

Microsoft Certified: Azure Network Engineer Associate - (AZ-700) Exam Questions
Total Questions
Last Updated
1st Try Guaranteed

Experts Verified
Question 1 Single Choice
Your company has a single on-premises datacenter in Washington DC. The East US Azure region has a peering location in Washington DC. The company only has Azure resources in the East US region.
You need to implement ExpressRoute to support up to 1 Gbps. You must use only ExpressRoute Unlimited data plans. The solution must minimize costs.
Which type of ExpressRoute circuits should you create?
Explanation

Click "Show Answer" to see the explanation here
Option A is CORRECT because ExpressRoute Local provides connectivity only within the region where the circuit is provisioned, and it costs less than other ExpressRoute offerings. In this case, since the company only has Azure resources in the East US region and there is a peering location in Washington DC, ExpressRoute Local will suffice to provide up to 1 Gbps connectivity. ExpressRoute Local also supports the Unlimited data plan which fulfills the requirement in the question.
Option B is INCORRECT because ExpressRoute Direct provides direct connectivity to Microsoft's network and is designed for massive data ingestion scenarios, where more than 10 Gbps of capacity is required. Since the requirement in the question is only up to 1 Gbps, ExpressRoute Direct is not needed and would not be cost-effective.
Option C is INCORRECT because ExpressRoute Premium offers increased route limits and global connectivity across Microsoft's network. Since the company only requires connectivity within the East US region, the additional cost for global connectivity and increased route limits of ExpressRoute Premium would not be justified.
Option D is INCORRECT because ExpressRoute Standard provides connectivity to all regions within a geopolitical region, which is more than the required connectivity to the East US region alone. So, using ExpressRoute Standard would increase the costs unnecessarily.
Reference links:
Explanation
Option A is CORRECT because ExpressRoute Local provides connectivity only within the region where the circuit is provisioned, and it costs less than other ExpressRoute offerings. In this case, since the company only has Azure resources in the East US region and there is a peering location in Washington DC, ExpressRoute Local will suffice to provide up to 1 Gbps connectivity. ExpressRoute Local also supports the Unlimited data plan which fulfills the requirement in the question.
Option B is INCORRECT because ExpressRoute Direct provides direct connectivity to Microsoft's network and is designed for massive data ingestion scenarios, where more than 10 Gbps of capacity is required. Since the requirement in the question is only up to 1 Gbps, ExpressRoute Direct is not needed and would not be cost-effective.
Option C is INCORRECT because ExpressRoute Premium offers increased route limits and global connectivity across Microsoft's network. Since the company only requires connectivity within the East US region, the additional cost for global connectivity and increased route limits of ExpressRoute Premium would not be justified.
Option D is INCORRECT because ExpressRoute Standard provides connectivity to all regions within a geopolitical region, which is more than the required connectivity to the East US region alone. So, using ExpressRoute Standard would increase the costs unnecessarily.
Reference links:
Question 2 Single Choice
You are planning an Azure Point-to-Site (P2S) VPN that will use OpenVPN. Users will authenticate by an on-premises Active Directory domain.
Which additional service should you deploy to support the VPN authentication?
Explanation

Click "Show Answer" to see the explanation here
Option B is CORRECT because a RADIUS server is required to integrate Point-to-Site (P2S) VPN with on-premises Active Directory for authentication. Azure VPN Gateway can integrate with RADIUS servers and use RADIUS to authenticate connections to the VPN. This setup is commonly used when an organization already uses RADIUS for other remote access solutions and wants to leverage the same for Azure P2S VPN.
Option A is INCORRECT because Azure Key Vault is a service for securely storing and accessing secrets, keys, and certificates. It doesn't provide authentication services for VPNs.
Option C is INCORRECT because a Certification Authority (CA) issues digital certificates for use by other parties. While a CA can be used for VPN authentication, in the scenario described in the question, users will be authenticated by an on-premises Active Directory domain, not by certificates.
Option D is INCORRECT because Azure AD Application Proxy is a service that allows users to access on-premises web applications from a remote client. It is not used for VPN authentication.
Reference links:
https://docs.microsoft.com/en-us/azure/vpn-gateway/openvpn-azure-ad-radius
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-howto-radius-vs
https://docs.microsoft.com/en-us/azure/key-vault/general/overview
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/application-proxy
Explanation
Option B is CORRECT because a RADIUS server is required to integrate Point-to-Site (P2S) VPN with on-premises Active Directory for authentication. Azure VPN Gateway can integrate with RADIUS servers and use RADIUS to authenticate connections to the VPN. This setup is commonly used when an organization already uses RADIUS for other remote access solutions and wants to leverage the same for Azure P2S VPN.
Option A is INCORRECT because Azure Key Vault is a service for securely storing and accessing secrets, keys, and certificates. It doesn't provide authentication services for VPNs.
Option C is INCORRECT because a Certification Authority (CA) issues digital certificates for use by other parties. While a CA can be used for VPN authentication, in the scenario described in the question, users will be authenticated by an on-premises Active Directory domain, not by certificates.
Option D is INCORRECT because Azure AD Application Proxy is a service that allows users to access on-premises web applications from a remote client. It is not used for VPN authentication.
Reference links:
https://docs.microsoft.com/en-us/azure/vpn-gateway/openvpn-azure-ad-radius
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-howto-radius-vs
https://docs.microsoft.com/en-us/azure/key-vault/general/overview
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/application-proxy
Question 3 Multiple Choice
You plan to configure BGP for a Site-to-Site VPN connection between a datacenter and Azure.
Which two Azure resources should you configure?
Explanation

Click "Show Answer" to see the explanation here
Option A is CORRECT because a virtual network gateway is a fundamental Azure resource necessary for configuring Site-to-Site VPN connections. It is the Azure side of the VPN connection, and it must be configured to use BGP (Border Gateway Protocol) to exchange routes with the on-premises network.
Option D is CORRECT because a local network gateway is another fundamental Azure resource necessary for configuring Site-to-Site VPN connections. The local network gateway represents the on-premises side of the VPN connection and is where the BGP settings (such as the BGP peer IP address and Autonomous System Number) for the on-premises network are specified.
Option B is INCORRECT because Azure Application Gateway is a web traffic load balancer that enables you to manage traffic to your web applications, not a resource for configuring Site-to-Site VPN connections or BGP.
Option C is INCORRECT because Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. It's not involved in the configuration of Site-to-Site VPN connections or BGP.
Option E is INCORRECT because Azure Front Door is a service that provides caching and fast network latency for global applications, but it doesn't play a role in setting up Site-to-Site VPN connections or BGP.
Reference links:
Explanation
Option A is CORRECT because a virtual network gateway is a fundamental Azure resource necessary for configuring Site-to-Site VPN connections. It is the Azure side of the VPN connection, and it must be configured to use BGP (Border Gateway Protocol) to exchange routes with the on-premises network.
Option D is CORRECT because a local network gateway is another fundamental Azure resource necessary for configuring Site-to-Site VPN connections. The local network gateway represents the on-premises side of the VPN connection and is where the BGP settings (such as the BGP peer IP address and Autonomous System Number) for the on-premises network are specified.
Option B is INCORRECT because Azure Application Gateway is a web traffic load balancer that enables you to manage traffic to your web applications, not a resource for configuring Site-to-Site VPN connections or BGP.
Option C is INCORRECT because Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. It's not involved in the configuration of Site-to-Site VPN connections or BGP.
Option E is INCORRECT because Azure Front Door is a service that provides caching and fast network latency for global applications, but it doesn't play a role in setting up Site-to-Site VPN connections or BGP.
Reference links:
Question 4 Single Choice
You fail to establish a Site-to-Site VPN connection between your company's main office and an Azure virtual network.
You need to troubleshoot what prevents you from establishing the IPsec tunnel.
Which diagnostic log should you review?
Explanation

Click "Show Answer" to see the explanation here
Option A is CORRECT because the IKE (Internet Key Exchange) Diagnostic Log is used to troubleshoot issues with the IPsec tunnel establishment in a Site-to-Site VPN connection. IKE is the protocol used to set up a security association in the IPsec protocol suite, and if there's a problem establishing the tunnel, the IKE Diagnostic Log will have relevant information.
Option B is INCORRECT because the Route Diagnostic Log is used to troubleshoot routing issues. While it can be helpful in other scenarios, it is not specifically used for troubleshooting IPsec tunnel establishment problems.
Option C is INCORRECT because the Gateway Diagnostic Log provides information about the health and status of a VPN gateway, but it is not specifically used for troubleshooting issues with IPsec tunnel establishment.
Option D is INCORRECT because there is no specific log named TunnelDiagnosticLog in Azure for troubleshooting Site-to-Site VPN connections.
Reference links:
Explanation
Option A is CORRECT because the IKE (Internet Key Exchange) Diagnostic Log is used to troubleshoot issues with the IPsec tunnel establishment in a Site-to-Site VPN connection. IKE is the protocol used to set up a security association in the IPsec protocol suite, and if there's a problem establishing the tunnel, the IKE Diagnostic Log will have relevant information.
Option B is INCORRECT because the Route Diagnostic Log is used to troubleshoot routing issues. While it can be helpful in other scenarios, it is not specifically used for troubleshooting IPsec tunnel establishment problems.
Option C is INCORRECT because the Gateway Diagnostic Log provides information about the health and status of a VPN gateway, but it is not specifically used for troubleshooting issues with IPsec tunnel establishment.
Option D is INCORRECT because there is no specific log named TunnelDiagnosticLog in Azure for troubleshooting Site-to-Site VPN connections.
Reference links:
Question 5 Multiple Choice
You have an Azure virtual network and an on-premises datacenter. You are planning a Site-to-Site VPN connection between the datacenter and the virtual network.
Which two resources should you include in your plan?
Explanation

Click "Show Answer" to see the explanation here
Option B is CORRECT because a virtual network gateway is a fundamental component when creating a Site-to-Site VPN connection in Azure. This gateway provides a connection point for the VPN connection on the Azure side.
Option G is CORRECT because a local network gateway is also a key resource when establishing a Site-to-Site VPN connection. The local network gateway defines the on-premises VPN device and network that Azure VPN gateway will connect to.
Option A is INCORRECT because a user-defined route is not a necessary resource for establishing a Site-to-Site VPN connection. User-defined routes can be used to customize routing in Azure, but they are not required for a basic VPN setup.
Option C is INCORRECT because Azure Firewall is a managed, cloud-based network security service to protect your Azure Virtual Network resources. It isn't a component required for establishing a Site-to-Site VPN connection.
Option D is INCORRECT because Azure Web Application Firewall (WAF) is a feature of Azure Application Gateway and provides centralized protection of your web applications from common exploits and vulnerabilities. It's not involved in the configuration of Site-to-Site VPN connections.
Option E is INCORRECT because an on-premises data gateway is used to provide quick and secure data transfer between on-premises data (data that is not in the cloud) and the Power BI, Microsoft Flow, Logic Apps, and PowerApps services. It's not involved in establishing a Site-to-Site VPN connection.
Option F is INCORRECT because an Azure application gateway provides application-level routing and load balancing services that let you build a scalable and highly-available web front end in Azure. It isn't a component required for establishing a Site-to-Site VPN connection.
Reference links:
Explanation
Option B is CORRECT because a virtual network gateway is a fundamental component when creating a Site-to-Site VPN connection in Azure. This gateway provides a connection point for the VPN connection on the Azure side.
Option G is CORRECT because a local network gateway is also a key resource when establishing a Site-to-Site VPN connection. The local network gateway defines the on-premises VPN device and network that Azure VPN gateway will connect to.
Option A is INCORRECT because a user-defined route is not a necessary resource for establishing a Site-to-Site VPN connection. User-defined routes can be used to customize routing in Azure, but they are not required for a basic VPN setup.
Option C is INCORRECT because Azure Firewall is a managed, cloud-based network security service to protect your Azure Virtual Network resources. It isn't a component required for establishing a Site-to-Site VPN connection.
Option D is INCORRECT because Azure Web Application Firewall (WAF) is a feature of Azure Application Gateway and provides centralized protection of your web applications from common exploits and vulnerabilities. It's not involved in the configuration of Site-to-Site VPN connections.
Option E is INCORRECT because an on-premises data gateway is used to provide quick and secure data transfer between on-premises data (data that is not in the cloud) and the Power BI, Microsoft Flow, Logic Apps, and PowerApps services. It's not involved in establishing a Site-to-Site VPN connection.
Option F is INCORRECT because an Azure application gateway provides application-level routing and load balancing services that let you build a scalable and highly-available web front end in Azure. It isn't a component required for establishing a Site-to-Site VPN connection.
Reference links:
Question 6 Single Choice
You need to connect an on-premises network and an Azure environment. The solution must use ExpressRoute and support failing over to a Site-to-Site VPN connection if there is an ExpressRoute failure.
Which routing type should you configure?
Explanation

Click "Show Answer" to see the explanation here
Option B is CORRECT because a Route-based VPN is required when setting up a Site-to-Site VPN as a backup for an ExpressRoute circuit. Route-based VPNs utilize Virtual Network Gateways with VPN tunnel interfaces on which routes can be configured. In a failover scenario where the ExpressRoute connection goes down, the traffic will be automatically rerouted through the Site-to-Site VPN because of the dynamic routing capability of the Route-based VPN.
Option A is INCORRECT because Policy-based routing makes routing decisions based on policies set by the network administrator. It does not support the dynamic routing required for the failover from ExpressRoute to Site-to-Site VPN.
Option C is INCORRECT because Static routing, where routes are manually set and do not change, does not provide the dynamic rerouting capability required for automatic failover from ExpressRoute to Site-to-Site VPN.
Reference links:
Explanation
Option B is CORRECT because a Route-based VPN is required when setting up a Site-to-Site VPN as a backup for an ExpressRoute circuit. Route-based VPNs utilize Virtual Network Gateways with VPN tunnel interfaces on which routes can be configured. In a failover scenario where the ExpressRoute connection goes down, the traffic will be automatically rerouted through the Site-to-Site VPN because of the dynamic routing capability of the Route-based VPN.
Option A is INCORRECT because Policy-based routing makes routing decisions based on policies set by the network administrator. It does not support the dynamic routing required for the failover from ExpressRoute to Site-to-Site VPN.
Option C is INCORRECT because Static routing, where routes are manually set and do not change, does not provide the dynamic rerouting capability required for automatic failover from ExpressRoute to Site-to-Site VPN.
Reference links:
Question 7 Single Choice
You need to connect an on-premises network and an Azure environment. The solution must use ExpressRoute and support failing over to a Site-to-Site VPN connection if there is an ExpressRoute failure.
How many virtual network gateways should you configure?
Explanation

Click "Show Answer" to see the explanation here
Option B is CORRECT
To achieve this architecture you need to configure two virtual network gateways.
An ExpressRoute gateway: This is needed to create the primary connection from your Azure environment to your on-premises network using ExpressRoute.
A VPN gateway: This is needed to create the secondary connection from your Azure environment to your on-premises network us
Thus, two virtual network gateways should be configured.
Reference links:
Explanation
Option B is CORRECT
To achieve this architecture you need to configure two virtual network gateways.
An ExpressRoute gateway: This is needed to create the primary connection from your Azure environment to your on-premises network using ExpressRoute.
A VPN gateway: This is needed to create the secondary connection from your Azure environment to your on-premises network us
Thus, two virtual network gateways should be configured.
Reference links:
Question 8 Single Choice
Your company has an on-premises network and three Azure subscriptions named Subscription1, Subscription2, and Subscription3.
The departments at the company use the Azure subscriptions as shown in the following table.
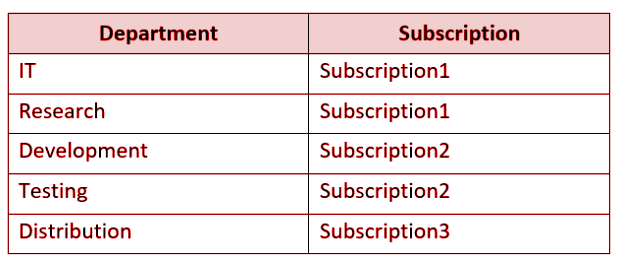
All the resources in the subscriptions are in either the West US Azure region or the West US 2 Azure region.
You plan to connect all the subscriptions to the on-premises network by using ExpressRoute.
What is the minimum number of ExpressRoute circuits required?
Explanation

Click "Show Answer" to see the explanation here
Option A is CORRECT because one ExpressRoute circuit is enough to connect multiple Azure subscriptions to an on-premises network. It doesn't matter if the subscriptions are being used by different departments or if the resources are in different Azure regions. As long as the subscriptions are part of the same Azure Active Directory tenant, a single ExpressRoute circuit can be used to connect all of them to the on-premises network.
Option B, Option C, Option D, and Option E are INCORRECT because the number of subscriptions, departments, or regions doesn't determine the number of ExpressRoute circuits required. The key factor here is the Azure Active Directory tenant. An ExpressRoute circuit connects your on-premises network to the Microsoft cloud through a connectivity provider. You can use one ExpressRoute circuit to connect your on-premises network to multiple subscriptions in the Microsoft cloud if they are under the same Azure Active Directory tenant.
Reference links:
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-introduction
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-faqs
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-troubleshooting-expressroute-link
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-locations-providers
Explanation
Option A is CORRECT because one ExpressRoute circuit is enough to connect multiple Azure subscriptions to an on-premises network. It doesn't matter if the subscriptions are being used by different departments or if the resources are in different Azure regions. As long as the subscriptions are part of the same Azure Active Directory tenant, a single ExpressRoute circuit can be used to connect all of them to the on-premises network.
Option B, Option C, Option D, and Option E are INCORRECT because the number of subscriptions, departments, or regions doesn't determine the number of ExpressRoute circuits required. The key factor here is the Azure Active Directory tenant. An ExpressRoute circuit connects your on-premises network to the Microsoft cloud through a connectivity provider. You can use one ExpressRoute circuit to connect your on-premises network to multiple subscriptions in the Microsoft cloud if they are under the same Azure Active Directory tenant.
Reference links:
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-introduction
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-faqs
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-troubleshooting-expressroute-link
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-locations-providers
Question 9 Single Choice
Your company has offices in New York and Amsterdam. The company has an Azure subscription. Both offices connect to Azure by using a Site-to-Site VPN connection. The office in Amsterdam uses resources in the North Europe Azure region. The office in New York uses resources in the East US Azure region.
You need to implement ExpressRoute circuits to connect each office to the nearest Azure region. Once the ExpressRoute circuits are connected, the on-premises computers in the Amsterdam office must be able to connect to the on-premises servers in the New York office by using the ExpressRoute circuits.
Which ExpressRoute option should you use?
Explanation

Click "Show Answer" to see the explanation here
Option B is CORRECT because it is designed to connect on-premises networks via Microsoft's network. It extends the functionality of ExpressRoute to allow any two networks connected to Microsoft through ExpressRoute to talk to each other, which fits the scenario of the Amsterdam office needing to connect to the New York office using ExpressRoute circuits.
Option A is INCORRECT because it is designed to optimize data flow between Azure datacenters and customer networks, not to directly connect two on-premises networks.
Option C is INCORRECT because it is designed to provide direct physical connections to Microsoft's network. This option does not enable direct connectivity between two on-premises networks.
Option D is INCORRECT because it provides cost-effective data ingress and egress at the same location. It does not enable direct connectivity between two on-premises networks.
Reference links:
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-global-reach
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-introduction
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-direct
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-faqs
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-locations-providers
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-optimize-routing
Explanation
Option B is CORRECT because it is designed to connect on-premises networks via Microsoft's network. It extends the functionality of ExpressRoute to allow any two networks connected to Microsoft through ExpressRoute to talk to each other, which fits the scenario of the Amsterdam office needing to connect to the New York office using ExpressRoute circuits.
Option A is INCORRECT because it is designed to optimize data flow between Azure datacenters and customer networks, not to directly connect two on-premises networks.
Option C is INCORRECT because it is designed to provide direct physical connections to Microsoft's network. This option does not enable direct connectivity between two on-premises networks.
Option D is INCORRECT because it provides cost-effective data ingress and egress at the same location. It does not enable direct connectivity between two on-premises networks.
Reference links:
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-global-reach
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-introduction
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-direct
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-faqs
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-locations-providers
https://docs.microsoft.com/en-us/azure/expressroute/expressroute-optimize-routing
Question 10 Single Choice
You have an Azure subscription that contains a single virtual network and a virtual network gateway.
You need to ensure that administrators can use Point-to-Site (P2S) VPN connections to access resources in the virtual network. The connections must be authenticated by Azure Active Directory (Azure AD).
What should you configure for Azure AD ?
Explanation

Click "Show Answer" to see the explanation here
Option C is CORRECT because Azure AD authentication for Point-to-Site (P2S) VPN connections requires an Azure AD tenant and an enterprise application in Azure AD. The enterprise application is used to manage the authorization to the VPN gateway.
Option A is INCORRECT because it is a part of Azure AD entitlement management and is used to manage access to groups, applications, and SharePoint Online sites. It's not used for managing authentication for P2S VPN connections.
Option B is INCORRECT because it is used to enforce controls on the access to apps in your environment based on specific conditions from a user’s location or device state, among other factors. It is not directly related to setting up P2S VPN connections.
Option D is INCORRECT because while certificates are required for certificate-based authentication for P2S VPN connections, they are not related to Azure AD authentication.
Reference links:
https://docs.microsoft.com/en-us/azure/vpn-gateway/openvpn-azure-ad-tenant
https://docs.microsoft.com/en-us/azure/vpn-gateway/openvpn-azure-ad-authorization
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-certificates-point-to-site
Explanation
Option C is CORRECT because Azure AD authentication for Point-to-Site (P2S) VPN connections requires an Azure AD tenant and an enterprise application in Azure AD. The enterprise application is used to manage the authorization to the VPN gateway.
Option A is INCORRECT because it is a part of Azure AD entitlement management and is used to manage access to groups, applications, and SharePoint Online sites. It's not used for managing authentication for P2S VPN connections.
Option B is INCORRECT because it is used to enforce controls on the access to apps in your environment based on specific conditions from a user’s location or device state, among other factors. It is not directly related to setting up P2S VPN connections.
Option D is INCORRECT because while certificates are required for certificate-based authentication for P2S VPN connections, they are not related to Azure AD authentication.
Reference links:
https://docs.microsoft.com/en-us/azure/vpn-gateway/openvpn-azure-ad-tenant
https://docs.microsoft.com/en-us/azure/vpn-gateway/openvpn-azure-ad-authorization
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-certificates-point-to-site



