

Microsoft Certified: Azure Solutions Architect Expert - (AZ-305) Exam Questions
Total Questions
Last Updated
1st Try Guaranteed

Experts Verified
Question 11 Single Choice
You have an Azure subscription that contains the resources shown in the following table:
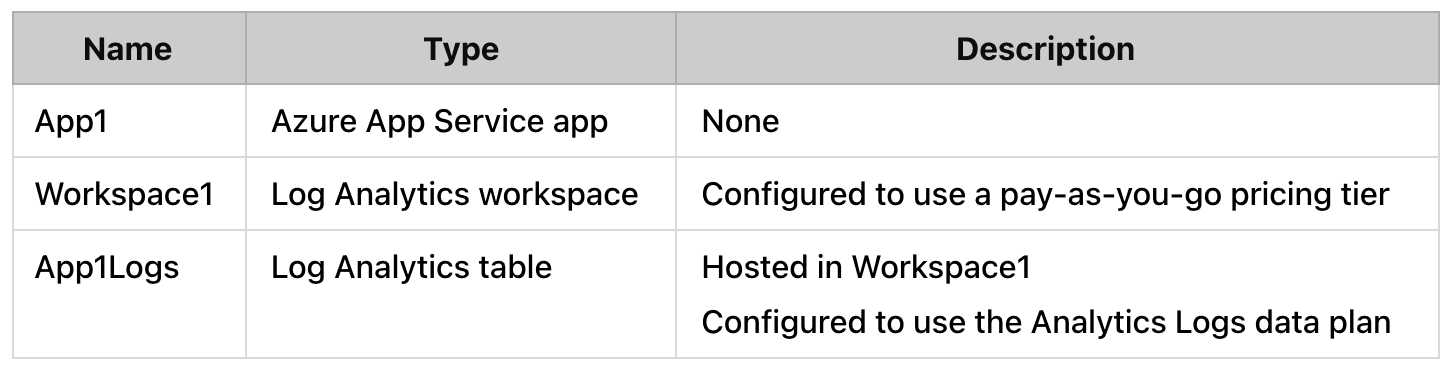
Log files from App1 are registered to App1Logs. An average of 120 GB of log data is ingested per day.
You configure an Azure Monitor alert that will be triggered if the App1 logs contain error messages.
You need to minimize the Log Analytics costs associated with App1. The solution must meet the following requirements:
Ensure that all the log files from App1 are ingested to App1 Logs.
Minimize the impact on the Azure Monitor alert.
Which modification should you perform?
Explanation

Click "Show Answer" to see the explanation here
Change to a commitment pricing tier is correct. Choosing a commitment pricing tier in Log Analytics offers a strategic approach to optimize costs and ensure effective monitoring for App1. By choosing this approach, it can save up to 30% compared to the pay-as-you-go model. This is advantageous when you have a consistent amount of data, like dealing with around 120 GB of log data daily. The commitment spans 31 days, offering you stable and predictable cost planning. This strategy ensures that all log files from App1 are organized into App1Logs, aligning perfectly with the goal of keeping Log Analytics costs to minimum.
Change to the Basic Logs data plan is incorrect. Opting for the Basic Logs data plan is a targeted solution designed to reduce costs associated with ingesting and storing high-volume verbose logs. This plan is basically used for scenarios involving debugging, troubleshooting, and auditing purposes. Also, the cost of searching through Basic Logs is based on how much data you search. While it offers cost-effectiveness for specific use cases, it may not provide the same level of overall cost savings as a commitment pricing tier. However, it might not be the most suitable option for analytics and alerts, and also it could impact the monitoring of the system.
Set a daily cap is incorrect. While setting a daily cap is a common method to control costs in Log Analytics, its suitability depends on the specific needs. In scenarios where the goal is to ingest all log files into a workspace like App1Logs while minimizing the impact on Azure Monitor alerts for error messages, using a daily cap might give challenges. There's a risk of incomplete logging or data loss when the cap is reached, especially when dealing with a consistent daily log data volume. And every workspace has its own daily limit for the amount of data it can handle. When this cap is reached, a warning banner appears in the Azure portal, and an operation event is sent to the Operation table. You can choose to create an alert rule to notify you when this event occurs. However, because error messages can be unpredictable, and a daily cap might impact the Azure Monitor alerting system, alternative solutions, such as Change to a commitment pricing tier plan, could be more effective.
Read More:
Explanation
Change to a commitment pricing tier is correct. Choosing a commitment pricing tier in Log Analytics offers a strategic approach to optimize costs and ensure effective monitoring for App1. By choosing this approach, it can save up to 30% compared to the pay-as-you-go model. This is advantageous when you have a consistent amount of data, like dealing with around 120 GB of log data daily. The commitment spans 31 days, offering you stable and predictable cost planning. This strategy ensures that all log files from App1 are organized into App1Logs, aligning perfectly with the goal of keeping Log Analytics costs to minimum.
Change to the Basic Logs data plan is incorrect. Opting for the Basic Logs data plan is a targeted solution designed to reduce costs associated with ingesting and storing high-volume verbose logs. This plan is basically used for scenarios involving debugging, troubleshooting, and auditing purposes. Also, the cost of searching through Basic Logs is based on how much data you search. While it offers cost-effectiveness for specific use cases, it may not provide the same level of overall cost savings as a commitment pricing tier. However, it might not be the most suitable option for analytics and alerts, and also it could impact the monitoring of the system.
Set a daily cap is incorrect. While setting a daily cap is a common method to control costs in Log Analytics, its suitability depends on the specific needs. In scenarios where the goal is to ingest all log files into a workspace like App1Logs while minimizing the impact on Azure Monitor alerts for error messages, using a daily cap might give challenges. There's a risk of incomplete logging or data loss when the cap is reached, especially when dealing with a consistent daily log data volume. And every workspace has its own daily limit for the amount of data it can handle. When this cap is reached, a warning banner appears in the Azure portal, and an operation event is sent to the Operation table. You can choose to create an alert rule to notify you when this event occurs. However, because error messages can be unpredictable, and a daily cap might impact the Azure Monitor alerting system, alternative solutions, such as Change to a commitment pricing tier plan, could be more effective.
Read More:
Question 12 Multiple Choice
You have 12 Azure subscriptions and three projects. Each project uses resources across multiple subscriptions.
You need to use Microsoft Cost Management to monitor costs on a per project basis. The solution must minimize administrative effort.
Which two components should you include in the solution?
Explanation

Click "Show Answer" to see the explanation here
Budgets is correct. Azure Budgets serve as a valuable tool for monitoring costs in a project. With Azure Budgets, you can set project-specific spending thresholds for each project, enabling proactive cost management. When spending approaches or exceeds the defined limits, Azure Budgets send alerts, enabling timely interventions. It helps in controlling and managing costs for individual projects without the need for constant manual monitoring. In general, Azure Budgets is a user-friendly solution designed for efficient tracking, managing the costs and it is well-suited for per-project monitoring scenarios.
Resource Tags is correct. Azure resource tags is a key-value pair that helps in labeling the resources, allowing users to categorize resources based on attributes like projects. By assigning tags such as ProjectA or ProjectB organizations can logically group resources, providing structure to their projects. Tags enables users to define their tags based on project needs, like environment or department. Crucially, tags play a vital role in cost allocation, enabling users to filter or group costs based on applied tags when viewing reports or setting up budgets. It also simplifies automation, especially in policy enforcement, ensuring consistent standards across management tasks. Azure resource tags serve as tools for efficient organization, categorization, and cost management and have a maximum of 50 tags, including resources, resource groups, and subscriptions.
*Tag names are case-insensitive for operations. A tag with a tag name, regardless of the casing, is updated or retrieved, on the other hand Tag values are case-sensitive.
Custom role-based access control (RBAC) roles is incorrect. When considering the goal of monitoring costs on a per-project basis with minimal administrative effort across 12 Azure subscriptions and three projects, Azure RBAC may not be the most direct solution to achieve this specific goal with minimal administrative effort. While Azure RBAC excels in managing access to Azure resources by defining who can perform specific actions and where, it primarily focuses on authorization rather than specialized cost monitoring.To illustrate, suppose an organization aims to monitor costs for distinct projects. In this scenario, using resource tags and Azure Cost Management features provides a more straightforward approach. Resource tagging allows for categorizing resources based on projects, while Azure Cost Management enables creating custom reports and views specific to each project.For instance, project managers can be assigned the "Cost Contributor" role or a custom role designed for cost analysis at the resource group level. This ensures that they have the necessary access to cost-related information without granting unnecessary permissions for resource management.
Management Groups is incorrect. Management Groups in Azure offer a structured approach to organize and govern subscriptions, primarily focusing on governance, policy enforcement, and compliance standards. However, when it comes to in-depth cost monitoring, especially for per-project management, Management Groups might not be the most suitable choice. They are suitable in applying policies and access controls across subscriptions rather than providing the granular, alert-driven cost monitoring capabilities essential for detailed project-level cost management. Opting for Management Groups for cost-related tasks could involve more manual effort and may lack the real-time alerts crucial for effective cost control at the project level. In essence, while Management Groups excel in governance and policy enforcement across subscriptions, they may not be the optimal solution for the specific and alert-driven cost monitoring needs of this scenario.
Azure Boardsis incorrect. Azure Boards is a web-based service primarily focused on agile methods, work tracking, and collaborative discussions throughout the development process. It supports agile methodologies like Scrum and Kanban, and it is primarily used in work item management. Azure Boards is effective at tasks related to tracking work items, user stories, and project planning; however, it lacks direct features for comprehensive cost management and financial monitoring. Teams can customize their work items within Azure Boards, promoting effective collaboration and optimizing workflow efficiency. It's important to note that Azure Boards may not be directly suitable for financial monitoring or cost analysis. For the specific requirement of monitoring costs on a per-project basis with minimal administrative effort, using cost management tools like Azure Cost Management would be more suitable. These tools provide necessary financial information and budgeting capabilities aligning with the specified cost-monitoring objective.
Read More:
Explanation
Budgets is correct. Azure Budgets serve as a valuable tool for monitoring costs in a project. With Azure Budgets, you can set project-specific spending thresholds for each project, enabling proactive cost management. When spending approaches or exceeds the defined limits, Azure Budgets send alerts, enabling timely interventions. It helps in controlling and managing costs for individual projects without the need for constant manual monitoring. In general, Azure Budgets is a user-friendly solution designed for efficient tracking, managing the costs and it is well-suited for per-project monitoring scenarios.
Resource Tags is correct. Azure resource tags is a key-value pair that helps in labeling the resources, allowing users to categorize resources based on attributes like projects. By assigning tags such as ProjectA or ProjectB organizations can logically group resources, providing structure to their projects. Tags enables users to define their tags based on project needs, like environment or department. Crucially, tags play a vital role in cost allocation, enabling users to filter or group costs based on applied tags when viewing reports or setting up budgets. It also simplifies automation, especially in policy enforcement, ensuring consistent standards across management tasks. Azure resource tags serve as tools for efficient organization, categorization, and cost management and have a maximum of 50 tags, including resources, resource groups, and subscriptions.
*Tag names are case-insensitive for operations. A tag with a tag name, regardless of the casing, is updated or retrieved, on the other hand Tag values are case-sensitive.
Custom role-based access control (RBAC) roles is incorrect. When considering the goal of monitoring costs on a per-project basis with minimal administrative effort across 12 Azure subscriptions and three projects, Azure RBAC may not be the most direct solution to achieve this specific goal with minimal administrative effort. While Azure RBAC excels in managing access to Azure resources by defining who can perform specific actions and where, it primarily focuses on authorization rather than specialized cost monitoring.To illustrate, suppose an organization aims to monitor costs for distinct projects. In this scenario, using resource tags and Azure Cost Management features provides a more straightforward approach. Resource tagging allows for categorizing resources based on projects, while Azure Cost Management enables creating custom reports and views specific to each project.For instance, project managers can be assigned the "Cost Contributor" role or a custom role designed for cost analysis at the resource group level. This ensures that they have the necessary access to cost-related information without granting unnecessary permissions for resource management.
Management Groups is incorrect. Management Groups in Azure offer a structured approach to organize and govern subscriptions, primarily focusing on governance, policy enforcement, and compliance standards. However, when it comes to in-depth cost monitoring, especially for per-project management, Management Groups might not be the most suitable choice. They are suitable in applying policies and access controls across subscriptions rather than providing the granular, alert-driven cost monitoring capabilities essential for detailed project-level cost management. Opting for Management Groups for cost-related tasks could involve more manual effort and may lack the real-time alerts crucial for effective cost control at the project level. In essence, while Management Groups excel in governance and policy enforcement across subscriptions, they may not be the optimal solution for the specific and alert-driven cost monitoring needs of this scenario.
Azure Boardsis incorrect. Azure Boards is a web-based service primarily focused on agile methods, work tracking, and collaborative discussions throughout the development process. It supports agile methodologies like Scrum and Kanban, and it is primarily used in work item management. Azure Boards is effective at tasks related to tracking work items, user stories, and project planning; however, it lacks direct features for comprehensive cost management and financial monitoring. Teams can customize their work items within Azure Boards, promoting effective collaboration and optimizing workflow efficiency. It's important to note that Azure Boards may not be directly suitable for financial monitoring or cost analysis. For the specific requirement of monitoring costs on a per-project basis with minimal administrative effort, using cost management tools like Azure Cost Management would be more suitable. These tools provide necessary financial information and budgeting capabilities aligning with the specified cost-monitoring objective.
Read More:
Question 13 Single Choice
You have an Azure subscription. The subscription contains a tiered app named App1 that is distributed across multiple containers hosted in Azure Container Instances.
You need to deploy an Azure Monitor monitoring solution for the App. The solution must meet the following requirements:
Support using synthetic transaction monitoring to monitor traffic between the App1 components.
Minimize development effort.
What should you include in the solution?
Explanation

Click "Show Answer" to see the explanation here
Application Insights is correct. In the given question where an Azure Monitor monitoring solution is required for an application distributed across multiple containers in Azure Container Instances, choosing Application Insights is best. Application Insights support Synthetic Transaction Monitoring (STM), allows developers to proactively measure and test the performance, functionality, and user interaction experience of the application.It uses automated scripts for synthetic monitoring, this method, also known as active monitoring, simulates real user actions to identify and address issues related to website availability and performance before they impact end users. By simulating user interactions, STM ensures that critical paths within the application are functioning correctly, it allows early detection of issues and addressing performance.Therefore, for the given scenario, including Application Insights in the monitoring solution not only supports Synthetic Transaction Monitoring but also aligns with the goal of minimizing development effort by providing a comprehensive and integrated monitoring solution.
Network insights is incorrect. Network Insights in Azure Monitor primarily focus on monitoring network performance, connectivity, and traffic flow between various resources. It helps in network monitoring features like Connection monitor, NSG flow logs, Traffic analytics, and diagnostic capabilities. In the given context of monitoring an application distributed across containers, Network insights alone may not provide the application-specific details and performance metrics required for comprehensive monitoring.
Container insightsis incorrect. Container insights in Azure Monitor provides important information about the health, performance, and resource usage of your containers, with a specific focus on the container infrastructure. It helps you understand how your containerized applications are behaving.However, Container Insights is excellent for general insights, but it is not suitable for capturing the detailed information required for synthetic transaction monitoring.? For a closer look at individual transactions and how users interact with your applications, you may find dedicated tools like Application Insights more suitable.
Log Analytics Workspace Insights is incorrect. Log Analytics Workspace Insights provides comprehensive monitoring of your workspaces through a unified view of your workspace usage, performance, health, agent, queries, and change log. It helps in analyzing and responding to the data generated from different data sources. While Log Analytics Workspace is instrumental for logging and diagnostics, it may not have the specific features required for synthetic transaction monitoring. It excels in log data analysis but doesn't inherently provide the transaction-level details and user experience insights that you'd find in dedicated application performance monitoring tools like Application Insights. For a better understanding of your application's performance and user interactions, Application Insights is a better choice.
Read More:
https://learn.microsoft.com/en-us/azure/azure-monitor/app/app-insights-overview
https://learn.microsoft.com/en-us/azure/network-watcher/network-insights-overview
https://learn.microsoft.com/en-us/azure/azure-monitor/containers/container-insights-overview
https://learn.microsoft.com/en-us/azure/azure-monitor/logs/log-analytics-workspace-insights-overview
Explanation
Application Insights is correct. In the given question where an Azure Monitor monitoring solution is required for an application distributed across multiple containers in Azure Container Instances, choosing Application Insights is best. Application Insights support Synthetic Transaction Monitoring (STM), allows developers to proactively measure and test the performance, functionality, and user interaction experience of the application.It uses automated scripts for synthetic monitoring, this method, also known as active monitoring, simulates real user actions to identify and address issues related to website availability and performance before they impact end users. By simulating user interactions, STM ensures that critical paths within the application are functioning correctly, it allows early detection of issues and addressing performance.Therefore, for the given scenario, including Application Insights in the monitoring solution not only supports Synthetic Transaction Monitoring but also aligns with the goal of minimizing development effort by providing a comprehensive and integrated monitoring solution.
Network insights is incorrect. Network Insights in Azure Monitor primarily focus on monitoring network performance, connectivity, and traffic flow between various resources. It helps in network monitoring features like Connection monitor, NSG flow logs, Traffic analytics, and diagnostic capabilities. In the given context of monitoring an application distributed across containers, Network insights alone may not provide the application-specific details and performance metrics required for comprehensive monitoring.
Container insightsis incorrect. Container insights in Azure Monitor provides important information about the health, performance, and resource usage of your containers, with a specific focus on the container infrastructure. It helps you understand how your containerized applications are behaving.However, Container Insights is excellent for general insights, but it is not suitable for capturing the detailed information required for synthetic transaction monitoring.? For a closer look at individual transactions and how users interact with your applications, you may find dedicated tools like Application Insights more suitable.
Log Analytics Workspace Insights is incorrect. Log Analytics Workspace Insights provides comprehensive monitoring of your workspaces through a unified view of your workspace usage, performance, health, agent, queries, and change log. It helps in analyzing and responding to the data generated from different data sources. While Log Analytics Workspace is instrumental for logging and diagnostics, it may not have the specific features required for synthetic transaction monitoring. It excels in log data analysis but doesn't inherently provide the transaction-level details and user experience insights that you'd find in dedicated application performance monitoring tools like Application Insights. For a better understanding of your application's performance and user interactions, Application Insights is a better choice.
Read More:
https://learn.microsoft.com/en-us/azure/azure-monitor/app/app-insights-overview
https://learn.microsoft.com/en-us/azure/network-watcher/network-insights-overview
https://learn.microsoft.com/en-us/azure/azure-monitor/containers/container-insights-overview
https://learn.microsoft.com/en-us/azure/azure-monitor/logs/log-analytics-workspace-insights-overview
Question 14 Single Choice
You have an Azure subscription.
You plan to deploy a monitoring solution that will include the following:
Azure Monitor Network Insights
Application Insights
Microsoft Sentinel
VM insights
The monitoring solution will be managed by a single team.
What is the minimum number of Azure Monitor workspaces required?
Explanation

Click "Show Answer" to see the explanation here
1 is correct. Since the single team is managing the monitoring solution and even with one workspace it is possible to handle Azure Monitor Network Insights, Application Insights, Microsoft Sentinel, and VM insights. The decision to use one or more workspaces, will depend on specific criteria, whether to use a single Azure Monitor workspace, multiple Azure Monitor workspaces, and the configuration and placement of those workspaces. Each workspace is a distinct environment with its own data repository, configuration, and permissions, ensuring a level of isolation and customization. Considering the scenario of deploying Azure Monitor Network Insights, Application Insights, Microsoft Sentinel, and VM insights, managed by a single team, you can use a minimum of single Azure Monitor workspace.
2, 3, and 4 are incorrect. A single Azure Monitor workspace can meet the needs of many scenarios, but some organizations choose to use multiple workspaces. Each workspace functions as a unique environment with its dedicated data repository, configuration, and permissions, providing a level of isolation. For example, in various environments such as test, pre-production, and production, it is recommended to create separate Azure Monitor workspaces by considering specific requirements.
Read More:
Explanation
1 is correct. Since the single team is managing the monitoring solution and even with one workspace it is possible to handle Azure Monitor Network Insights, Application Insights, Microsoft Sentinel, and VM insights. The decision to use one or more workspaces, will depend on specific criteria, whether to use a single Azure Monitor workspace, multiple Azure Monitor workspaces, and the configuration and placement of those workspaces. Each workspace is a distinct environment with its own data repository, configuration, and permissions, ensuring a level of isolation and customization. Considering the scenario of deploying Azure Monitor Network Insights, Application Insights, Microsoft Sentinel, and VM insights, managed by a single team, you can use a minimum of single Azure Monitor workspace.
2, 3, and 4 are incorrect. A single Azure Monitor workspace can meet the needs of many scenarios, but some organizations choose to use multiple workspaces. Each workspace functions as a unique environment with its dedicated data repository, configuration, and permissions, providing a level of isolation. For example, in various environments such as test, pre-production, and production, it is recommended to create separate Azure Monitor workspaces by considering specific requirements.
Read More:
Question 15 Single Choice
You have two app registrations named App1 and App2 in Microsoft Entra. App1 supports role-based access control (RBAC) and includes a role named Writer.
You need to ensure that when App2 authenticates to access App1, the tokens issued by Microsoft Entra ID include the Writer role claim.
Which blade should you use to modify App1 registration?
Explanation

Click "Show Answer" to see the explanation here
App roles is correct. In Microsoft Entra, the App roles blade is a tool for managing access to applications by defining custom roles associated with specific permissions. These App roles provide a mechanism for role-based access control (RBAC), allowing you to assign roles to users, groups, or other applications. When App2 needs to authenticate to access App1 and requires specific permissions, such as the Writer role claim in the tokens issued by Microsoft Entra, modifying the App1 registration using the App roles blade is the recommended option. By defining and configuring the Writer role within App1, you enable App2 to request and grant the role during authentication.
API permissions is incorrect. In the given question, which focuses around ensuring the inclusion of the Writer role claim in tokens during App2 authentication to access App1, the API Permissions blade in Microsoft Entra is not the suitable option. This blade is commonly used for managing an application's permissions when interacting with external APIs. However, it lacks the capability to define custom roles within an application or influence the role claims issued in tokens during the authentication process. For the specified requirement, the more appropriate option is the App roles blade, which is purposefully built for managing application-specific roles with associated permissions.
Token configuration is incorrect. In the context of the question, the goal is to ensure that when App2 authenticates to access App1, the tokens issued by Microsoft Entra include the Writer role claim. While it's related to token configuration, it's not the primary tool for defining custom roles within an application. It deals with configuring standard claims, not application-specific roles like Writer. The App roles blade is more suited to this scenario, as it is specifically designed for managing application-specific roles with their associated permissions.
Read More:
Explanation
App roles is correct. In Microsoft Entra, the App roles blade is a tool for managing access to applications by defining custom roles associated with specific permissions. These App roles provide a mechanism for role-based access control (RBAC), allowing you to assign roles to users, groups, or other applications. When App2 needs to authenticate to access App1 and requires specific permissions, such as the Writer role claim in the tokens issued by Microsoft Entra, modifying the App1 registration using the App roles blade is the recommended option. By defining and configuring the Writer role within App1, you enable App2 to request and grant the role during authentication.
API permissions is incorrect. In the given question, which focuses around ensuring the inclusion of the Writer role claim in tokens during App2 authentication to access App1, the API Permissions blade in Microsoft Entra is not the suitable option. This blade is commonly used for managing an application's permissions when interacting with external APIs. However, it lacks the capability to define custom roles within an application or influence the role claims issued in tokens during the authentication process. For the specified requirement, the more appropriate option is the App roles blade, which is purposefully built for managing application-specific roles with associated permissions.
Token configuration is incorrect. In the context of the question, the goal is to ensure that when App2 authenticates to access App1, the tokens issued by Microsoft Entra include the Writer role claim. While it's related to token configuration, it's not the primary tool for defining custom roles within an application. It deals with configuring standard claims, not application-specific roles like Writer. The App roles blade is more suited to this scenario, as it is specifically designed for managing application-specific roles with their associated permissions.
Read More:
Question 16 Single Choice
You have two app registrations named App1 and App2 in Microsoft Entra. App1 supports role-based access control (RBAC) and includes a role named Writer.
You need to ensure that when App2 authenticates to access App1, the tokens issued by Microsoft Entra ID include the Writer role claim.
Which blade should you use to modify App2 registration?
Explanation

Click "Show Answer" to see the explanation here
Token configuration is correct. To ensure that the tokens issued by Microsoft Entra ID during App2 authentication to access App1 include the Writer role claim, you can utilize the Token configuration blade to modify App2 registration. The Token Configuration blade allows for the customization of claims included in authentication tokens. In this context, you can configure the specific role claims, such as the Writer role, within the Token Configuration settings for App2. This customization ensures that when App2 undergoes authentication to access App1, the issued tokens contain the necessary role claims and seamless role-based access control (RBAC) between the two applications.
App Roles is incorrect. App role blade is primarily designed for managing roles within an application and assigning associated permissions. However, it is not the primary tool for customizing claims in authentication tokens. When the goal is to specifically customize claims, such as role claims, within the tokens issued during authentication, the more suitable choice is the Token Configuration blade. The Token Configuration blade allows for setting the claims included in authentication tokens, providing a more direct and appropriate solution for token customization requirements.
API permissions is incorrect. The API Permissions blade is primarily focused towards managing an application's permissions for interacting with external APIs. Its main function is not about defining custom roles within an application or influencing the role claims within authentication tokens during the authentication process. Instead, it is more focused on facilitating and controlling access to external APIs, making it less suitable for tasks related to customizing authentication tokens. For token customization, especially concerning role claims, you can use tools like the Token Configuration blade.
Read More:
Explanation
Token configuration is correct. To ensure that the tokens issued by Microsoft Entra ID during App2 authentication to access App1 include the Writer role claim, you can utilize the Token configuration blade to modify App2 registration. The Token Configuration blade allows for the customization of claims included in authentication tokens. In this context, you can configure the specific role claims, such as the Writer role, within the Token Configuration settings for App2. This customization ensures that when App2 undergoes authentication to access App1, the issued tokens contain the necessary role claims and seamless role-based access control (RBAC) between the two applications.
App Roles is incorrect. App role blade is primarily designed for managing roles within an application and assigning associated permissions. However, it is not the primary tool for customizing claims in authentication tokens. When the goal is to specifically customize claims, such as role claims, within the tokens issued during authentication, the more suitable choice is the Token Configuration blade. The Token Configuration blade allows for setting the claims included in authentication tokens, providing a more direct and appropriate solution for token customization requirements.
API permissions is incorrect. The API Permissions blade is primarily focused towards managing an application's permissions for interacting with external APIs. Its main function is not about defining custom roles within an application or influencing the role claims within authentication tokens during the authentication process. Instead, it is more focused on facilitating and controlling access to external APIs, making it less suitable for tasks related to customizing authentication tokens. For token customization, especially concerning role claims, you can use tools like the Token Configuration blade.
Read More:
Question 17 Single Choice
You are designing an app that will be hosted on Azure virtual machines that run Ubuntu. The app will use a third-party email service to send email messages to users. The third-party email service requires that the app authenticate by using an API key.
You need to recommend an Azure Key Vault solution for storing and accessing the API key. The solution must minimize administrative effort.
What should you recommend to store the access key?
Explanation

Click "Show Answer" to see the explanation here
Secret is correct. For secure storage and access of an API key in Azure Key Vault with minimized administrative effort, the best choice is to utilize a Secret in Azure Key Vault. Azure Key Vault offers three primary types: secrets, keys, and certificates, designed to safeguard sensitive information. In this scenario, an API key, which is typically a string-based credential, a Secret is the correct choice. By using Azure Key Vault Secrets, you can easily manage and rotate the API key without requiring changes to the application code. Secrets in Azure Key Vault can be versioned, and you can also set access policies to control who can manage and retrieve these secrets.
Key is incorrect. Keys in Azure Key Vault are designed for scenarios involving cryptographic operations, such as encryption or digital signatures. Cryptographic keys in Azure Key Vault support various key types and algorithms, including software-protected and HSM-protected (Hardware Security Module) keys. Storing an API key as a "key" in Key Vault might not be appropriate, as keys are better suited for cryptographic functions. In comparison to API keys, typically plaintext strings, opting for Azure Key Vault Secrets is recommended when dealing with API keys for a third-party email service. This choice better fits the nature of API keys and allows for easy management.
Certificate is incorrect. Certificate is used to provide information about the source of a Key Vault certificate issuer name, provider, credentials, and other administrative details. Certificates are primarily used in scenarios where authentication involves a public-private key pair. This process is more complex and is often used in situations requiring a higher level of security, such as in SSL/TLS for secure communication. Storing and retrieving a simple API key, which is typically a plaintext string, doesn't warrant the complexity of using certificates. Certificates are better suited for cryptographic operations that go beyond the requirements of handling an API key. For example, In HTTPS, a certificate verifies the bank's website, enabling secure, encrypted communication that protects sensitive data like login details and financial information.
Read More:
Explanation
Secret is correct. For secure storage and access of an API key in Azure Key Vault with minimized administrative effort, the best choice is to utilize a Secret in Azure Key Vault. Azure Key Vault offers three primary types: secrets, keys, and certificates, designed to safeguard sensitive information. In this scenario, an API key, which is typically a string-based credential, a Secret is the correct choice. By using Azure Key Vault Secrets, you can easily manage and rotate the API key without requiring changes to the application code. Secrets in Azure Key Vault can be versioned, and you can also set access policies to control who can manage and retrieve these secrets.
Key is incorrect. Keys in Azure Key Vault are designed for scenarios involving cryptographic operations, such as encryption or digital signatures. Cryptographic keys in Azure Key Vault support various key types and algorithms, including software-protected and HSM-protected (Hardware Security Module) keys. Storing an API key as a "key" in Key Vault might not be appropriate, as keys are better suited for cryptographic functions. In comparison to API keys, typically plaintext strings, opting for Azure Key Vault Secrets is recommended when dealing with API keys for a third-party email service. This choice better fits the nature of API keys and allows for easy management.
Certificate is incorrect. Certificate is used to provide information about the source of a Key Vault certificate issuer name, provider, credentials, and other administrative details. Certificates are primarily used in scenarios where authentication involves a public-private key pair. This process is more complex and is often used in situations requiring a higher level of security, such as in SSL/TLS for secure communication. Storing and retrieving a simple API key, which is typically a plaintext string, doesn't warrant the complexity of using certificates. Certificates are better suited for cryptographic operations that go beyond the requirements of handling an API key. For example, In HTTPS, a certificate verifies the bank's website, enabling secure, encrypted communication that protects sensitive data like login details and financial information.
Read More:
Question 18 Single Choice
You are designing an app that will be hosted on Azure virtual machines that run Ubuntu. The app will use a third-party email service to send email messages to users. The third-party email service requires that the app authenticate by using an API key.
You need to recommend an Azure Key Vault solution for storing and accessing the API key. The solution must minimize administrative effort.
What should you recommend to access the key?
Explanation

Click "Show Answer" to see the explanation here
A managed service identity (MSI) is correct. Managed Service Identity (MSI) simplifies granting your VM access to Azure Key Vault. With MSI, Azure handles identity management, eliminating the need for you to manually handle credentials. This feature ensures authentication for your Azure-hosted Ubuntu app. Configuring MSI on your Azure VM automates identity management, enhancing security by allowing Azure to handle credential rolling and lifecycle. The app can use its managed identity to get an Microsoft Entra token and authenticate to Azure Key Vault, securely storing the API key. This approach simplifies administrative tasks through Microsoft Entra's role-based access control, aligning with the goal of minimizing effort in securely accessing the API key.
API Token is incorrect. An API token is a common method for authentication, but it is typically handled and managed manually within your application. This method introduces security risks, as the token might need to be stored somewhere, and if compromised, it could result in unauthorized access. The need for secure storage and management of tokens can introduce complexities and potential vulnerabilities in the application's security posture.
Service Principal is incorrect. While a service principal in Azure is essential for applications and automated tools to access resources, its management involves manual configurations, including Microsoft Entra registration, credential creation, and permission setup. For instance, creating a service principal for an application to read data from an Azure Storage Account requires specific permissions and secure credential management. However, when it comes to API key management in Azure Key Vault, depending on a Service Principal introduces manual complexities, security risks, and administrative efforts.
Read More:
Explanation
A managed service identity (MSI) is correct. Managed Service Identity (MSI) simplifies granting your VM access to Azure Key Vault. With MSI, Azure handles identity management, eliminating the need for you to manually handle credentials. This feature ensures authentication for your Azure-hosted Ubuntu app. Configuring MSI on your Azure VM automates identity management, enhancing security by allowing Azure to handle credential rolling and lifecycle. The app can use its managed identity to get an Microsoft Entra token and authenticate to Azure Key Vault, securely storing the API key. This approach simplifies administrative tasks through Microsoft Entra's role-based access control, aligning with the goal of minimizing effort in securely accessing the API key.
API Token is incorrect. An API token is a common method for authentication, but it is typically handled and managed manually within your application. This method introduces security risks, as the token might need to be stored somewhere, and if compromised, it could result in unauthorized access. The need for secure storage and management of tokens can introduce complexities and potential vulnerabilities in the application's security posture.
Service Principal is incorrect. While a service principal in Azure is essential for applications and automated tools to access resources, its management involves manual configurations, including Microsoft Entra registration, credential creation, and permission setup. For instance, creating a service principal for an application to read data from an Azure Storage Account requires specific permissions and secure credential management. However, when it comes to API key management in Azure Key Vault, depending on a Service Principal introduces manual complexities, security risks, and administrative efforts.
Read More:
Question 19 Single Choice
You have an on-premises Microsoft SQL server named SQL1 that hosts 50 databases.
You plan to migrate SQL1 to Azure SQL Managed Instance.
You need to perform an offline migration of SQL1. The solution must minimize administrative effort.
What should you include in the solution?
Explanation

Click "Show Answer" to see the explanation here
Azure Database Migration Service is correct. Azure Database Migration Service (DMS) is a fully managed solution for smooth migrations from multiple database sources to Azure data platforms, suitable for both online and offline scenarios. It is specifically designed for migrating SQL Server databases, including SQL Server to Azure SQL Database and Azure SQL Managed Instance, DMS ensures minimal downtime and user involvement throughout the migration process. Its resilience and reliability makes it the best choice, and it can be accessed through various interfaces such as the Azure portal, PowerShell, and Azure CLI. The Azure SQL Migration extension for Azure Data Studio, powered by DMS, adds valuable features, facilitating SQL Database modernization to Azure. Also, DMS offers the flexibility to run online migrations, minimizing downtime, or offline migrations for scenarios where downtime is acceptable, making it a suitable solution for the diverse business requirements.
Azure Migrate is incorrect. Azure Migrate offers tools such as Azure Migrate: Discovery and Assessment and Migration and Modernization, offers a flexibility in assessing and migrating servers, databases, and web applications. Particularly for databases, Azure Migrate optimizes the evaluation of on-premises SQL Server instances and databases, facilitating a smooth migration to Azure SQL Managed Instance, Azure SQL Database, or an SQL Server on an Azure VM. Additionally, Azure Migrate extends its capabilities to assess and migrate on-premises web applications to Azure App Service and Azure Kubernetes Service. It handles large-scale data migrations using Azure Data Box products, ensuring a quick and cost-effective transfer of significant data volumes to Azure. Its seamless integration with other Azure services, tools, and independent software vendor (ISV) for the migration journey. Azure Migrate stands as a good solution for organizations migrating on-premises resources to Azure. For an offline migration of SQL1 to Azure SQL Managed Instance, with minimal administrative effort, Azure Migrate may not be the most suitable tool. Tools like Azure Database Migration Service are more suitable for offline migration scenarios.
SQL Server Migration Assistant (SSMA) is incorrect. SSMA is a Microsoft tool designed to automate the migration of databases to SQL Server from various platforms, including Microsoft Access, DB2, MySQL, Oracle, and SAP ASE. SSMA is more focused on the migration process, providing assessment reports, converting database objects, and ensuring compatibility with Azure SQL services.While it excels in streamlining migrations from diverse sources to SQL Server, it may not offer the same level of automation and management needed for an offline migration scenario. In the context of an offline migration scenario, a dedicated solution like Azure Database Migration Service works well which is designed for both online and offline migrations.
Data Migration Assistant is incorrect. The Data Migration Assistant (DMA) is a tool that helps in upgrading to a modern data platform by detecting compatibility issues which may affect database functionality during an upgrade to a new SQL Server version or migration to Azure SQL Database. DMA not only identifies potential compatibility concerns but also provides recommendations for performance and reliability improvements in the target environment. Its primary focus is on assessing the readiness of databases for migration. However, DMA does not perform the actual migration, it concentrates on preparing databases for migration rather than executing the migration process. On the other hand, Azure Database Migration Service (DMS) is a suitable solution designed to handle both online and offline migrations. It guarantees a smoother migration by minimizing administrative efforts in migration processes. Therefore, for an offline migration scenario Azure DMS is a preferable solution compared to DMA.
Read More:
Explanation
Azure Database Migration Service is correct. Azure Database Migration Service (DMS) is a fully managed solution for smooth migrations from multiple database sources to Azure data platforms, suitable for both online and offline scenarios. It is specifically designed for migrating SQL Server databases, including SQL Server to Azure SQL Database and Azure SQL Managed Instance, DMS ensures minimal downtime and user involvement throughout the migration process. Its resilience and reliability makes it the best choice, and it can be accessed through various interfaces such as the Azure portal, PowerShell, and Azure CLI. The Azure SQL Migration extension for Azure Data Studio, powered by DMS, adds valuable features, facilitating SQL Database modernization to Azure. Also, DMS offers the flexibility to run online migrations, minimizing downtime, or offline migrations for scenarios where downtime is acceptable, making it a suitable solution for the diverse business requirements.
Azure Migrate is incorrect. Azure Migrate offers tools such as Azure Migrate: Discovery and Assessment and Migration and Modernization, offers a flexibility in assessing and migrating servers, databases, and web applications. Particularly for databases, Azure Migrate optimizes the evaluation of on-premises SQL Server instances and databases, facilitating a smooth migration to Azure SQL Managed Instance, Azure SQL Database, or an SQL Server on an Azure VM. Additionally, Azure Migrate extends its capabilities to assess and migrate on-premises web applications to Azure App Service and Azure Kubernetes Service. It handles large-scale data migrations using Azure Data Box products, ensuring a quick and cost-effective transfer of significant data volumes to Azure. Its seamless integration with other Azure services, tools, and independent software vendor (ISV) for the migration journey. Azure Migrate stands as a good solution for organizations migrating on-premises resources to Azure. For an offline migration of SQL1 to Azure SQL Managed Instance, with minimal administrative effort, Azure Migrate may not be the most suitable tool. Tools like Azure Database Migration Service are more suitable for offline migration scenarios.
SQL Server Migration Assistant (SSMA) is incorrect. SSMA is a Microsoft tool designed to automate the migration of databases to SQL Server from various platforms, including Microsoft Access, DB2, MySQL, Oracle, and SAP ASE. SSMA is more focused on the migration process, providing assessment reports, converting database objects, and ensuring compatibility with Azure SQL services.While it excels in streamlining migrations from diverse sources to SQL Server, it may not offer the same level of automation and management needed for an offline migration scenario. In the context of an offline migration scenario, a dedicated solution like Azure Database Migration Service works well which is designed for both online and offline migrations.
Data Migration Assistant is incorrect. The Data Migration Assistant (DMA) is a tool that helps in upgrading to a modern data platform by detecting compatibility issues which may affect database functionality during an upgrade to a new SQL Server version or migration to Azure SQL Database. DMA not only identifies potential compatibility concerns but also provides recommendations for performance and reliability improvements in the target environment. Its primary focus is on assessing the readiness of databases for migration. However, DMA does not perform the actual migration, it concentrates on preparing databases for migration rather than executing the migration process. On the other hand, Azure Database Migration Service (DMS) is a suitable solution designed to handle both online and offline migrations. It guarantees a smoother migration by minimizing administrative efforts in migration processes. Therefore, for an offline migration scenario Azure DMS is a preferable solution compared to DMA.
Read More:
Question 20 Single Choice
You have a Microsoft Entra tenant that contains an administrative unit named MarketingAU. MarketingAU contains 100 users.
You create two users named User1 and User2.
You need to ensure that the users can perform the following actions in MarketingAU:
User1 must be able to create user accounts.
User2 must be able to reset user passwords.
Which role should you assign to User1?
Explanation

Click "Show Answer" to see the explanation here
User Administrator for MarketingAU is correct. Assigning the User Administrator for MarketingAU role is the most suitable choice for User1 because it provides the necessary permissions to create and manage user accounts specifically within the MarketingAU administrative unit. This role follows the principle of least privilege by granting the exact level of access required for the defined task without unnecessary permissions. Granting roles with the least necessary access will be the best practice for security and governance.
User Administrator for the tenant is incorrect. Assigning the User Administrator for the tenant role would provide User1 with extensive permissions across the entire Microsoft Entra tenant. This includes all administrative units and resources, which goes beyond the specified scope of MarketingAU. The principle of least privilege tells that users should only have the minimum level of access required for their specific responsibilities. Granting User1 access to the entire tenant introduces unnecessary risk and potential loss.
Helpdesk Administrator for MarketingAU is incorrect. While the Helpdesk Administrator for MarketingAU role allows some administrative actions like resetting passwords for non-administrators, invalidating refresh tokens, creating and managing support requests with Microsoft for Azure and Microsoft 365 services, and monitoring service health in the assigned unit (MarketingAU), it still lacks specific permissions needed for creating user accounts.
Helpdesk Administrator for the tenant is incorrect. While the Helpdesk Administrator for MarketingAU role allows for some administrative actions, it operates at the tenant level, where it can affect all users in the Microsoft Entra tenant level. While it includes actions like resetting passwords for non-administrators, invalidating refresh tokens, creating and managing support requests with Microsoft for Azure and Microsoft 365 services, and monitoring service health, it still lacks the specific permissions needed for creating user accounts.
Read More:
Explanation
User Administrator for MarketingAU is correct. Assigning the User Administrator for MarketingAU role is the most suitable choice for User1 because it provides the necessary permissions to create and manage user accounts specifically within the MarketingAU administrative unit. This role follows the principle of least privilege by granting the exact level of access required for the defined task without unnecessary permissions. Granting roles with the least necessary access will be the best practice for security and governance.
User Administrator for the tenant is incorrect. Assigning the User Administrator for the tenant role would provide User1 with extensive permissions across the entire Microsoft Entra tenant. This includes all administrative units and resources, which goes beyond the specified scope of MarketingAU. The principle of least privilege tells that users should only have the minimum level of access required for their specific responsibilities. Granting User1 access to the entire tenant introduces unnecessary risk and potential loss.
Helpdesk Administrator for MarketingAU is incorrect. While the Helpdesk Administrator for MarketingAU role allows some administrative actions like resetting passwords for non-administrators, invalidating refresh tokens, creating and managing support requests with Microsoft for Azure and Microsoft 365 services, and monitoring service health in the assigned unit (MarketingAU), it still lacks specific permissions needed for creating user accounts.
Helpdesk Administrator for the tenant is incorrect. While the Helpdesk Administrator for MarketingAU role allows for some administrative actions, it operates at the tenant level, where it can affect all users in the Microsoft Entra tenant level. While it includes actions like resetting passwords for non-administrators, invalidating refresh tokens, creating and managing support requests with Microsoft for Azure and Microsoft 365 services, and monitoring service health, it still lacks the specific permissions needed for creating user accounts.
Read More:



