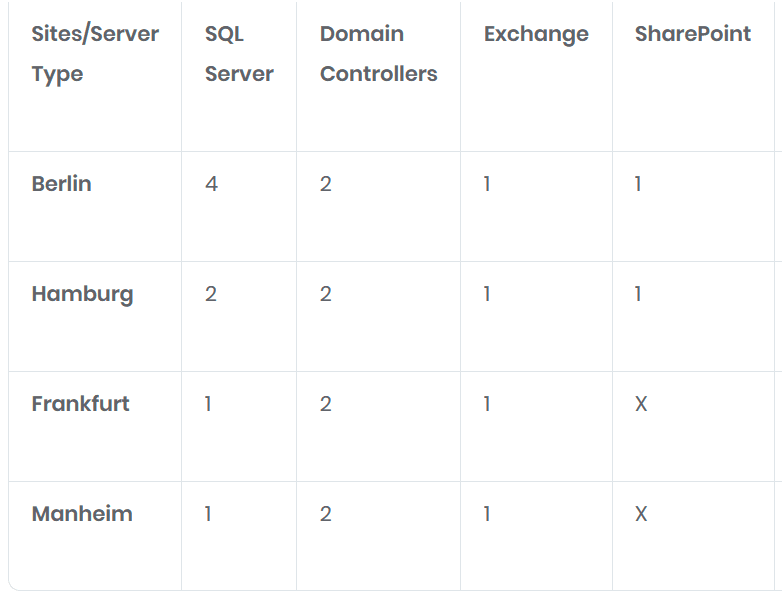
Business Goals
GetCloudSkills aims to effectively and affordably host their on-prem servers using Microsoft services.
Technical Requirements
A security administrator requires a report showing which Microsoft 365 users have signed in. Based on the report, the administrator will create a policy requiring multi-factor authentication when a sign-in is at high risk.
Aggregate the system event logs using Microsoft services. Aggregate the system event logs using Microsoft services
Compliance Requirements
The legal department must place a hold on all emails of a user named LeglJser1 for a period of 5 years.
Ensure that documents and email messages containing the Personal Identifiable Information (PII) data of European Union (EU) citizens are preserved for a period of 7 years.
A security administrator requires a report that shows which Microsoft 365 users last signed in.
Which of the following Microsoft Azure solutions will assist in achieving this goal?
Question 16 Single Choice
GetCloudSkills subscribes to Microsoft 365.
They aim to authenticate all incoming email senders to their organization.
Which Microsoft 365 Defender policy should they configure?
Question 17 Single Choice
GetCloudSkills is equipped with Microsoft Defender for Endpoint. As a SOC engineer, you seek ways to streamline security operations and automatically address most of the alerts associated with viruses and malware.
What configuration should you make in Microsoft Defender for Endpoint to achieve this?
Question 18 Multiple Choice
What threat management features are included in Exchange Online Protection (EOP) subscriptions?
Question 19 Single Choice
Your organization has a Microsoft 365 infrastructure.
You need to enable Microsoft Defender for Office 365 for SharePoint, OneDrive, and Microsoft Teams.
What type of Microsoft Defender for Office 365 policy should you configure?
Question 20 Single Choice
You are planning to deploy Microsoft Defender for Identity and install a standalone Microsoft Defender for Identity sensor on Server1.
What step should you take prior to using the Microsoft Defender for Identity sensor?




