Microsoft Certified: Security, Compliance, and Identity Fundamentals - (SC-900) Exam Questions
Total Questions
Last Updated
1st Try Guaranteed

Experts Verified
Question 1 Single Choice
Scenario: Beyond Corporation is an organization which originated on the planet Vulcan which is lead by S'chn T'gai Spock as the Supreme Commander. Spock has investigated the Microsoft platform and found it to be formidable and has decided to implement its use into Beyond.
The current project related to the migration to Microsoft is utilizing Azure Active Directory Identity Protection. Montgomery "Scotty" Scott is the Chief Engineer working on the migration. One of the Jr Engineers working on the project is explaining to Scotty that Azure AD Identity Protection can add users to groups based on the users’ risk level.
Is the Jr Engineer correct?
Explanation

Click "Show Answer" to see the explanation here
No - Azure AD Identity Protection cannot add users to groups based on the users’ risk level.
Risk levels
Identity Protection categorizes risk into three tiers: low, medium, and high.
While Microsoft does not provide specific details about how risk is calculated, we will say that each level brings higher confidence that the user or sign-in is compromised. For example, something like one instance of unfamiliar sign-in properties for a user might not be as threatening as leaked credentials for another user.
Exporting risk data
Data from Identity Protection can be exported to other tools for archive and further investigation and correlation. The Microsoft Graph based APIs allow organizations to collect this data for further processing in a tool such as their SIEM.
Explanation
No - Azure AD Identity Protection cannot add users to groups based on the users’ risk level.
Risk levels
Identity Protection categorizes risk into three tiers: low, medium, and high.
While Microsoft does not provide specific details about how risk is calculated, we will say that each level brings higher confidence that the user or sign-in is compromised. For example, something like one instance of unfamiliar sign-in properties for a user might not be as threatening as leaked credentials for another user.
Exporting risk data
Data from Identity Protection can be exported to other tools for archive and further investigation and correlation. The Microsoft Graph based APIs allow organizations to collect this data for further processing in a tool such as their SIEM.
Question 2 Single Choice
Scenario: Café Rivoli is a restaurant in Manhattan that has a very exclusive clientele. Steve Rogers and Bruce Banner are the creators of this iconic restaurant and continue to strive to improve the business. Part of the improvements has been to implement Microsoft Azure into their business and have hired you to lead several projects in the company.
The IT team at Café Rivoli is having issues with getting "Your session has expired" error message before the Bastion session starts.
Which of the following can remedy the situation?
Explanation

Click "Show Answer" to see the explanation here
A session should be initiated only from the Azure portal. Sign into the Azure portal and begin your session again. If you go to the URL directly from another browser session or tab, this error is expected. It helps ensure that your session is more secure and that the session can be accessed only through the Azure portal.
Azure Bastion
Azure Bastion is a service you deploy that lets you connect to a virtual machine using your browser and the Azure portal. The Azure Bastion service is a fully platform-managed PaaS service that you provision inside your virtual network. It provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS. When you connect via Azure Bastion, your virtual machines do not need a public IP address, agent, or special client software.
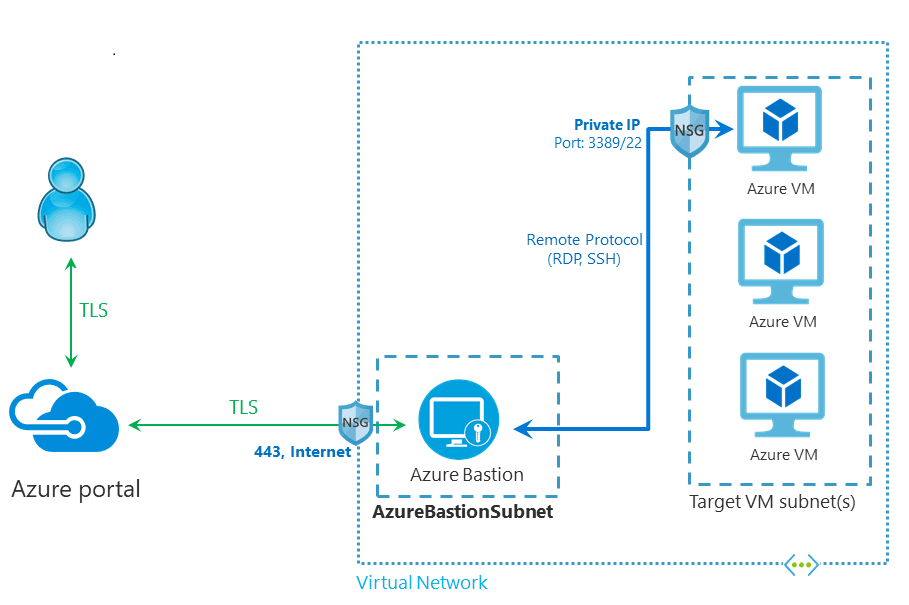
Bastion provides secure RDP and SSH connectivity to all of the VMs in the virtual network in which it is provisioned. Using Azure Bastion protects your virtual machines from exposing RDP/SSH ports to the outside world, while still providing secure access using RDP/SSH.
https://docs.microsoft.com/en-us/azure/bastion/bastion-overview
Explanation
A session should be initiated only from the Azure portal. Sign into the Azure portal and begin your session again. If you go to the URL directly from another browser session or tab, this error is expected. It helps ensure that your session is more secure and that the session can be accessed only through the Azure portal.
Azure Bastion
Azure Bastion is a service you deploy that lets you connect to a virtual machine using your browser and the Azure portal. The Azure Bastion service is a fully platform-managed PaaS service that you provision inside your virtual network. It provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS. When you connect via Azure Bastion, your virtual machines do not need a public IP address, agent, or special client software.

Bastion provides secure RDP and SSH connectivity to all of the VMs in the virtual network in which it is provisioned. Using Azure Bastion protects your virtual machines from exposing RDP/SSH ports to the outside world, while still providing secure access using RDP/SSH.
https://docs.microsoft.com/en-us/azure/bastion/bastion-overview
Question 3 Single Choice
Scenario: The Tivan Group is a prestigious and notoriously powerful group in the galactic community. Responsible for the founding of Knowhere, the Group is considerably wealthy and are often the source of exponential contributions to the galaxy. Taneleer Tivan, the infamous Collector, controls the group and is implementing Microsoft Azure into the company.
Taneleer has tasked his IT team with implementing a system which will provide Network Address Translation (NAT) services.
Which of the following will fit the need?
Explanation

Click "Show Answer" to see the explanation here
Azure Firewall - Azure Firewall provide Source Network Address Translation and Destination Network Address Translation.
Azure Firewall
Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. Using Azure Firewall, you can centrally create, enforce, and log application and network connectivity policies across subscriptions and virtual networks. Azure Firewall uses a static public IP address for your virtual network resources allowing outside firewalls to identify traffic originating from your virtual network.
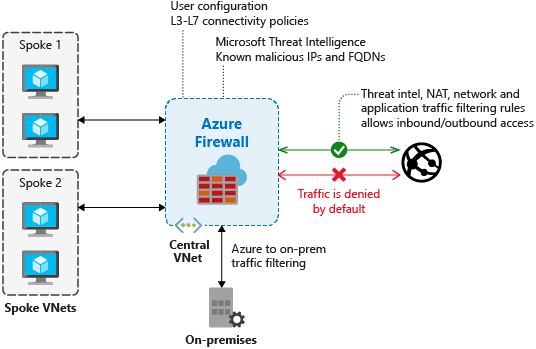
Azure Firewall includes the following features:
Built-in high availability
Availability Zones
Unrestricted cloud scalability
Application FQDN filtering rules
Network traffic filtering rules
FQDN tags
Service tags
Threat intelligence
Outbound SNAT support
Inbound DNAT support
Multiple public IP addresses
Azure Monitor logging
Forced tunneling
Web categories
Certifications
Built-in high availability
High availability is built in, so no extra load balancers are required and there's nothing you need to configure.
https://docs.microsoft.com/en-us/azure/firewall/features
Virtual network NAT Gateway
Virtual Network NAT (network address translation) simplifies outbound-only Internet connectivity for virtual networks. When configured on a subnet, all outbound connectivity uses your specified static public IP addresses. Outbound connectivity is possible without load balancer or public IP addresses directly attached to virtual machines.
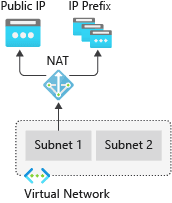
https://docs.microsoft.com/en-us/azure/networking/fundamentals/networking-overview
Explanation
Azure Firewall - Azure Firewall provide Source Network Address Translation and Destination Network Address Translation.
Azure Firewall
Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. Using Azure Firewall, you can centrally create, enforce, and log application and network connectivity policies across subscriptions and virtual networks. Azure Firewall uses a static public IP address for your virtual network resources allowing outside firewalls to identify traffic originating from your virtual network.

Azure Firewall includes the following features:
Built-in high availability
Availability Zones
Unrestricted cloud scalability
Application FQDN filtering rules
Network traffic filtering rules
FQDN tags
Service tags
Threat intelligence
Outbound SNAT support
Inbound DNAT support
Multiple public IP addresses
Azure Monitor logging
Forced tunneling
Web categories
Certifications
Built-in high availability
High availability is built in, so no extra load balancers are required and there's nothing you need to configure.
https://docs.microsoft.com/en-us/azure/firewall/features
Virtual network NAT Gateway
Virtual Network NAT (network address translation) simplifies outbound-only Internet connectivity for virtual networks. When configured on a subnet, all outbound connectivity uses your specified static public IP addresses. Outbound connectivity is possible without load balancer or public IP addresses directly attached to virtual machines.

https://docs.microsoft.com/en-us/azure/networking/fundamentals/networking-overview
Question 4 Single Choice
Scenario: Pennyworth’s Haberdashery has been around for over 50 years now and they have several stores in the Greater London area. They have just purchased a smaller clothier line based in Madrid and are integrating their systems with Pennyworth's Microsoft Power Platform service.
Alfred Pennyworth has hired you as a Microsoft Power Platform Expert for guidance on the merger of the systems.
Dick Grayson is a new member of the IT team in Pennyworth’s and is applying system updates.
Will this action likely increase Pennyworth’s security score in Azure Security Centre?
Explanation

Click "Show Answer" to see the explanation here
Yes – this action likely increase Pennyworth’s security score in Azure Security Centre.
System updates reduce security vulnerabilities and provide a more stable environment for end users. Not applying updates leaves unpatched vulnerabilities and results in environments that are susceptible to attacks.
Secure score in Azure Security Centre
Azure Security Centre has two main goals:
to help you understand your current security situation
to help you efficiently and effectively improve your security
The central feature in Security Centre that enables you to achieve those goals is secure score.
Security Centre continually assesses your resources, subscriptions, and organization for security issues. It then aggregates all the findings into a single score so that you can tell, at a glance, your current security situation: the higher the score, the lower the identified risk level.
The secure score is shown in the Azure portal pages as a percentage value, but the underlying values are also clearly presented:
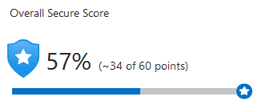
To increase your security, review Security Centre's recommendations page for the outstanding actions necessary to raise your score. Each recommendation includes instructions to help you remediate the specific issue.
Recommendations are grouped into security controls. Each control is a logical group of related security recommendations and reflects your vulnerable attack surfaces. Your score only improves when you remediate all of the recommendations for a single resource within a control. To see how well your organization is securing each individual attack surface, review the scores for each security control.
https://docs.microsoft.com/en-us/azure/security-center/secure-score-security-controls
Explanation
Yes – this action likely increase Pennyworth’s security score in Azure Security Centre.
System updates reduce security vulnerabilities and provide a more stable environment for end users. Not applying updates leaves unpatched vulnerabilities and results in environments that are susceptible to attacks.
Secure score in Azure Security Centre
Azure Security Centre has two main goals:
to help you understand your current security situation
to help you efficiently and effectively improve your security
The central feature in Security Centre that enables you to achieve those goals is secure score.
Security Centre continually assesses your resources, subscriptions, and organization for security issues. It then aggregates all the findings into a single score so that you can tell, at a glance, your current security situation: the higher the score, the lower the identified risk level.
The secure score is shown in the Azure portal pages as a percentage value, but the underlying values are also clearly presented:

To increase your security, review Security Centre's recommendations page for the outstanding actions necessary to raise your score. Each recommendation includes instructions to help you remediate the specific issue.
Recommendations are grouped into security controls. Each control is a logical group of related security recommendations and reflects your vulnerable attack surfaces. Your score only improves when you remediate all of the recommendations for a single resource within a control. To see how well your organization is securing each individual attack surface, review the scores for each security control.
https://docs.microsoft.com/en-us/azure/security-center/secure-score-security-controls
Question 5 Single Choice
Scenario: The Tivan Group is a prestigious and notoriously powerful group in the galactic community. Responsible for the founding of Knowhere, the Group is considerably wealthy and are often the source of exponential contributions to the galaxy. Taneleer Tivan, the infamous Collector, controls the group and is implementing Microsoft Azure into the company.
Taneleer wants to integrate the Azure Active Directory (Azure AD) feature which is used to provide just-in-time (JIT) access to manage Azure resources.
Which of the following should his IT team implement?
Explanation

Click "Show Answer" to see the explanation here
The IT team should implement Azure AD Privileged Identity Management (PIM) because it provides just-in-time privileged access to Azure AD and Azure resources.
Azure AD Privileged Identity Management
Privileged Identity Management (PIM) is a service in Azure Active Directory (Azure AD) that enables you to manage, control, and monitor access to important resources in your organization. These resources include resources in Azure AD, Azure, and other Microsoft Online Services such as Microsoft 365 or Microsoft Intune. The following video introduces you to important PIM concepts and features.
Privileged Identity Management provides time-based and approval-based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions on resources that you care about. Here are some of the key features of Privileged Identity Management:
Provide just-in-time privileged access to Azure AD and Azure resources
Assign time-bound access to resources using start and end dates
Require approval to activate privileged roles
Enforce multi-factor authentication to activate any role
Use justification to understand why users activate
Get notifications when privileged roles are activated
Conduct access reviews to ensure users still need roles
Download audit history for internal or external audit
Prevents removal of the last active Global Administrator role assignment
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
Explanation
The IT team should implement Azure AD Privileged Identity Management (PIM) because it provides just-in-time privileged access to Azure AD and Azure resources.
Azure AD Privileged Identity Management
Privileged Identity Management (PIM) is a service in Azure Active Directory (Azure AD) that enables you to manage, control, and monitor access to important resources in your organization. These resources include resources in Azure AD, Azure, and other Microsoft Online Services such as Microsoft 365 or Microsoft Intune. The following video introduces you to important PIM concepts and features.
Privileged Identity Management provides time-based and approval-based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions on resources that you care about. Here are some of the key features of Privileged Identity Management:
Provide just-in-time privileged access to Azure AD and Azure resources
Assign time-bound access to resources using start and end dates
Require approval to activate privileged roles
Enforce multi-factor authentication to activate any role
Use justification to understand why users activate
Get notifications when privileged roles are activated
Conduct access reviews to ensure users still need roles
Download audit history for internal or external audit
Prevents removal of the last active Global Administrator role assignment
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
Question 6 Single Choice
Scenario: The Eat-More Corporation is a U.S.-based fast-food restaurant chain headed by Teresa Payton. The main headquarters and processing plants of the Eat-More Corporation are located in Sedona, Arizona. Eat-More has restaurants located all over the United States and has plans to expand internationally. The expansion plans are underway and have presented several IT challenges which Teresa has contracted you to advise her IT staff on.
The IT team is planning to implement the Zero Trust model and you are conducting a workshop with the group.
Is “Control” a key privacy principle in Microsoft?
Explanation

Click "Show Answer" to see the explanation here
Microsoft’s products and services run on trust. Microsoft focuses on six key privacy principles when making decisions about data. Privacy is about making meaningful choices for how and why data is collected and used. It's about ensuring that you have the information you need to make the choices that are right for you, across all Microsoft products and services.
The six privacy principles are:
Control: Putting you, the customer, in control of your privacy with easy-to-use tools and clear choices.
Transparency: Being transparent about data collection and use so that everyone can make informed decisions.
Security: Protecting the data that's entrusted to Microsoft by using strong security and encryption.
Strong legal protections: Respecting local privacy laws and fighting for legal protection of privacy as a fundamental human right.
No content-based targeting: Not using email, chat, files, or other personal content to target advertising.
Benefits to you: When Microsoft does collect data, it's used to benefit you, the customer, and to make your experiences better.
These principles form Microsoft’s privacy foundation, and they shape the way that products and services are designed.
Explanation
Microsoft’s products and services run on trust. Microsoft focuses on six key privacy principles when making decisions about data. Privacy is about making meaningful choices for how and why data is collected and used. It's about ensuring that you have the information you need to make the choices that are right for you, across all Microsoft products and services.
The six privacy principles are:
Control: Putting you, the customer, in control of your privacy with easy-to-use tools and clear choices.
Transparency: Being transparent about data collection and use so that everyone can make informed decisions.
Security: Protecting the data that's entrusted to Microsoft by using strong security and encryption.
Strong legal protections: Respecting local privacy laws and fighting for legal protection of privacy as a fundamental human right.
No content-based targeting: Not using email, chat, files, or other personal content to target advertising.
Benefits to you: When Microsoft does collect data, it's used to benefit you, the customer, and to make your experiences better.
These principles form Microsoft’s privacy foundation, and they shape the way that products and services are designed.
Question 7 Single Choice
Scenario: The UCWF (Unlimited Class Wrestling Federation) was founded by a promoter named Edward Garner, who strives to use technology to improve his business and has come to you for assistance with the company’s Microsoft Azure service.
Garrison Kane is new to the UCWF and has been asked to use Advanced eDiscovery to help the legal team that is working on a case. What is the workflow Garrison will use?
Explanation

Click "Show Answer" to see the explanation here
The workflow will help you to get the best out of Advanced eDiscovery and is in line with common eDiscovery practices.
The core eDiscovery workflow
Core eDiscovery in Microsoft 365 provides a basic tool that organizations can use to search and export content in Microsoft 365.
To access Core eDiscovery or be added as a member of a Core eDiscovery case, a user must be assigned the appropriate permissions. Specifically, a user must be added as a member of the eDiscovery Manager role group in the Office 365 Security and Compliance Centre.
You start by creating an eDiscovery case, which starts from within Microsoft 365 compliance centre. When you create a case, you must specify a name for it and optionally define a case number. You can assign members to the case. From that point, the case will be displayed in the eDiscovery page and the user can step through the workflow.
The workflow consists of creating holds, searching for content, and exporting and downloading search results.

Create an eDiscovery hold
You can use an eDiscovery case to create a hold to preserve content that might be relevant to the case. You can place a hold on the Exchange mailboxes and OneDrive for Business accounts of people you're investigating in the case. You can also place a hold on the mailboxes and sites that are associated with Microsoft Teams, Office 365 Groups, and Yammer Groups. When you place content locations on hold, it's preserved until you remove the hold from the content location, or until you delete the hold.
It may take up to 24 hours after you create the hold for it to take effect.
You have two options to scope the content that's preserved:
You create an infinite hold where all content in the specified locations is placed on hold. Or you can create a query-based hold where only the content in the specified locations that matches a search query is placed on hold.
You can specify a date range to preserve only the content that was sent, received, or created within that date range. Or you can hold all content in specified locations regardless of when it was sent, received, or created.
Search for content in the case
When you've placed a hold, you can create and run searches for content that relates to the case. You start the search from within the home page for that specific case. Searches associated with a case can only be accessed by members assigned to it.
You can specify keywords, message properties such as sent and received dates, or document properties such as file names, or the date a document was last changed. You can use Boolean operators such as AND, OR, NOT, or NEAR. You can also search for sensitive information (for example, social security numbers) in documents, or search for documents that have been shared externally. If you don't specify keywords, all content located in the specified content locations will be included in the search results.
Export content from a case
You can export search results. Mailbox items are downloaded in a PST file or as individual messages. Content from SharePoint, OneDrive for Business sites, copies of native Office documents, and other documents are exported. A Results.csv file that contains information about every item that's exported and a manifest file (in XML format) that contains information about every search result is also exported.
You can export the results of both a single search or results from multiple searches associated with a case.
Close, reopen, and delete a core eDiscovery case
Core eDiscovery cases can be closed when the investigations or legal cases they were supporting have been completed. When a case is closed, any holds associated with it will be turned off. Once turned off, there’s a 30-day grace period (referred to as a delay hold) on the content locations that were on hold. This helps ensure that content isn’t deleted immediately and gives admins the chance to look for and restore any content before it's deleted permanently.
The main difference between an active and closed case is that eDiscovery holds are turned off for a closed case. When you reopen a closed case, any holds that were in place when it was closed, won’t be reinstated automatically. After reopening the case, you’ll need to turn on previous holds. A reopened case will have its status changed from closed to active.
You can delete both active and closed cases. If you delete a case, all searches and exports in that case are also deleted, the case is removed from the list in the Microsoft 365 compliance centre. The deleted case can’t be reopened.
If the case you want to delete contains eDiscovery holds, you can't delete it. You’ll need to delete all the holds linked to the case then try to delete it again.
Explanation
The workflow will help you to get the best out of Advanced eDiscovery and is in line with common eDiscovery practices.
The core eDiscovery workflow
Core eDiscovery in Microsoft 365 provides a basic tool that organizations can use to search and export content in Microsoft 365.
To access Core eDiscovery or be added as a member of a Core eDiscovery case, a user must be assigned the appropriate permissions. Specifically, a user must be added as a member of the eDiscovery Manager role group in the Office 365 Security and Compliance Centre.
You start by creating an eDiscovery case, which starts from within Microsoft 365 compliance centre. When you create a case, you must specify a name for it and optionally define a case number. You can assign members to the case. From that point, the case will be displayed in the eDiscovery page and the user can step through the workflow.
The workflow consists of creating holds, searching for content, and exporting and downloading search results.

Create an eDiscovery hold
You can use an eDiscovery case to create a hold to preserve content that might be relevant to the case. You can place a hold on the Exchange mailboxes and OneDrive for Business accounts of people you're investigating in the case. You can also place a hold on the mailboxes and sites that are associated with Microsoft Teams, Office 365 Groups, and Yammer Groups. When you place content locations on hold, it's preserved until you remove the hold from the content location, or until you delete the hold.
It may take up to 24 hours after you create the hold for it to take effect.
You have two options to scope the content that's preserved:
You create an infinite hold where all content in the specified locations is placed on hold. Or you can create a query-based hold where only the content in the specified locations that matches a search query is placed on hold.
You can specify a date range to preserve only the content that was sent, received, or created within that date range. Or you can hold all content in specified locations regardless of when it was sent, received, or created.
Search for content in the case
When you've placed a hold, you can create and run searches for content that relates to the case. You start the search from within the home page for that specific case. Searches associated with a case can only be accessed by members assigned to it.
You can specify keywords, message properties such as sent and received dates, or document properties such as file names, or the date a document was last changed. You can use Boolean operators such as AND, OR, NOT, or NEAR. You can also search for sensitive information (for example, social security numbers) in documents, or search for documents that have been shared externally. If you don't specify keywords, all content located in the specified content locations will be included in the search results.
Export content from a case
You can export search results. Mailbox items are downloaded in a PST file or as individual messages. Content from SharePoint, OneDrive for Business sites, copies of native Office documents, and other documents are exported. A Results.csv file that contains information about every item that's exported and a manifest file (in XML format) that contains information about every search result is also exported.
You can export the results of both a single search or results from multiple searches associated with a case.
Close, reopen, and delete a core eDiscovery case
Core eDiscovery cases can be closed when the investigations or legal cases they were supporting have been completed. When a case is closed, any holds associated with it will be turned off. Once turned off, there’s a 30-day grace period (referred to as a delay hold) on the content locations that were on hold. This helps ensure that content isn’t deleted immediately and gives admins the chance to look for and restore any content before it's deleted permanently.
The main difference between an active and closed case is that eDiscovery holds are turned off for a closed case. When you reopen a closed case, any holds that were in place when it was closed, won’t be reinstated automatically. After reopening the case, you’ll need to turn on previous holds. A reopened case will have its status changed from closed to active.
You can delete both active and closed cases. If you delete a case, all searches and exports in that case are also deleted, the case is removed from the list in the Microsoft 365 compliance centre. The deleted case can’t be reopened.
If the case you want to delete contains eDiscovery holds, you can't delete it. You’ll need to delete all the holds linked to the case then try to delete it again.
Question 8 Single Choice
Identify the missing word(s) in the following sentence within the context of Microsoft Azure.
[?] is a managed, cloud-based network security service that protects your Azure virtual network (VNet) resources from attackers. You can deploy [?] on any virtual network, but the best approach is to use it on a centralized virtual network.
Explanation

Click "Show Answer" to see the explanation here
Azure Firewall
Azure Firewall is a managed, cloud-based network security service that protects your Azure virtual network (VNet) resources from attackers. You can deploy Azure Firewall on any virtual network, but the best approach is to use it on a centralized virtual network. All your other virtual and on-premises networks will then route through it. The advantage of this model is the ability to centrally exert control of network traffic for all your VNets across different subscriptions.
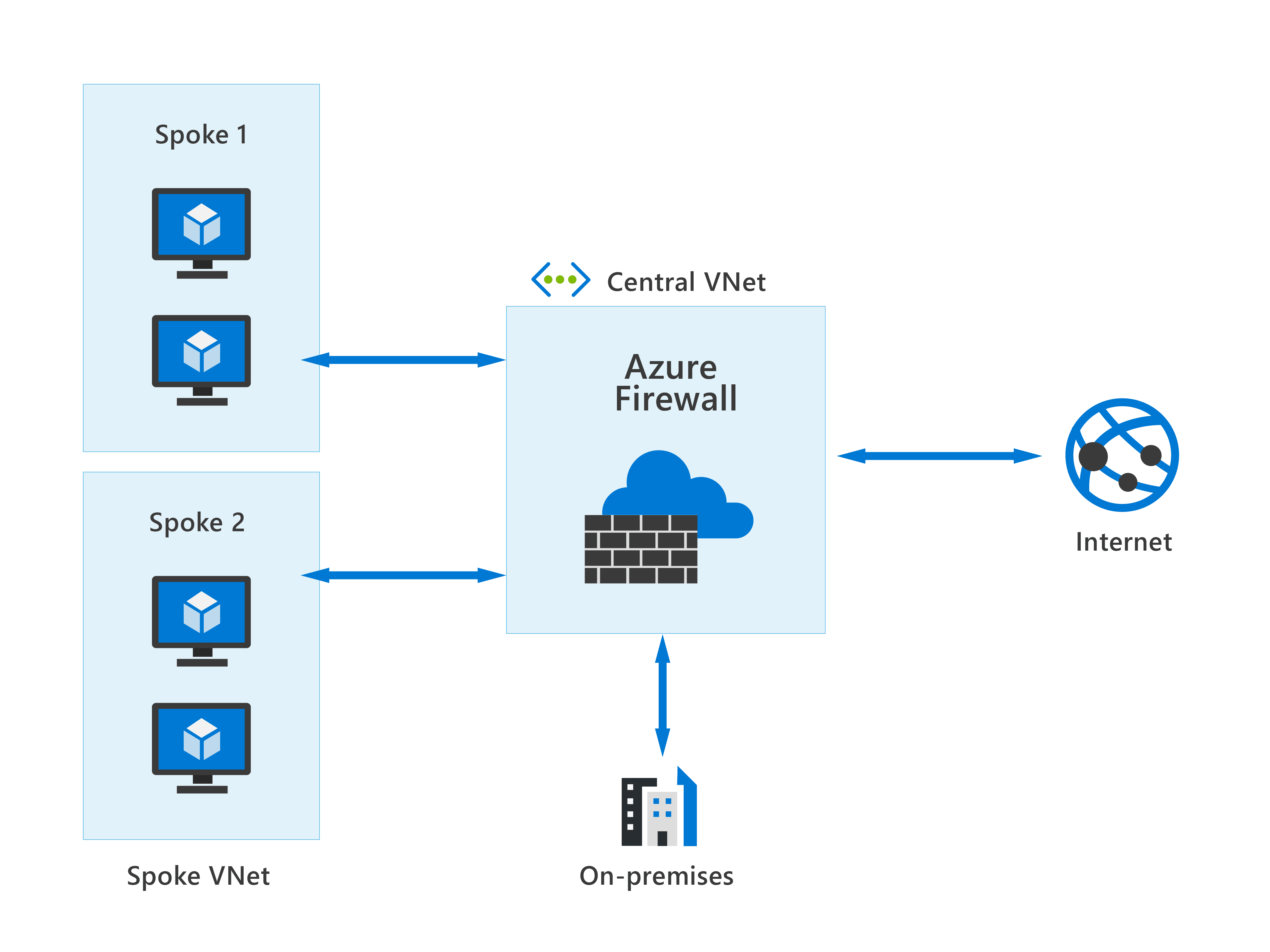
With Azure Firewall, you can scale up the usage to accommodate changing network traffic flows, so you don't need to budget for peak traffic. Network traffic is subjected to the configured firewall rules when you route it to the firewall as the subnet default gateway.
Key features of Azure Firewall
Azure Firewall comes with many features, including but not limited to:
Built-in high availability and availability zones: High availability is built in so there's nothing to configure. Also, Azure Firewall can be configured to span multiple availability zones for increased availability.
Network and application-level filtering: Use IP address, port, and protocol to support fully qualified domain name filtering for outbound HTTP(s) traffic and network filtering controls.
Outbound SNAT and inbound DNAT to communicate with internet resources: Translates the private IP address of network resources to an Azure public IP address (source network address translation) to identify and allow traffic originating from the virtual network to internet destinations. Similarly, inbound internet traffic to the firewall public IP address is translated (Destination Network Address Translation) and filtered to the private IP addresses of resources on the virtual network.
Multiple public IP addresses: These addresses can be associated with Azure Firewall.
Threat intelligence: Threat intelligence-based filtering can be enabled for your firewall to alert and deny traffic from/to known malicious IP addresses and domains.
Integration with Azure Monitor: Integrated with Azure Monitor to enable collecting, analyzing, and acting on telemetry from Azure Firewall logs.
Use Azure Firewall to help protect the Azure resources you've connected to Azure Virtual Networks.
https://docs.microsoft.com/en-us/azure/storage/common/storage-network-security?tabs=azure-portal
Explanation
Azure Firewall
Azure Firewall is a managed, cloud-based network security service that protects your Azure virtual network (VNet) resources from attackers. You can deploy Azure Firewall on any virtual network, but the best approach is to use it on a centralized virtual network. All your other virtual and on-premises networks will then route through it. The advantage of this model is the ability to centrally exert control of network traffic for all your VNets across different subscriptions.

With Azure Firewall, you can scale up the usage to accommodate changing network traffic flows, so you don't need to budget for peak traffic. Network traffic is subjected to the configured firewall rules when you route it to the firewall as the subnet default gateway.
Key features of Azure Firewall
Azure Firewall comes with many features, including but not limited to:
Built-in high availability and availability zones: High availability is built in so there's nothing to configure. Also, Azure Firewall can be configured to span multiple availability zones for increased availability.
Network and application-level filtering: Use IP address, port, and protocol to support fully qualified domain name filtering for outbound HTTP(s) traffic and network filtering controls.
Outbound SNAT and inbound DNAT to communicate with internet resources: Translates the private IP address of network resources to an Azure public IP address (source network address translation) to identify and allow traffic originating from the virtual network to internet destinations. Similarly, inbound internet traffic to the firewall public IP address is translated (Destination Network Address Translation) and filtered to the private IP addresses of resources on the virtual network.
Multiple public IP addresses: These addresses can be associated with Azure Firewall.
Threat intelligence: Threat intelligence-based filtering can be enabled for your firewall to alert and deny traffic from/to known malicious IP addresses and domains.
Integration with Azure Monitor: Integrated with Azure Monitor to enable collecting, analyzing, and acting on telemetry from Azure Firewall logs.
Use Azure Firewall to help protect the Azure resources you've connected to Azure Virtual Networks.
https://docs.microsoft.com/en-us/azure/storage/common/storage-network-security?tabs=azure-portal
Question 9 Single Choice
Scenario: You have been contracted by Wayne Enterprises, a company owned by Bruce Wayne with a market value of over twenty-seven million dollars. Bruce founded Wayne Enterprises shortly after he created the Wayne Foundation and he became the president and chairman of the company.
Bruce has come to you because his IT team needs direction. All users in Wayne Enterprises have Microsoft 365 cloud identities.
Which identity model applies?
Explanation

Click "Show Answer" to see the explanation here
When all your users have cloud identities, you use the cloud-only model.
The concept of hybrid identities
Organizations may use the hybrid identity model, or the cloud-only identity model. In the hybrid model, identities are created in Windows Active Directory or another identity provider, and then synchronized to Azure AD. In the cloud-only model, identities are created and wholly managed in Azure AD. Whether identities are created on-premises or in the cloud, users can access both cloud and on-premises resources.
With the hybrid model, users accessing both on-premises and cloud apps are hybrid users managed in the on-premises Active Directory. When you make an update in your on-premises AD DS, all updates to user accounts, groups, and contacts are synchronized to your Azure AD. The synchronization is managed with Azure AD Connect.
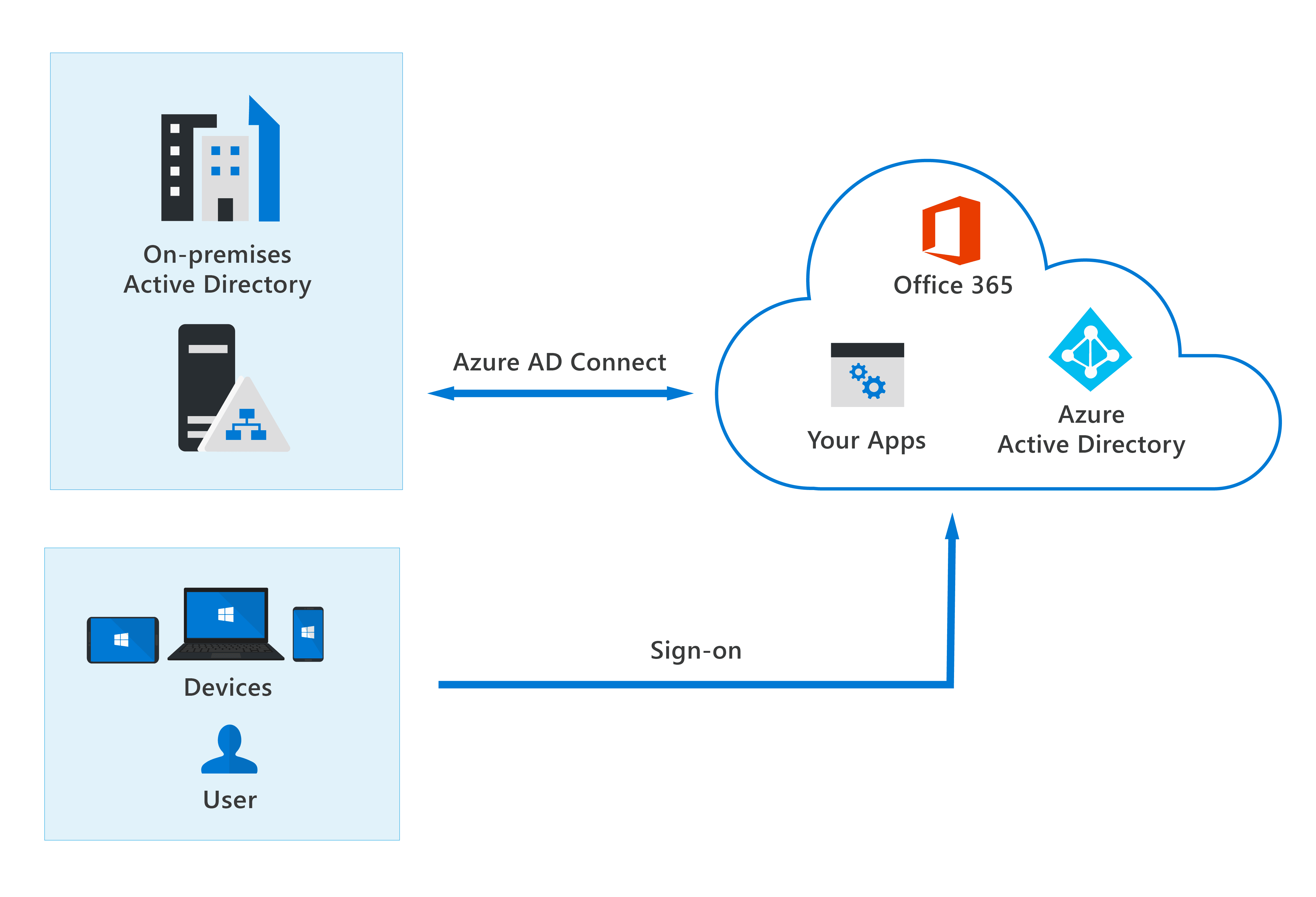
When using the hybrid model, authentication can either be done by Azure AD, which is known as managed authentication, or Azure AD redirects the client requesting authentication to another identity provider, which is known as federated authentication.
One of three authentication methods can be used:
• Password hash synchronization. The simplest way to enable authentication for on-premises directory objects in Azure AD. Users have the same username and password that they use on-premises without any other infrastructure required.
• Pass-through authentication (PTA). Provides a simple password validation for Azure AD authentication services by using a software agent that runs on one or more on-premises servers. The servers validate the users directly with an on-premises Active Directory, which ensures that the password validation doesn't happen in the cloud.
• Federated authentication. Azure AD hands off the authentication process to a separate trusted authentication system, such as on-premises Active Directory Federation Services (AD FS), to validate the user’s password.
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-hybrid-identity
Explanation
When all your users have cloud identities, you use the cloud-only model.
The concept of hybrid identities
Organizations may use the hybrid identity model, or the cloud-only identity model. In the hybrid model, identities are created in Windows Active Directory or another identity provider, and then synchronized to Azure AD. In the cloud-only model, identities are created and wholly managed in Azure AD. Whether identities are created on-premises or in the cloud, users can access both cloud and on-premises resources.
With the hybrid model, users accessing both on-premises and cloud apps are hybrid users managed in the on-premises Active Directory. When you make an update in your on-premises AD DS, all updates to user accounts, groups, and contacts are synchronized to your Azure AD. The synchronization is managed with Azure AD Connect.

When using the hybrid model, authentication can either be done by Azure AD, which is known as managed authentication, or Azure AD redirects the client requesting authentication to another identity provider, which is known as federated authentication.
One of three authentication methods can be used:
• Password hash synchronization. The simplest way to enable authentication for on-premises directory objects in Azure AD. Users have the same username and password that they use on-premises without any other infrastructure required.
• Pass-through authentication (PTA). Provides a simple password validation for Azure AD authentication services by using a software agent that runs on one or more on-premises servers. The servers validate the users directly with an on-premises Active Directory, which ensures that the password validation doesn't happen in the cloud.
• Federated authentication. Azure AD hands off the authentication process to a separate trusted authentication system, such as on-premises Active Directory Federation Services (AD FS), to validate the user’s password.
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-hybrid-identity
Question 10 Single Choice
Scenario: The Serpent Society is a business enterprise considered one of the best-organized, most successful sector coalitions in operation today. Seth Voelker is the founder of the Society and has come to you for assistance as a Microsoft Azure Expert.
Peter Parker is the compliance admin for the Serpent Society and is required to comply with corporate policies, and therefore needs to be able to identify and scan for offensive language across the organization.
Which of the following solutions would you suggest to Peter to implement to address this need?
Explanation

Click "Show Answer" to see the explanation here
Communication Compliance helps minimize communication risks by enabling you to detect, capture, and take remediation actions for inappropriate messages in the organization.
Communication compliance
Communication compliance in Microsoft 365 compliance centre helps minimize communication risks by enabling organizations to detect, capture, and take remediation actions for inappropriate messages. Predefined and custom policies in communication compliance make it possible to scan internal and external communications for policy matches so they can be examined by chosen reviewers.
Identifying and resolving compliance issues with communication compliance in Microsoft 365 uses the following workflow:
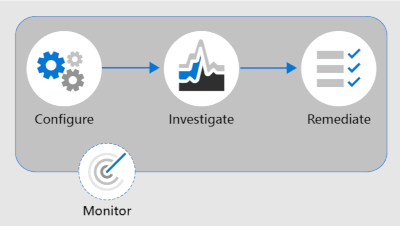
Configure – in this step, admins identify compliance requirements and configure applicable communication compliance policies.
Investigate – admins look deeper into the issues detected when matching your communication compliance policies. Tools and steps that help include alerts, issue management to help remediation, document reviews, reviewing user history, and filters.
Remediate – remediate communications compliance issues. Options include resolving an alert, tagging a message, notifying the user, escalating to another reviewer, marking an alert as a false positive, removing a message in Teams, and escalating for investigation.
Monitor – Keeping track and managing compliance issues identified by communication compliance policies spans the entire workflow process. Communication compliance dashboard widgets, export logs, and events recorded in the unified audit logs can be used to continually evaluate and improve your compliance posture.
Communication compliance enables reviewers to investigate scanned emails, and messages across Microsoft Teams, Exchange Online, Yammer, or third-party communications in an organization, taking appropriate remediation actions to make sure they're compliant with the organization's message standards.
Some important compliance areas where communication compliance policies can assist with reviewing messages include:
Corporate policies - Users have to follow corporate policies like usage and ethical standards in their day-to-day business communications. With communication compliance, admins can scan user communications across the organization for potential concerns of offensive language or harassment.
Risk management - Communication compliance can help admins scan for unauthorized communication about projects that are considered to be confidential, such as acquisitions, earnings disclosures, and more.
Regulatory compliance - Most organizations are expected to follow some regulatory compliance standards during their day-to-day operations. For example, a regulation might require organizations to review communications of its brokers to safeguard against potential insider trading, money laundering, or bribery. Communication compliance enables the organization to scan and report on these types of communications in a way that meets their requirements.
https://www.microsoft.com/en-ca/videoplayer/embed/RE4xlaF?postJsllMsg=true&autoCaptions=en-ca
Communication compliance is a powerful tool, that can help maintain and safeguard your staff, your data and your organization.
Explanation
Communication Compliance helps minimize communication risks by enabling you to detect, capture, and take remediation actions for inappropriate messages in the organization.
Communication compliance
Communication compliance in Microsoft 365 compliance centre helps minimize communication risks by enabling organizations to detect, capture, and take remediation actions for inappropriate messages. Predefined and custom policies in communication compliance make it possible to scan internal and external communications for policy matches so they can be examined by chosen reviewers.
Identifying and resolving compliance issues with communication compliance in Microsoft 365 uses the following workflow:

Configure – in this step, admins identify compliance requirements and configure applicable communication compliance policies.
Investigate – admins look deeper into the issues detected when matching your communication compliance policies. Tools and steps that help include alerts, issue management to help remediation, document reviews, reviewing user history, and filters.
Remediate – remediate communications compliance issues. Options include resolving an alert, tagging a message, notifying the user, escalating to another reviewer, marking an alert as a false positive, removing a message in Teams, and escalating for investigation.
Monitor – Keeping track and managing compliance issues identified by communication compliance policies spans the entire workflow process. Communication compliance dashboard widgets, export logs, and events recorded in the unified audit logs can be used to continually evaluate and improve your compliance posture.
Communication compliance enables reviewers to investigate scanned emails, and messages across Microsoft Teams, Exchange Online, Yammer, or third-party communications in an organization, taking appropriate remediation actions to make sure they're compliant with the organization's message standards.
Some important compliance areas where communication compliance policies can assist with reviewing messages include:
Corporate policies - Users have to follow corporate policies like usage and ethical standards in their day-to-day business communications. With communication compliance, admins can scan user communications across the organization for potential concerns of offensive language or harassment.
Risk management - Communication compliance can help admins scan for unauthorized communication about projects that are considered to be confidential, such as acquisitions, earnings disclosures, and more.
Regulatory compliance - Most organizations are expected to follow some regulatory compliance standards during their day-to-day operations. For example, a regulation might require organizations to review communications of its brokers to safeguard against potential insider trading, money laundering, or bribery. Communication compliance enables the organization to scan and report on these types of communications in a way that meets their requirements.
https://www.microsoft.com/en-ca/videoplayer/embed/RE4xlaF?postJsllMsg=true&autoCaptions=en-ca
Communication compliance is a powerful tool, that can help maintain and safeguard your staff, your data and your organization.