

Microsoft Certified: DevOps Engineer Expert - (AZ-400) Exam Questions
Total Questions
Last Updated
1st Try Guaranteed

Experts Verified
Question 1 Single Choice
You have an Azure subscription that contains an Azure key vault named Vault1, an Azure pipeline named Pipeline1, and an Azure SQL database named DB1.
Pipeline1 is used to deploy an app that will authenticate to DB1 by using a password.
You need to store the password in Vault1. The solution must ensure that the password can be accessed by Pipeline1.
How should you store the password as?
Explanation

Click "Show Answer" to see the explanation here
Correct Answer(s): Secret
Secret is CORRECT because in Azure Key Vault, secrets are used to store sensitive data such as passwords, connection strings, and other pieces of information that are needed in a secure manner by various services. Pipeline1 can retrieve this stored password from Vault1 during deployment to authenticate to the Azure SQL database DB1.
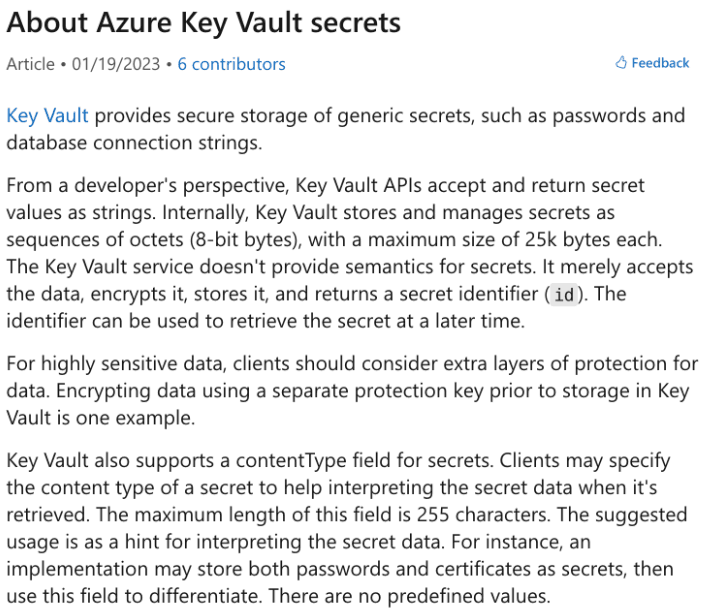
Certificate is INCORRECT because certificates are typically used for TLS/SSL and for authentication where a certificate-based authentication mechanism is required. Certificates include a private key and a public key but are not used for storing passwords.
Key is INCORRECT because keys in Azure Key Vault refer to cryptographic keys that are used for operations like encrypting and decrypting data, not for storing passwords for authentication purposes.
Reference Links:
https://learn.microsoft.com/en-us/azure/key-vault/secrets/about-secrets
Explanation
Correct Answer(s): Secret
Secret is CORRECT because in Azure Key Vault, secrets are used to store sensitive data such as passwords, connection strings, and other pieces of information that are needed in a secure manner by various services. Pipeline1 can retrieve this stored password from Vault1 during deployment to authenticate to the Azure SQL database DB1.

Certificate is INCORRECT because certificates are typically used for TLS/SSL and for authentication where a certificate-based authentication mechanism is required. Certificates include a private key and a public key but are not used for storing passwords.
Key is INCORRECT because keys in Azure Key Vault refer to cryptographic keys that are used for operations like encrypting and decrypting data, not for storing passwords for authentication purposes.
Reference Links:
https://learn.microsoft.com/en-us/azure/key-vault/secrets/about-secrets
Question 2 Single Choice
You have an Azure subscription that contains an Azure key vault named Vault1, an Azure pipeline named Pipeline1, and an Azure SQL database named DB1.
Pipeline1 is used to deploy an app that will authenticate to DB1 by using a password.
You need to store the password in Vault1. The solution must ensure that the password can be accessed by Pipeline1.
What would you modify to grant Pipeline1 access to Vault1?
Explanation

Click "Show Answer" to see the explanation here
Correct Answer(s): Access policies
Access policies is CORRECT as access policies in Azure Key Vault are the correct place to configure permissions for identities (such as service principals or managed identities) to access the secrets, keys, and certificates in the vault. You would modify the access policies to grant the appropriate level of access to the identity used by Pipeline1, allowing it to retrieve the password stored as a secret in Vault1 during the deployment process.
Access control (IAM) settings is INCORRECT because while IAM settings determine who has management access to the Key Vault resource itself within the Azure subscription, it does not grant fine-grained permissions to the data stored within the Key Vault like access policies do.
Security settings is INCORRECT because this is a broad term and in the context of Azure, it generally refers to the security features and configurations of a subscription or a service, not the specific data access permissions within Azure Key Vault.
Reference(s):
https://learn.microsoft.com/en-us/azure/key-vault/general/security-features
https://learn.microsoft.com/en-us/azure/key-vault/general/network-security
Explanation
Correct Answer(s): Access policies
Access policies is CORRECT as access policies in Azure Key Vault are the correct place to configure permissions for identities (such as service principals or managed identities) to access the secrets, keys, and certificates in the vault. You would modify the access policies to grant the appropriate level of access to the identity used by Pipeline1, allowing it to retrieve the password stored as a secret in Vault1 during the deployment process.
Access control (IAM) settings is INCORRECT because while IAM settings determine who has management access to the Key Vault resource itself within the Azure subscription, it does not grant fine-grained permissions to the data stored within the Key Vault like access policies do.
Security settings is INCORRECT because this is a broad term and in the context of Azure, it generally refers to the security features and configurations of a subscription or a service, not the specific data access permissions within Azure Key Vault.
Reference(s):
https://learn.microsoft.com/en-us/azure/key-vault/general/security-features
https://learn.microsoft.com/en-us/azure/key-vault/general/network-security
Question 3 Single Choice
You use Azure Repos to manage source code and Azure Pipelines to implement continuous integration and continuous deployment (CI/CD).
You need to ensure that all comments on pull requests are resolved before the pull requests are included in a build. The solution must minimize administrative effort.
What should you include in the solution?
Explanation

Click "Show Answer" to see the explanation here
Correct Answer(s): a branch policy
a branch policy is CORRECT because in Azure Repos, you can enforce branch policies that require all comments on a pull request to be resolved before the pull request can be completed. This ensures that no pull request with active comments is merged into the target branch, which aligns with the continuous integration process in Azure Pipelines. Setting up a branch policy minimizes administrative effort by automating the enforcement of this requirement.
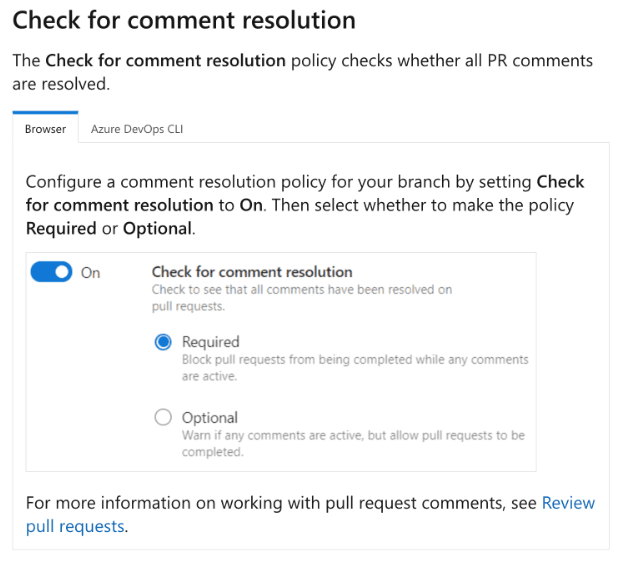
a custom action is INCORRECT because GitHub Actions uses custom actions, not Azure Pipelines. Moreover, custom actions would require manual setup and potentially more ongoing administration compared to using branch policies which are built into Azure Repos.
a post-deployment gate is INCORRECT because post-deployment gates are used after a deployment in a release pipeline to evaluate the deployment's success using various criteria. They are not related to the pull request process or code comments.
a pre-deployment gate is INCORRECT because pre-deployment gates are used before a deployment in a release pipeline to ensure certain conditions are met before proceeding with the deployment. Like post-deployment gates, they do not relate to the enforcement of resolved comments on pull requests.
Reference Links:
Explanation
Correct Answer(s): a branch policy
a branch policy is CORRECT because in Azure Repos, you can enforce branch policies that require all comments on a pull request to be resolved before the pull request can be completed. This ensures that no pull request with active comments is merged into the target branch, which aligns with the continuous integration process in Azure Pipelines. Setting up a branch policy minimizes administrative effort by automating the enforcement of this requirement.

a custom action is INCORRECT because GitHub Actions uses custom actions, not Azure Pipelines. Moreover, custom actions would require manual setup and potentially more ongoing administration compared to using branch policies which are built into Azure Repos.
a post-deployment gate is INCORRECT because post-deployment gates are used after a deployment in a release pipeline to evaluate the deployment's success using various criteria. They are not related to the pull request process or code comments.
a pre-deployment gate is INCORRECT because pre-deployment gates are used before a deployment in a release pipeline to ensure certain conditions are met before proceeding with the deployment. Like post-deployment gates, they do not relate to the enforcement of resolved comments on pull requests.
Reference Links:
Question 4 Single Choice
You use GitHub to host container packages that use Semantic Versioning (SemVer).
You have an app named App1. The current version of App1 is 11.2.0.
You change the code of App1 to fix a bug that was introduced in version 10.5.1.
Which version number should you assign to the release?
Explanation

Click "Show Answer" to see the explanation here
Correct Answer(s): 11.2.1
11.2.1 is CORRECT because according to Semantic Versioning (SemVer), when you fix a bug and there are no new features or breaking changes, you increment the PATCH version. Since the current version of the app is 11.2.0, the next version with a bug fix would be 11.2.1, even if the bug was introduced in an earlier version.
10.5.1-PATCH is INCORRECT because Semantic Versioning does not use a "-PATCH" suffix for version numbers. Instead, it uses a three-part version number: MAJOR.MINOR.PATCH.
10.5.2 is INCORRECT because going back to an older MINOR version and incrementing the PATCH number would imply that users of versions 10.6.0 to 11.2.0 do not receive the bug fix. This would not be consistent with the intent of SemVer, which is to ensure that all users on the current MAJOR release benefit from bug fixes.
10.6.0 is INCORRECT because this would indicate that new functionality has been added in a backwards compatible manner, not a bug fix. Additionally, this would not be correct as it would still be a previous minor version and would not include all the updates and fixes from subsequent versions.
Reference(s):
Explanation
Correct Answer(s): 11.2.1
11.2.1 is CORRECT because according to Semantic Versioning (SemVer), when you fix a bug and there are no new features or breaking changes, you increment the PATCH version. Since the current version of the app is 11.2.0, the next version with a bug fix would be 11.2.1, even if the bug was introduced in an earlier version.
10.5.1-PATCH is INCORRECT because Semantic Versioning does not use a "-PATCH" suffix for version numbers. Instead, it uses a three-part version number: MAJOR.MINOR.PATCH.
10.5.2 is INCORRECT because going back to an older MINOR version and incrementing the PATCH number would imply that users of versions 10.6.0 to 11.2.0 do not receive the bug fix. This would not be consistent with the intent of SemVer, which is to ensure that all users on the current MAJOR release benefit from bug fixes.
10.6.0 is INCORRECT because this would indicate that new functionality has been added in a backwards compatible manner, not a bug fix. Additionally, this would not be correct as it would still be a previous minor version and would not include all the updates and fixes from subsequent versions.
Reference(s):
Question 5 Single Choice
You use GitHub for source control and Microsoft Teams for collaboration.
You need to send a notification to a Teams channel for each commit. The solution must minimize development effort.
What should you do?
Explanation

Click "Show Answer" to see the explanation here
Correct Answer(s): Use the Microsoft Teams for GitHub app and configure a subscription to receive notifications in the Teams channel
Use the Microsoft Teams for GitHub app and configure a subscription to receive notifications in the Teams channel is CORRECT because this app is designed to integrate GitHub with Microsoft Teams directly and can be used to create subscriptions for various GitHub events, including commits. This approach minimizes development effort because it uses pre-built integration and does not require writing any custom code or setting up additional infrastructure.
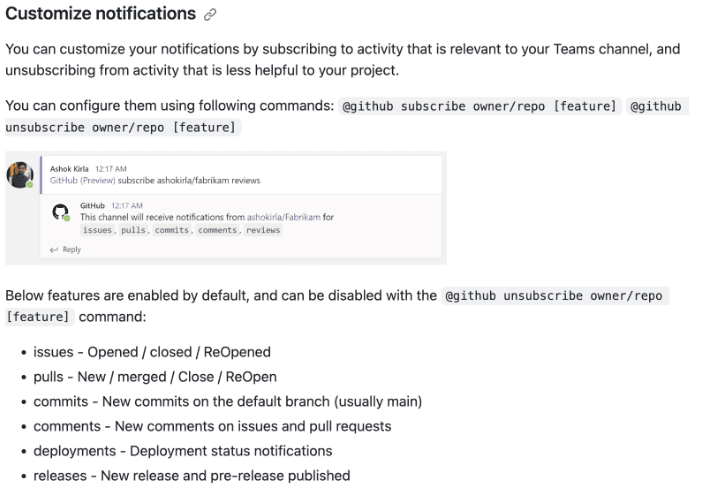
Use Azure Automation to connect to the GitHub Actions API and send a message to the Teams channel is INCORRECT because this would require creating and maintaining runbooks in Azure Automation, which involves unnecessary complexity compared to using the dedicated Teams app for GitHub.
Use GitHub Actions with a dispatch to send a message to the Teams channel by using the Teams API is INCORRECT because, while this is technically possible, it would require more development effort to set up a custom GitHub Actions workflow to interact with the Teams API.
Use Azure Functions to connect to the GitHub REST API and send a message to the Teams channel is INCORRECT because this would involve writing and maintaining custom code in Azure Functions to handle GitHub webhooks and interact with the Teams API, which is more complex than using the existing Teams app for GitHub.
Reference Links:
https://github.com/integrations/microsoft-teams#customize-notifications
Explanation
Correct Answer(s): Use the Microsoft Teams for GitHub app and configure a subscription to receive notifications in the Teams channel
Use the Microsoft Teams for GitHub app and configure a subscription to receive notifications in the Teams channel is CORRECT because this app is designed to integrate GitHub with Microsoft Teams directly and can be used to create subscriptions for various GitHub events, including commits. This approach minimizes development effort because it uses pre-built integration and does not require writing any custom code or setting up additional infrastructure.

Use Azure Automation to connect to the GitHub Actions API and send a message to the Teams channel is INCORRECT because this would require creating and maintaining runbooks in Azure Automation, which involves unnecessary complexity compared to using the dedicated Teams app for GitHub.
Use GitHub Actions with a dispatch to send a message to the Teams channel by using the Teams API is INCORRECT because, while this is technically possible, it would require more development effort to set up a custom GitHub Actions workflow to interact with the Teams API.
Use Azure Functions to connect to the GitHub REST API and send a message to the Teams channel is INCORRECT because this would involve writing and maintaining custom code in Azure Functions to handle GitHub webhooks and interact with the Teams API, which is more complex than using the existing Teams app for GitHub.
Reference Links:
https://github.com/integrations/microsoft-teams#customize-notifications
Question 6 Single Choice
You have an Azure web app that is deployed by using Azure Pipelines.
You need to ensure that when a new version of the app is deployed to production, you can roll back to the previous version. The solution must meet the following requirements:
Minimize downtime during the deployment.
Minimize the time it takes for the rollback.
What should you use?
Explanation

Click "Show Answer" to see the explanation here
Correct Answer(s): a single web app and two deployment slots
a single web app and two deployment slots is CORRECT because Azure App Service deployment slots allow you to stage a new version of your app in a separate deployment slot before swapping it with the production slot. If there is an issue with the new version, you can quickly swap back to the previous version with minimal downtime, thus meeting the requirements of minimizing downtime and the time it takes for the rollback.
a single web app and two deployment pipelines is INCORRECT because while having separate deployment pipelines for different stages can be part of a CI/CD process, it does not directly support quick rollbacks to a previous version without redeployment, which would not minimize downtime.
two web apps and an Azure Standard Load Balancer is INCORRECT because this setup would involve more complexity and does not provide an inherent rollback mechanism. Load balancers are used for distributing traffic, not for app version management or rollbacks.
two web apps and an Azure Traffic Manager instance is INCORRECT because, like the load balancer, Azure Traffic Manager is used for directing user traffic and improving availability and responsiveness. While it could potentially route traffic between different versions of an app hosted on separate web apps, it would not meet the requirement of minimizing downtime and the time it takes for the rollback as efficiently as using deployment slots.
Reference Links:
https://learn.microsoft.com/en-us/azure/app-service/deploy-staging-slots?tabs=portal
https://learn.microsoft.com/en-us/azure/app-service/deploy-staging-slots?tabs=portal
Explanation
Correct Answer(s): a single web app and two deployment slots
a single web app and two deployment slots is CORRECT because Azure App Service deployment slots allow you to stage a new version of your app in a separate deployment slot before swapping it with the production slot. If there is an issue with the new version, you can quickly swap back to the previous version with minimal downtime, thus meeting the requirements of minimizing downtime and the time it takes for the rollback.
a single web app and two deployment pipelines is INCORRECT because while having separate deployment pipelines for different stages can be part of a CI/CD process, it does not directly support quick rollbacks to a previous version without redeployment, which would not minimize downtime.
two web apps and an Azure Standard Load Balancer is INCORRECT because this setup would involve more complexity and does not provide an inherent rollback mechanism. Load balancers are used for distributing traffic, not for app version management or rollbacks.
two web apps and an Azure Traffic Manager instance is INCORRECT because, like the load balancer, Azure Traffic Manager is used for directing user traffic and improving availability and responsiveness. While it could potentially route traffic between different versions of an app hosted on separate web apps, it would not meet the requirement of minimizing downtime and the time it takes for the rollback as efficiently as using deployment slots.
Reference Links:
https://learn.microsoft.com/en-us/azure/app-service/deploy-staging-slots?tabs=portal
https://learn.microsoft.com/en-us/azure/app-service/deploy-staging-slots?tabs=portal
Question 7 Single Choice
You plan to create an image that will contain a .NET Core application.
You have a Dockerfile file that contains the following code. (Line numbers are included for reference only.)
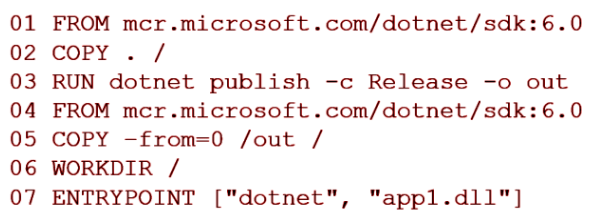
You need to ensure that the image is as small as possible when the image is built.
Which line should you modify in the file?
Explanation

Click "Show Answer" to see the explanation here
Correct Answer(s): 4
4 is CORRECT. To ensure the Docker image is as small as possible, you should use a multi-stage build with a smaller base image for the final stage of the build, which typically contains just the runtime necessary to run the application. The SDK image is larger because it contains the SDK and build tools needed to build the application, which aren't needed in the final image.
The line that should be modified is:Line 4: FROM mcr.microsoft.com/dotnet/sdk:6.0
This line should be modified to use a runtime image instead of the SDK image. The .NET runtime image is smaller than the SDK image and is sufficient for running a .NET application.
The line should look something like this after modification:Line4: FROM mcr.microsoft.com/dotnet/runtime:6.0
Reference Links:
https://learn.microsoft.com/en-us/dotnet/core/docker/build-container?tabs=windows&pivots=dotnet-8-0
https://docs.docker.com/build/building/multi-stage/#use-multi-stage-builds
Explanation
Correct Answer(s): 4
4 is CORRECT. To ensure the Docker image is as small as possible, you should use a multi-stage build with a smaller base image for the final stage of the build, which typically contains just the runtime necessary to run the application. The SDK image is larger because it contains the SDK and build tools needed to build the application, which aren't needed in the final image.
The line that should be modified is:Line 4: FROM mcr.microsoft.com/dotnet/sdk:6.0
This line should be modified to use a runtime image instead of the SDK image. The .NET runtime image is smaller than the SDK image and is sufficient for running a .NET application.
The line should look something like this after modification:Line4: FROM mcr.microsoft.com/dotnet/runtime:6.0
Reference Links:
https://learn.microsoft.com/en-us/dotnet/core/docker/build-container?tabs=windows&pivots=dotnet-8-0
https://docs.docker.com/build/building/multi-stage/#use-multi-stage-builds
Question 8 Single Choice
You create a Git repository named Repo1 in Azure Repos.
You need to configure Repo1 to meet the following requirement:
Work items must be linked to a pull request.
The solution must minimize administrative effort.
Which type of policy should you use for this requirement?
Explanation

Click "Show Answer" to see the explanation here
Correct Answer(s): Branch
Branch is CORRECT because the branch policy in Azure Repos allows you to enforce work item linking as a part of the pull request process. By setting up a branch policy, you can require that all pull requests to a specified branch are associated with a work item, ensuring that changes are tracked against tasks, bugs, or other work items. This approach minimizes administrative effort as it automates the enforcement of this requirement and integrates smoothly with the workflow in Azure DevOps.
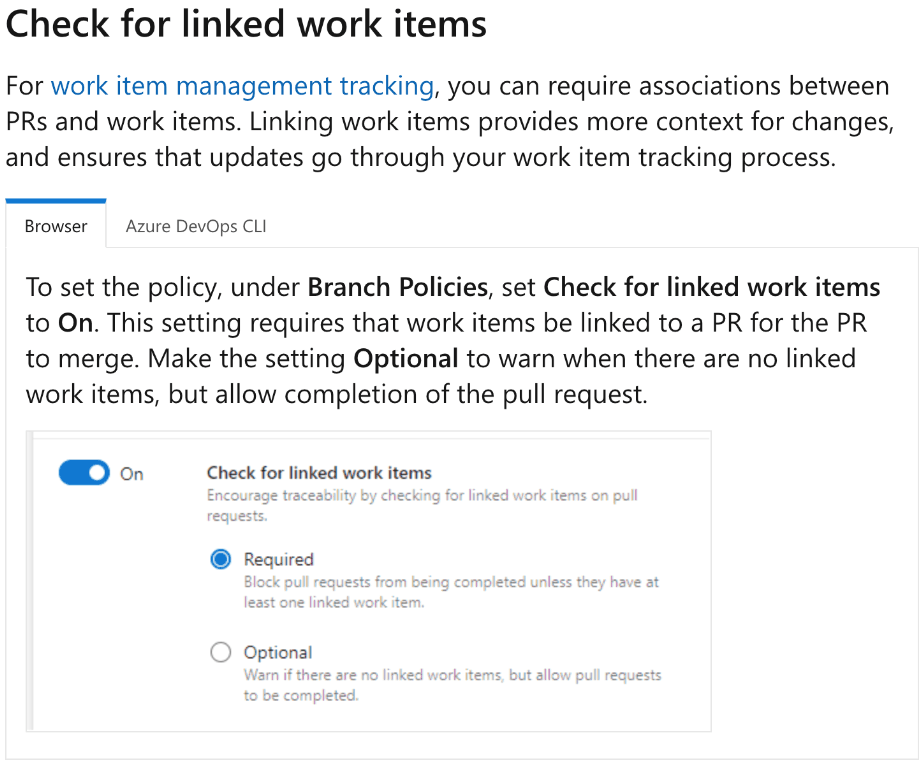
Build is INCORRECT because build policies in Azure Repos are used to ensure that a build has passed before changes can be merged into a branch. While this ensures code quality, it does not directly enforce the linking of work items to pull requests.
Check-in is INCORRECT because check-in policies are used in Team Foundation Version Control (TFVC), not in Git repositories. They enforce certain conditions before code can be checked in, but they are not applicable to Git repositories like Repo1 in Azure Repos.
Status is INCORRECT because status policies in Azure Repos are used to enforce that certain conditions are met based on the status of external services or processes, such as passing a check from an external build system or a third-party service. They do not inherently enforce the linking of work items to pull requests.
Reference(s):
Explanation
Correct Answer(s): Branch
Branch is CORRECT because the branch policy in Azure Repos allows you to enforce work item linking as a part of the pull request process. By setting up a branch policy, you can require that all pull requests to a specified branch are associated with a work item, ensuring that changes are tracked against tasks, bugs, or other work items. This approach minimizes administrative effort as it automates the enforcement of this requirement and integrates smoothly with the workflow in Azure DevOps.

Build is INCORRECT because build policies in Azure Repos are used to ensure that a build has passed before changes can be merged into a branch. While this ensures code quality, it does not directly enforce the linking of work items to pull requests.
Check-in is INCORRECT because check-in policies are used in Team Foundation Version Control (TFVC), not in Git repositories. They enforce certain conditions before code can be checked in, but they are not applicable to Git repositories like Repo1 in Azure Repos.
Status is INCORRECT because status policies in Azure Repos are used to enforce that certain conditions are met based on the status of external services or processes, such as passing a check from an external build system or a third-party service. They do not inherently enforce the linking of work items to pull requests.
Reference(s):
Question 9 Single Choice
You create a Git repository named Repo1 in Azure Repos.
You need to configure Repo1 to meet the following requirement:
Pull requests must have a minimum of two reviewers.
The solution must minimize administrative effort.
Which type of policy should you use for this requirement?
Explanation

Click "Show Answer" to see the explanation here
Correct Answer(s): Branch
Branch is CORRECT because branch policies in Azure Repos can be used to enforce rules for pull requests, including the requirement for a minimum number of reviewers. By setting up a branch policy for Repo1, you can specify that all pull requests targeting the branch require at least two reviewers. This ensures code quality and adherence to team practices with minimal administrative effort, as the policy automatically applies to all relevant pull requests.
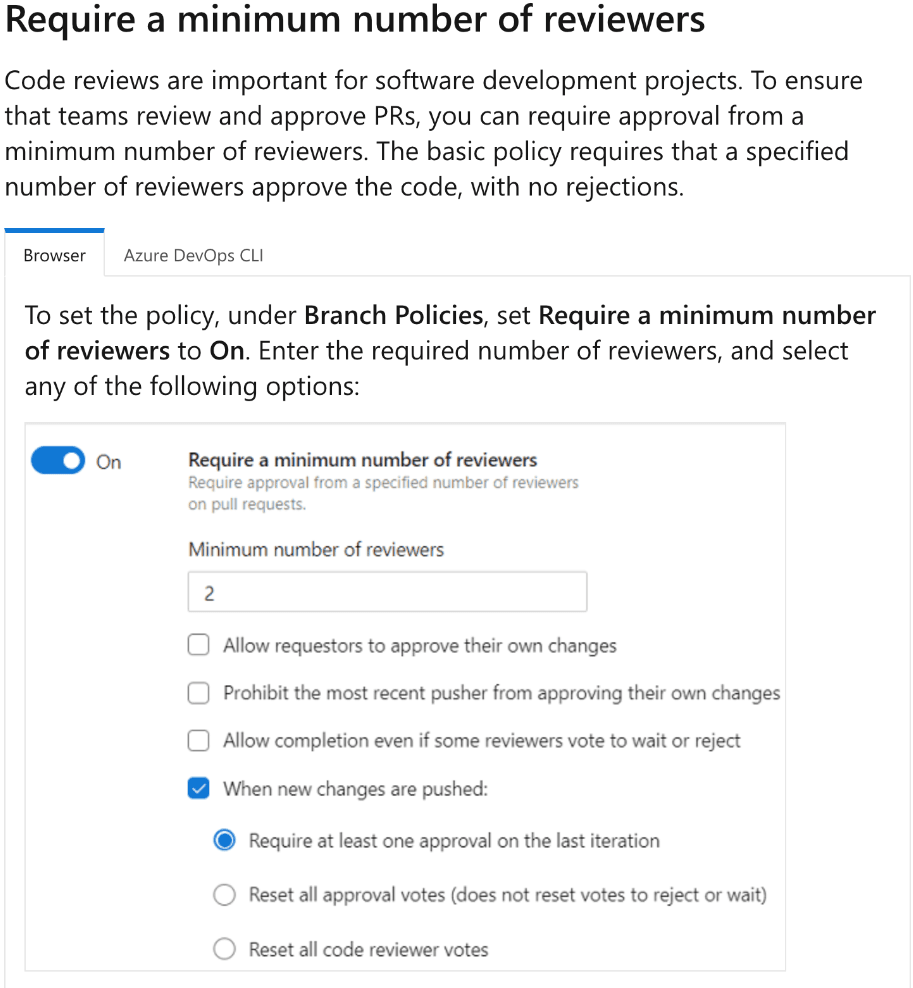
Build is INCORRECT because build policies are focused on ensuring that code changes pass build validation or automated tests before they are merged. They do not provide functionality to require a specific number of reviewers for pull requests.
Check-in is INCORRECT because check-in policies are applicable to Team Foundation Version Control (TFVC) and not to Git repositories. These policies enforce conditions for check-ins, such as code analysis or testing, but are not relevant for managing pull request review requirements in Git repositories.
Status is INCORRECT because status policies are related to the integration of external services or status checks, such as continuous integration builds or third-party tools. They are not used to enforce rules about the number of reviewers for pull requests.
Reference(s):
Explanation
Correct Answer(s): Branch
Branch is CORRECT because branch policies in Azure Repos can be used to enforce rules for pull requests, including the requirement for a minimum number of reviewers. By setting up a branch policy for Repo1, you can specify that all pull requests targeting the branch require at least two reviewers. This ensures code quality and adherence to team practices with minimal administrative effort, as the policy automatically applies to all relevant pull requests.

Build is INCORRECT because build policies are focused on ensuring that code changes pass build validation or automated tests before they are merged. They do not provide functionality to require a specific number of reviewers for pull requests.
Check-in is INCORRECT because check-in policies are applicable to Team Foundation Version Control (TFVC) and not to Git repositories. These policies enforce conditions for check-ins, such as code analysis or testing, but are not relevant for managing pull request review requirements in Git repositories.
Status is INCORRECT because status policies are related to the integration of external services or status checks, such as continuous integration builds or third-party tools. They are not used to enforce rules about the number of reviewers for pull requests.
Reference(s):
Question 10 Single Choice
You create a Git repository named Repo1 in Azure Repos.
You need to configure Repo1 to meet the following requirement:
Pull requests must complete a code review by using a third-party tool.
The solution must minimize administrative effort.
Which type of policy should you use for this requirement?
Explanation

Click "Show Answer" to see the explanation here
Correct Answer(s): Branch
Branch is CORRECT because in Azure Repos, a branch policy can be configured to enforce various requirements for pull requests, including the integration with third-party tools for code reviews. While Azure Repos does not directly integrate with third-party code review tools, it supports reporting the status of these reviews back to the pull request via status checks. A branch policy can be set to require these status checks to pass, which can be reported by the third-party tool, before the pull request can be completed. This approach minimizes administrative effort by automating the enforcement of the code review requirement.
Build is INCORRECT because build policies focus on ensuring successful builds or automated tests pass before merging changes, rather than integrating with third-party code review tools.
Check-in is INCORRECT as it applies to Team Foundation Version Control (TFVC) and is not relevant for Git repositories in Azure Repos.
Status is INCORRECT for this specific requirement because it typically relates to the integration of external services or status checks that are not directly controlling the code review process with a third-party tool.
Reference(s):
Explanation
Correct Answer(s): Branch
Branch is CORRECT because in Azure Repos, a branch policy can be configured to enforce various requirements for pull requests, including the integration with third-party tools for code reviews. While Azure Repos does not directly integrate with third-party code review tools, it supports reporting the status of these reviews back to the pull request via status checks. A branch policy can be set to require these status checks to pass, which can be reported by the third-party tool, before the pull request can be completed. This approach minimizes administrative effort by automating the enforcement of the code review requirement.
Build is INCORRECT because build policies focus on ensuring successful builds or automated tests pass before merging changes, rather than integrating with third-party code review tools.
Check-in is INCORRECT as it applies to Team Foundation Version Control (TFVC) and is not relevant for Git repositories in Azure Repos.
Status is INCORRECT for this specific requirement because it typically relates to the integration of external services or status checks that are not directly controlling the code review process with a third-party tool.
Reference(s):



