Microsoft Certified: Security, Compliance, and Identity Fundamentals - (SC-900) Exam Questions
Total Questions
Last Updated
1st Try Guaranteed

Experts Verified
Question 11 Single Choice
Scenario: Café Rivoli is a restaurant in Manhattan that has a very exclusive clientele. Steve Rogers and Bruce Banner are the creators of this iconic restaurant and continue to strive to improve the business. Part of the improvements has been to implement Microsoft Azure into their business and have hired you to lead several projects in the company.
One of the projects in-flight is compliance related. Upon running the Compliance Manager, the analysis came back with a high score. Bruce believes that the high score confirms the company is fully compliant. Steve does not believe this is completely accurate.
If Café Rivoli has a high score, does it mean the company is fully compliant?
Explanation

Click "Show Answer" to see the explanation here
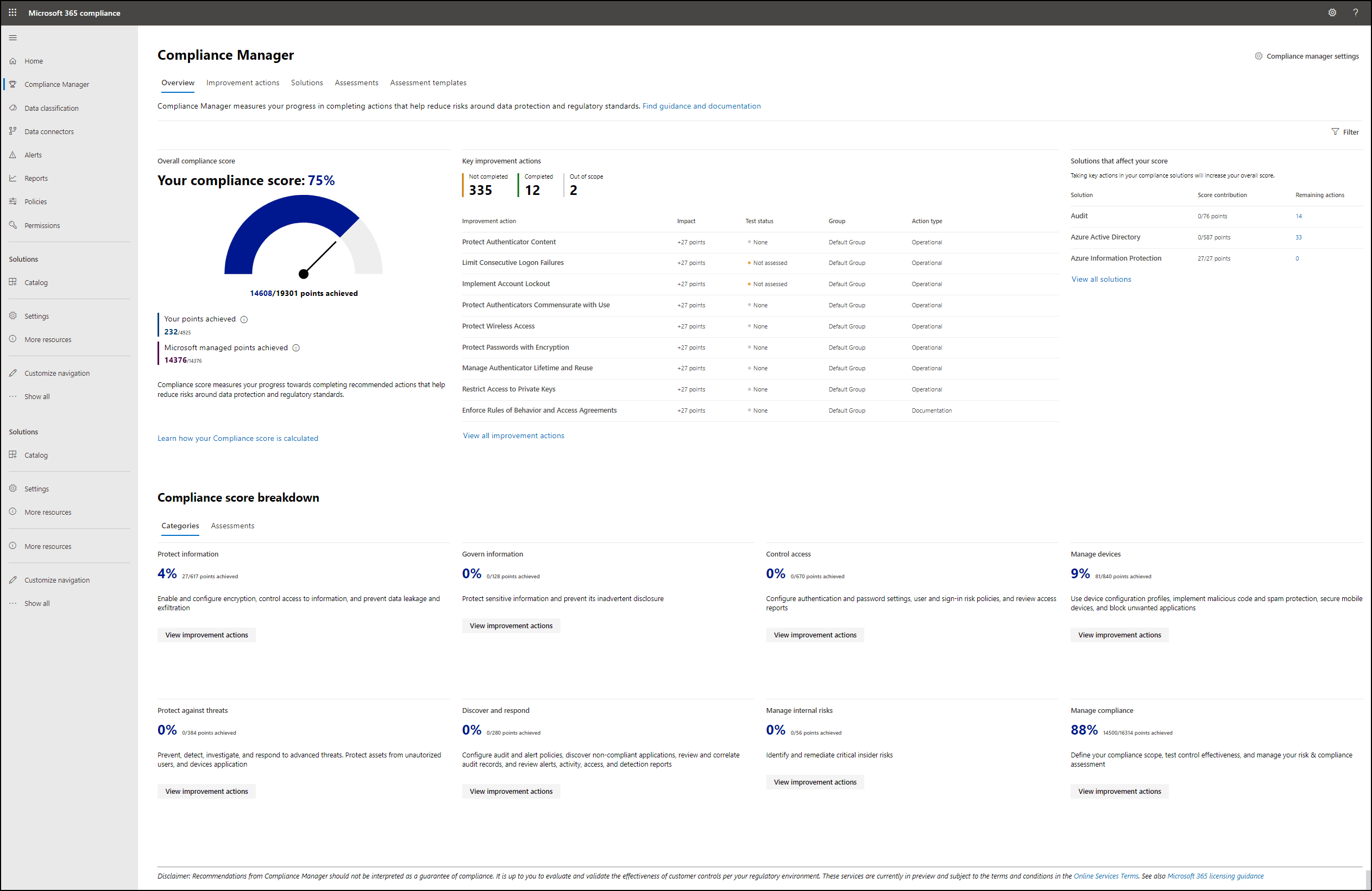
No - Your compliance score measures your progress in completing recommended actions that help reduce risks around data protection and regulatory standards. It does not express an absolute measure of organizational compliance with regard to a particular standard or regulation. Compliance Manager, and your compliance score, should not be interpreted as a guarantee in any way.
Microsoft Compliance Manager
Microsoft Compliance Manager is a feature in the Microsoft 365 compliance centre that helps you manage your organization’s compliance requirements with greater ease and convenience. Compliance Manager can help you throughout your compliance journey, from taking inventory of your data protection risks to managing the complexities of implementing controls, staying current with regulations and certifications, and reporting to auditors.
https://www.microsoft.com/en-us/videoplayer/embed/RE4FGYZ
Compliance Manager helps simplify compliance and reduce risk by providing:
• Pre-built assessments for common industry and regional standards and regulations, or custom assessments to meet your unique compliance needs (available assessments depend on your licensing agreement; learn more).
• Workflow capabilities to help you efficiently complete your risk assessments through a single tool.
• Detailed step-by-step guidance on suggested improvement actions to help you comply with the standards and regulations that are most relevant for your organization. For actions that are managed by Microsoft, you’ll see implementation details and audit results.
• A risk-based compliance score to help you understand your compliance posture by measuring your progress in completing improvement actions.
Your Compliance Manager dashboard shows your current compliance score, helps you see what needs attention, and guides you to key improvement actions. Below is an example of what your Compliance Manager dashboard will look like:
https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-manager?view=o365-worldwide
Explanation
No - Your compliance score measures your progress in completing recommended actions that help reduce risks around data protection and regulatory standards. It does not express an absolute measure of organizational compliance with regard to a particular standard or regulation. Compliance Manager, and your compliance score, should not be interpreted as a guarantee in any way.
Microsoft Compliance Manager
Microsoft Compliance Manager is a feature in the Microsoft 365 compliance centre that helps you manage your organization’s compliance requirements with greater ease and convenience. Compliance Manager can help you throughout your compliance journey, from taking inventory of your data protection risks to managing the complexities of implementing controls, staying current with regulations and certifications, and reporting to auditors.

https://www.microsoft.com/en-us/videoplayer/embed/RE4FGYZ
Compliance Manager helps simplify compliance and reduce risk by providing:
• Pre-built assessments for common industry and regional standards and regulations, or custom assessments to meet your unique compliance needs (available assessments depend on your licensing agreement; learn more).
• Workflow capabilities to help you efficiently complete your risk assessments through a single tool.
• Detailed step-by-step guidance on suggested improvement actions to help you comply with the standards and regulations that are most relevant for your organization. For actions that are managed by Microsoft, you’ll see implementation details and audit results.
• A risk-based compliance score to help you understand your compliance posture by measuring your progress in completing improvement actions.
Your Compliance Manager dashboard shows your current compliance score, helps you see what needs attention, and guides you to key improvement actions. Below is an example of what your Compliance Manager dashboard will look like:

https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-manager?view=o365-worldwide
Question 12 Single Choice
Identify the missing word(s) in the following sentence within the context of Microsoft Azure.
The Microsoft Defender portal includes a Reports section that includes a general security report, reports related to endpoints, and reports related to email and collaboration.
The [?] enables admins to view information about security trends and track the protection status of your identities, data, devices, apps, and infrastructure.
Explanation

Click "Show Answer" to see the explanation here
The general security report enables admins to view information about security trends and track the protection status of your identities, data, devices, apps, and infrastructure.
Security reports and dashboards
The Microsoft Defender portal includes a Reports section that includes a general security report, reports related to endpoints, and reports related to email and collaboration.
Security report
The general security report enables admins to view information about security trends and track the protection status of your identities, data, devices, apps, and infrastructure.
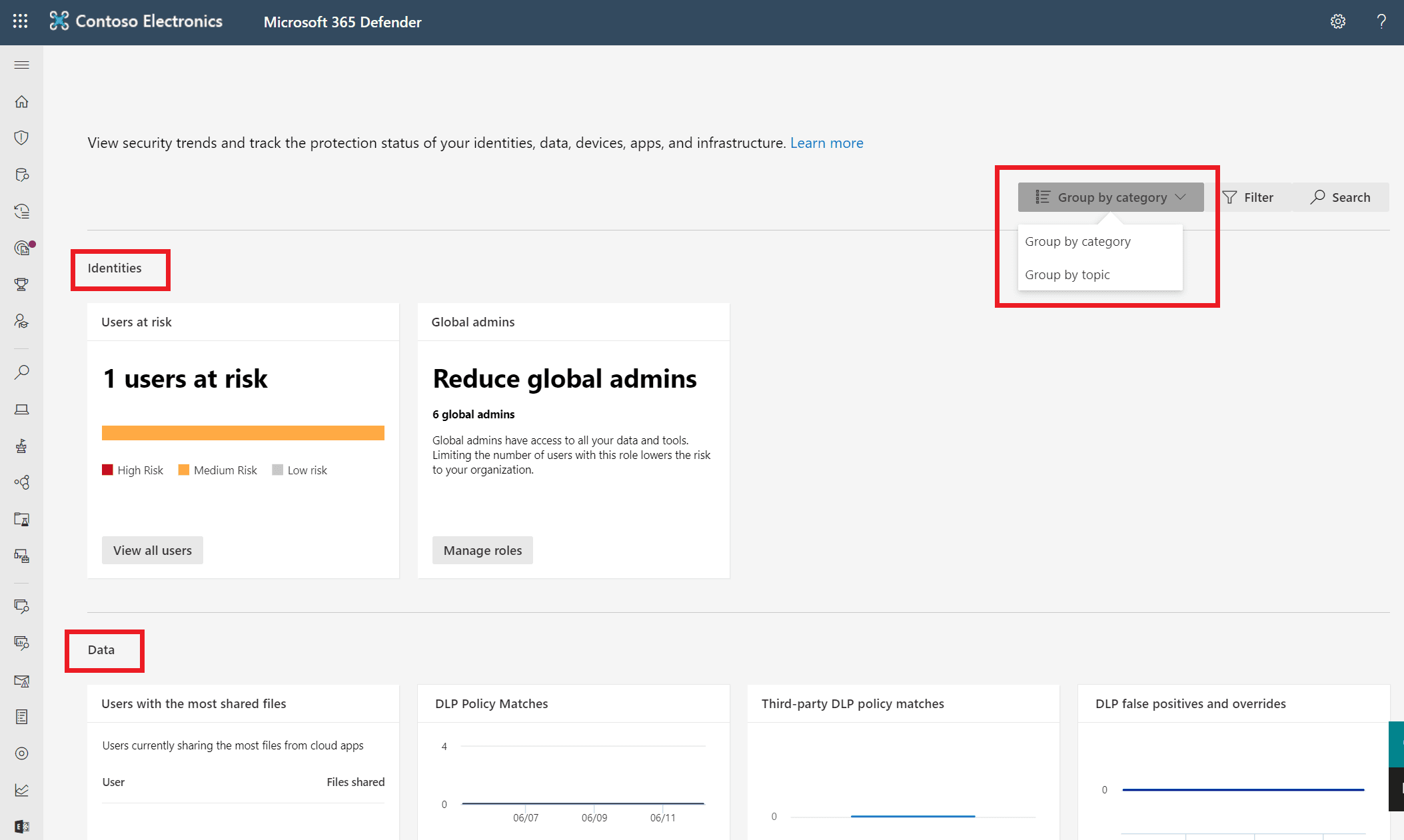
By default, cards are grouped by the following categories:
Identities - user accounts and credentials.
Data - email and document contents.
Devices - computers, mobile phones, and other devices.
Apps - programs and attached online services.
In the example below, the cards are grouped by category (only two of the four categories are shown in the image).
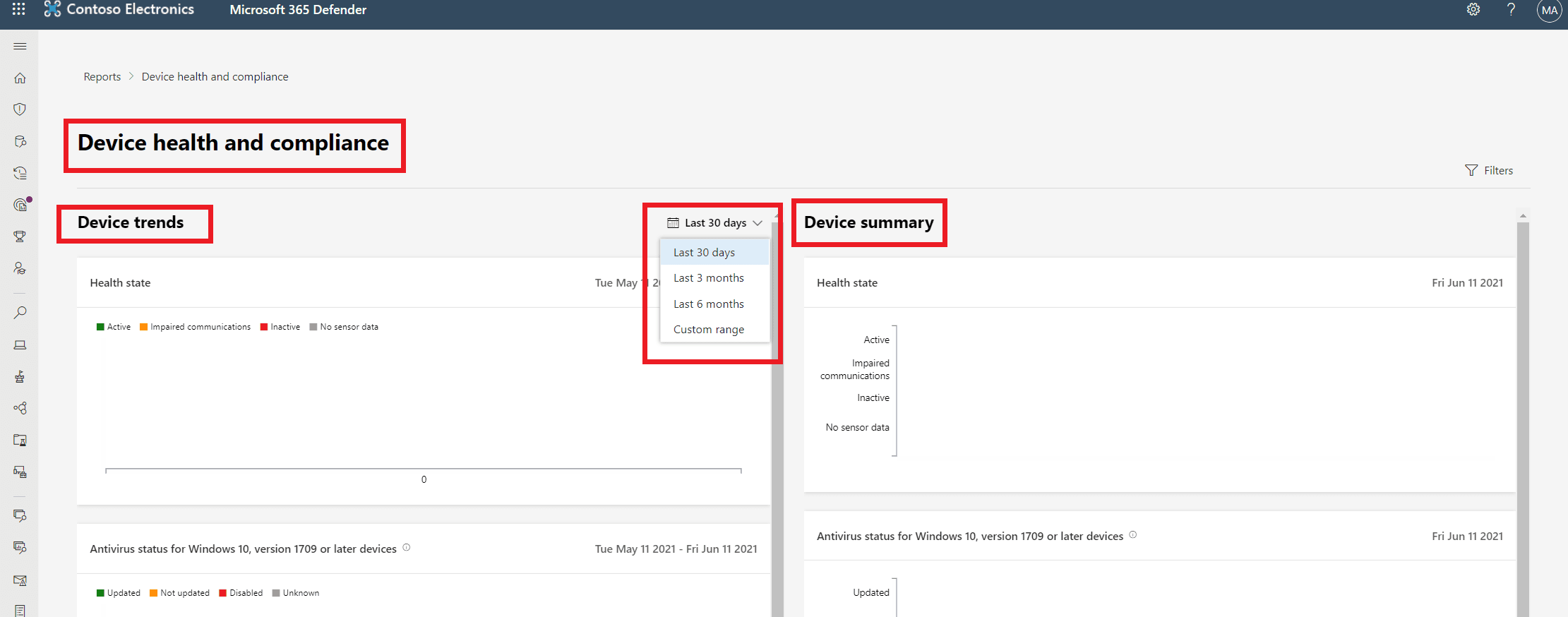
The device health and compliance report enables admins to monitor the health state, antivirus status, operating system platforms, and Windows 10 versions for devices in your organization.
This report's dashboard is also structured into two sections:
Device trends - By default, the device trends displays device information from the 30-day period ending in the latest full day. To gain better perspective on trends occurring in your organization, you can fine-tune the reporting period by adjusting the time period.
Device summary - The device summary shows device information scoped to the current day.
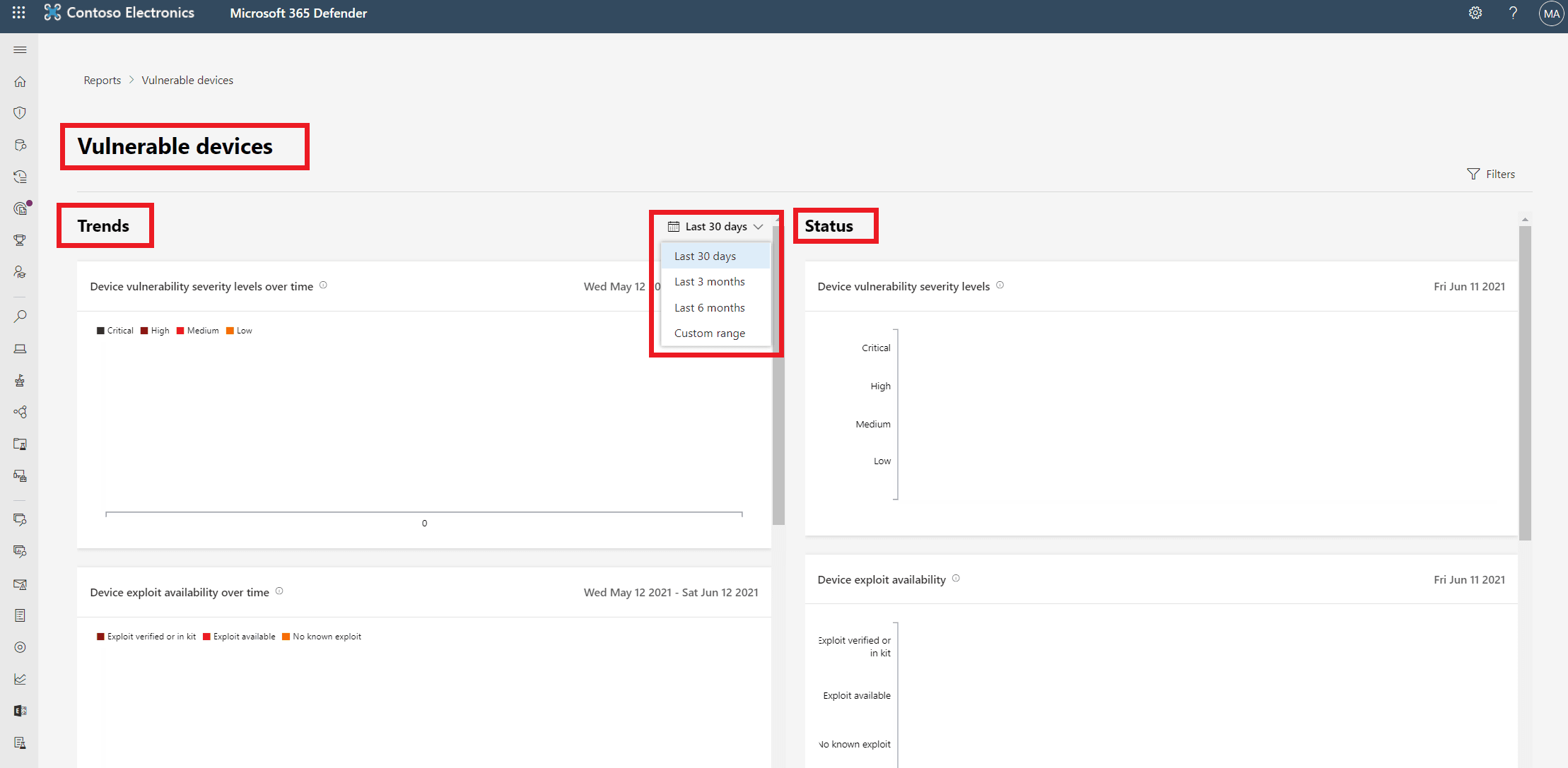
The vulnerable devices report enables admins to view information about the vulnerable devices in your organization, including their exposure to vulnerabilities by severity level, exploitability, age, and more.
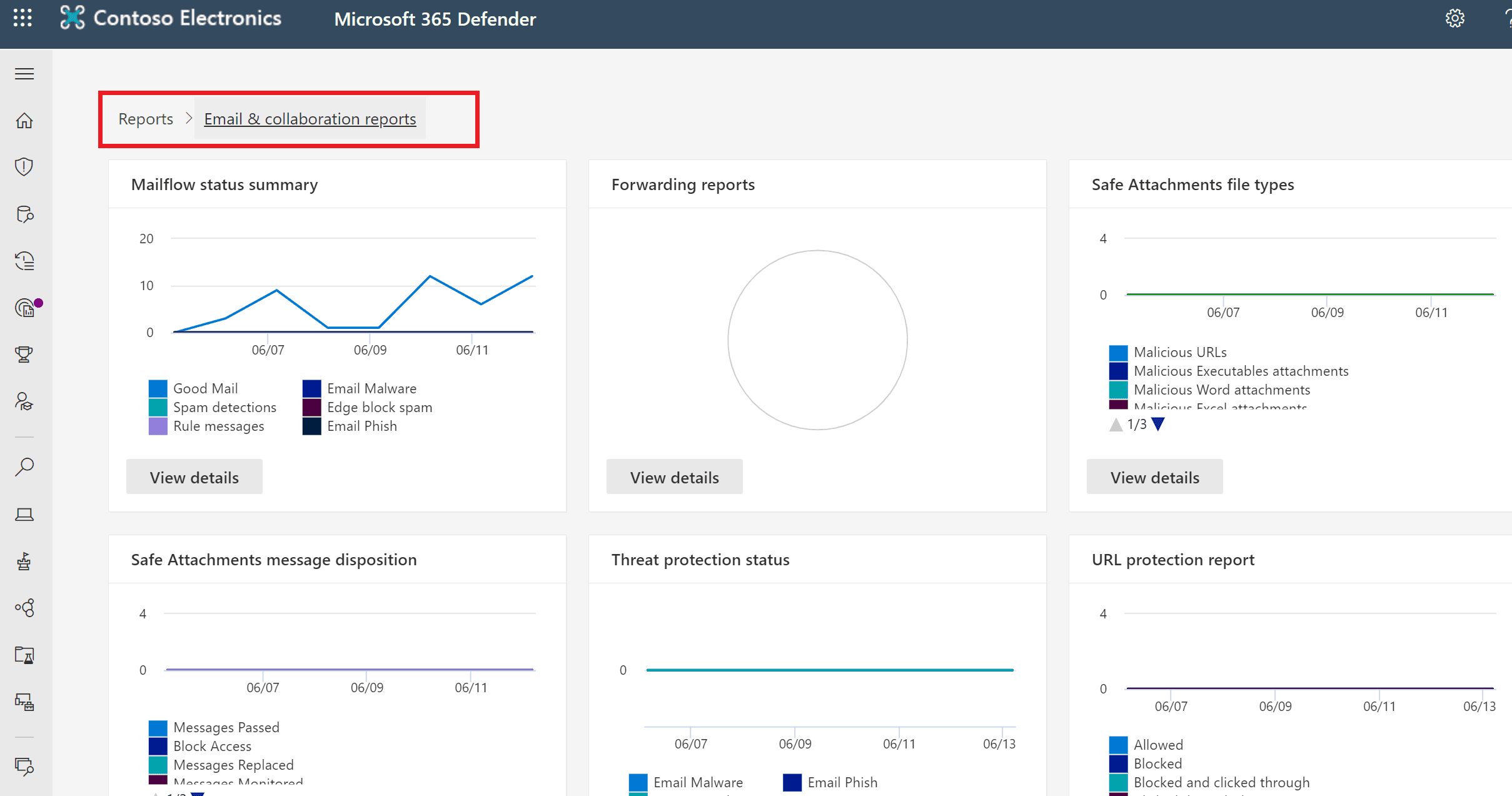
Email and collaboration reports
The email and collaboration reports enable admins to review Microsoft recommended actions to help improve email and collaboration security.
Explanation
The general security report enables admins to view information about security trends and track the protection status of your identities, data, devices, apps, and infrastructure.
Security reports and dashboards
The Microsoft Defender portal includes a Reports section that includes a general security report, reports related to endpoints, and reports related to email and collaboration.

Security report
The general security report enables admins to view information about security trends and track the protection status of your identities, data, devices, apps, and infrastructure.
By default, cards are grouped by the following categories:
Identities - user accounts and credentials.
Data - email and document contents.
Devices - computers, mobile phones, and other devices.
Apps - programs and attached online services.
In the example below, the cards are grouped by category (only two of the four categories are shown in the image).

The device health and compliance report enables admins to monitor the health state, antivirus status, operating system platforms, and Windows 10 versions for devices in your organization.
This report's dashboard is also structured into two sections:
Device trends - By default, the device trends displays device information from the 30-day period ending in the latest full day. To gain better perspective on trends occurring in your organization, you can fine-tune the reporting period by adjusting the time period.
Device summary - The device summary shows device information scoped to the current day.

The vulnerable devices report enables admins to view information about the vulnerable devices in your organization, including their exposure to vulnerabilities by severity level, exploitability, age, and more.

Email and collaboration reports
The email and collaboration reports enable admins to review Microsoft recommended actions to help improve email and collaboration security.

Question 13 Single Choice
Scenario: Anvil is a private military firm founded by Billy Russo with the purpose of providing military and security services. The company specializes in its activity in military contract services, such as personal protection, convoy security, and tactical operations.
To keep ahead of the technological curve, Billy has adopted Microsoft as a core system for the company and has deployed Microsoft 365 applications to all employees.
Who is responsible for the security of the personal data relating to these employees?
Explanation

Click "Show Answer" to see the explanation here
In the shared responsibility model, the customer organization always has responsibility for their data, including personal data relating to employees.
Shared responsibility model
The shared responsibility model identifies which security tasks are handled by the cloud provider, and which security tasks are handled by you, the customer.
In organizations running only on-premises hardware and software, the organization is 100 percent responsible for implementing security and compliance. With cloud-based services, that responsibility is shared between the customer and the cloud provider.
The responsibilities vary depending on where the workload is hosted:
Software as a Service (SaaS)
Platform as a Service (PaaS)
Infrastructure as a Service (IaaS)
On-premises datacentre (On-prem)
The shared responsibility model makes responsibilities clear. When organizations move data to the cloud, some responsibilities transfer to the cloud provider and some to the customer organization.
The following diagram illustrates the areas of responsibility between the customer and the cloud provider, according to where data is held.
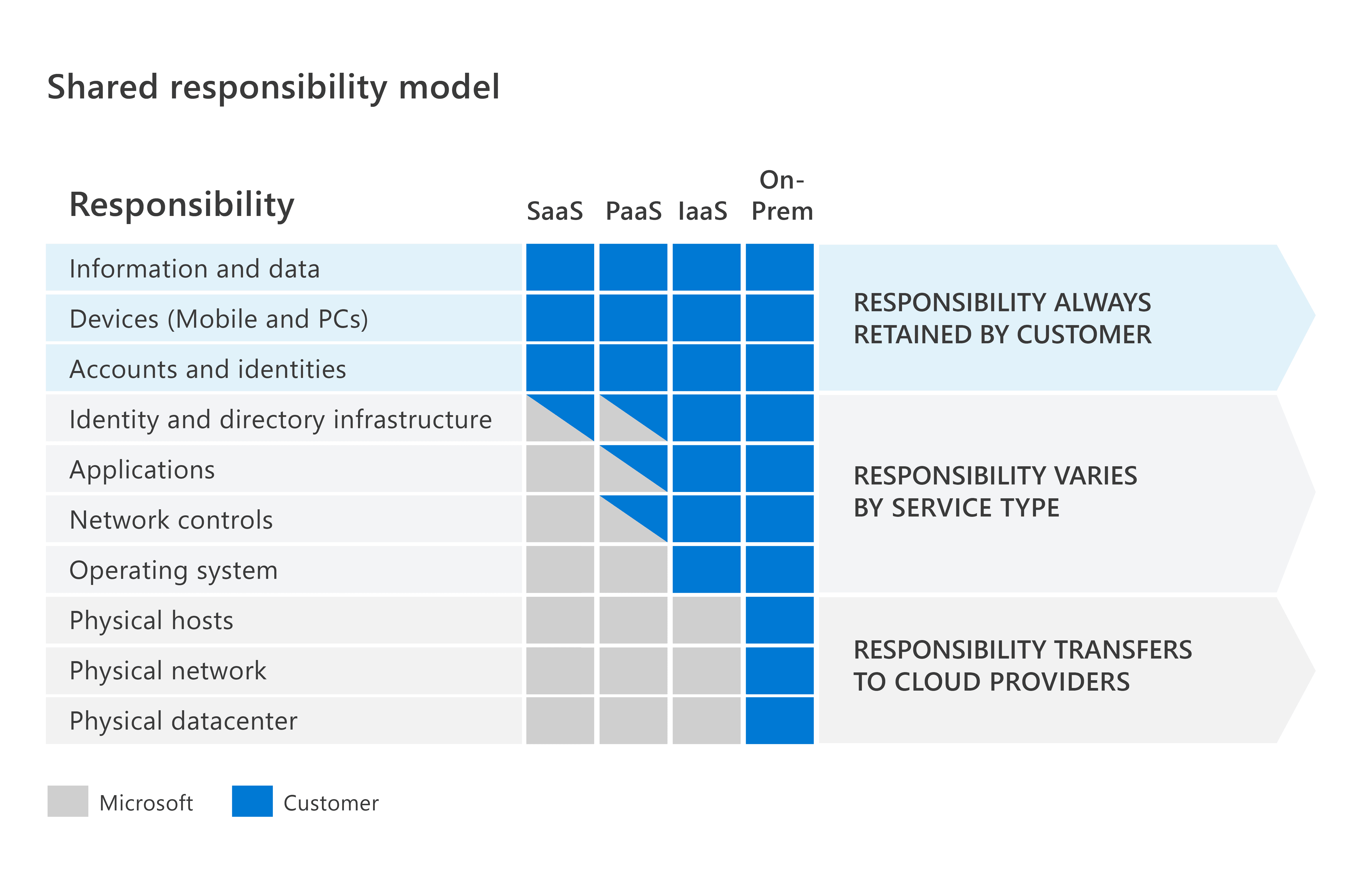
On-premises datacentres
In an on-premises datacentre, you have responsibility for everything from physical security to encrypting sensitive data.
Infrastructure as a Service (IaaS)
Of all cloud services, IaaS requires the most management by the cloud customer. With IaaS, you're using the cloud provider’s computing infrastructure. The cloud customer isn't responsible for the physical components, such as computers and the network, or the physical security of the datacentre. However, the cloud customer still has responsibility for software components such as operating systems, network controls, applications, and protecting data.
Platform as a Service (PaaS)
PaaS provides an environment for building, testing, and deploying software applications. The goal of PaaS is to help you create an application quickly without managing the underlying infrastructure. With PaaS, the cloud provider manages the hardware and operating systems, and the customer is responsible for applications and data.
Software as a Service (SaaS)
SaaS is hosted and managed by the cloud provider, for the customer. It's usually licensed through a monthly or annual subscription. Microsoft 365, Skype, and Dynamics CRM Online are all examples of SaaS software. SaaS requires the least amount of management by the cloud customer. The cloud provider is responsible for managing everything except data, devices, accounts, and identities.
For all cloud deployment types you, the cloud customer, own your data and identities. You're responsible for protecting the security of your data and identities, and on-premises resources.
In summary, responsibilities always retained by the customer organization include:
Information and data
Devices (mobile and PCs)
Accounts and identities
The benefit of the shared responsibility model is that organizations are clear about their responsibilities, and those of the cloud provider.
https://docs.microsoft.com/en-us/azure/security/fundamentals/shared-responsibility
Explanation
In the shared responsibility model, the customer organization always has responsibility for their data, including personal data relating to employees.
Shared responsibility model
The shared responsibility model identifies which security tasks are handled by the cloud provider, and which security tasks are handled by you, the customer.
In organizations running only on-premises hardware and software, the organization is 100 percent responsible for implementing security and compliance. With cloud-based services, that responsibility is shared between the customer and the cloud provider.
The responsibilities vary depending on where the workload is hosted:
Software as a Service (SaaS)
Platform as a Service (PaaS)
Infrastructure as a Service (IaaS)
On-premises datacentre (On-prem)
The shared responsibility model makes responsibilities clear. When organizations move data to the cloud, some responsibilities transfer to the cloud provider and some to the customer organization.
The following diagram illustrates the areas of responsibility between the customer and the cloud provider, according to where data is held.

On-premises datacentres
In an on-premises datacentre, you have responsibility for everything from physical security to encrypting sensitive data.
Infrastructure as a Service (IaaS)
Of all cloud services, IaaS requires the most management by the cloud customer. With IaaS, you're using the cloud provider’s computing infrastructure. The cloud customer isn't responsible for the physical components, such as computers and the network, or the physical security of the datacentre. However, the cloud customer still has responsibility for software components such as operating systems, network controls, applications, and protecting data.
Platform as a Service (PaaS)
PaaS provides an environment for building, testing, and deploying software applications. The goal of PaaS is to help you create an application quickly without managing the underlying infrastructure. With PaaS, the cloud provider manages the hardware and operating systems, and the customer is responsible for applications and data.
Software as a Service (SaaS)
SaaS is hosted and managed by the cloud provider, for the customer. It's usually licensed through a monthly or annual subscription. Microsoft 365, Skype, and Dynamics CRM Online are all examples of SaaS software. SaaS requires the least amount of management by the cloud customer. The cloud provider is responsible for managing everything except data, devices, accounts, and identities.
For all cloud deployment types you, the cloud customer, own your data and identities. You're responsible for protecting the security of your data and identities, and on-premises resources.
In summary, responsibilities always retained by the customer organization include:
Information and data
Devices (mobile and PCs)
Accounts and identities
The benefit of the shared responsibility model is that organizations are clear about their responsibilities, and those of the cloud provider.
https://docs.microsoft.com/en-us/azure/security/fundamentals/shared-responsibility
Question 14 Single Choice
True or False: Microsoft Defender for Office 365 is included in all subscriptions.
Explanation

Click "Show Answer" to see the explanation here
Microsoft Defender for Office 365 is included in certain subscriptions, such as Microsoft 365 E5, Office 365 E5, Office 365 A5, and Microsoft 365 Business Premium. If your subscription doesn’t include Defender for Office 365, you can purchase it as an add-on.
Microsoft Defender for Office 365
Microsoft Defender for Office 365, formerly Office 365 Advanced Threat Protection, safeguards your organization against malicious threats posed by email messages, links (URLs), and collaboration tools, including Microsoft Teams, SharePoint Online, OneDrive for Business, and other Office clients.
Microsoft Defender for Office 365 covers these key areas:
Threat protection policies: Define threat protection policies to set the appropriate level of protection for your organization.
Reports: View real-time reports to monitor Microsoft Defender for Office 365 performance in your organization.
Threat investigation and response capabilities: Use leading-edge tools to investigate, understand, simulate, and prevent threats.
Automated investigation and response capabilities: Save time and effort investigating and mitigating threats.
Microsoft Defender for Office 365 is available in two plans. The plan you choose influences the tools you’ll see and use. It's important to make sure you select the best plan to meet your organization's needs.
Microsoft Defender for Office 365 Plan 1
This plan offers configuration, protection, and detection tools for your Office 365 suite:
Safe Attachments: Checks email attachments for malicious content.
Safe Links: Links are scanned for each click. A safe link remains accessible, but malicious links are blocked.
Safe Attachments for SharePoint, OneDrive, and Microsoft Teams: Protects your organization when users collaborate and share files by identifying and blocking malicious files in team sites and document libraries.
Anti-phishing protection: Detects attempts to impersonate your users and internal or custom domains.
Real-time detections: A real-time report that allows you to identify and analyze recent threats.
Microsoft Defender for Office 365 Plan 2
This plan includes all the core features of Plan 1, and provides automation, investigation, remediation, and simulation tools to help protect your Office 365 suite:
Threat Trackers: Provide the latest intelligence on prevailing cybersecurity issues and allow an organization to take countermeasures before there's an actual threat.
Threat Explorer: A real-time report that allows you to identify and analyze recent threats.
Automated investigation and response (AIR): Includes a set of security playbooks that can be launched automatically, such as when an alert is triggered, or manually. A security playbook can start an automated investigation, provide detailed results, and recommend actions that the security team can approve or reject.
Attack Simulator: Allows you to run realistic attack scenarios in your organization to identify vulnerabilities.
Microsoft Defender for Office 365 availability
Microsoft Defender for Office 365 is included in certain subscriptions, such as Microsoft 365 E5, Office 365 E5, Office 365 A5, and Microsoft 365 Business Premium.
If your subscription doesn’t include Defender for Office 365, you can purchase it as an add-on.
Use Microsoft Defender for Office 365 to protect your organization's collaboration tools and messages.
Explanation
Microsoft Defender for Office 365 is included in certain subscriptions, such as Microsoft 365 E5, Office 365 E5, Office 365 A5, and Microsoft 365 Business Premium. If your subscription doesn’t include Defender for Office 365, you can purchase it as an add-on.
Microsoft Defender for Office 365
Microsoft Defender for Office 365, formerly Office 365 Advanced Threat Protection, safeguards your organization against malicious threats posed by email messages, links (URLs), and collaboration tools, including Microsoft Teams, SharePoint Online, OneDrive for Business, and other Office clients.
Microsoft Defender for Office 365 covers these key areas:
Threat protection policies: Define threat protection policies to set the appropriate level of protection for your organization.
Reports: View real-time reports to monitor Microsoft Defender for Office 365 performance in your organization.
Threat investigation and response capabilities: Use leading-edge tools to investigate, understand, simulate, and prevent threats.
Automated investigation and response capabilities: Save time and effort investigating and mitigating threats.
Microsoft Defender for Office 365 is available in two plans. The plan you choose influences the tools you’ll see and use. It's important to make sure you select the best plan to meet your organization's needs.
Microsoft Defender for Office 365 Plan 1
This plan offers configuration, protection, and detection tools for your Office 365 suite:
Safe Attachments: Checks email attachments for malicious content.
Safe Links: Links are scanned for each click. A safe link remains accessible, but malicious links are blocked.
Safe Attachments for SharePoint, OneDrive, and Microsoft Teams: Protects your organization when users collaborate and share files by identifying and blocking malicious files in team sites and document libraries.
Anti-phishing protection: Detects attempts to impersonate your users and internal or custom domains.
Real-time detections: A real-time report that allows you to identify and analyze recent threats.
Microsoft Defender for Office 365 Plan 2
This plan includes all the core features of Plan 1, and provides automation, investigation, remediation, and simulation tools to help protect your Office 365 suite:
Threat Trackers: Provide the latest intelligence on prevailing cybersecurity issues and allow an organization to take countermeasures before there's an actual threat.
Threat Explorer: A real-time report that allows you to identify and analyze recent threats.
Automated investigation and response (AIR): Includes a set of security playbooks that can be launched automatically, such as when an alert is triggered, or manually. A security playbook can start an automated investigation, provide detailed results, and recommend actions that the security team can approve or reject.
Attack Simulator: Allows you to run realistic attack scenarios in your organization to identify vulnerabilities.
Microsoft Defender for Office 365 availability
Microsoft Defender for Office 365 is included in certain subscriptions, such as Microsoft 365 E5, Office 365 E5, Office 365 A5, and Microsoft 365 Business Premium.
If your subscription doesn’t include Defender for Office 365, you can purchase it as an add-on.
Use Microsoft Defender for Office 365 to protect your organization's collaboration tools and messages.
Question 15 Single Choice
Scenario: Dr. Karl Malus works for the Power Broker Corporation (PBC) founded by Curtiss Jackson, using technology to service various countries and their military efforts. You have been contracted by the company to assist Dr. Malus with their Microsoft Azure implementation.
The IT team at PBC is planning to employ an SSH client to access the SSH to the Azure virtual machine in their Azure portal. Dr. Malus is concerned that this may not be the best way to proceed and comes to you for your advice.
Does PBC need an SSH client to access the SSH to the Azure virtual machine in their Azure portal?
Explanation

Click "Show Answer" to see the explanation here
No - You don't need an RDP or SSH client to access the RDP/SSH to your Azure virtual machine in your Azure portal. Use the Azure portal to let you get RDP/SSH access to your virtual machine directly in the browser.
Azure Bastion
Azure Bastion is a service you deploy that lets you connect to a virtual machine using your browser and the Azure portal. The Azure Bastion service is a fully platform-managed PaaS service that you provision inside your virtual network. It provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS. When you connect via Azure Bastion, your virtual machines do not need a public IP address, agent, or special client software.
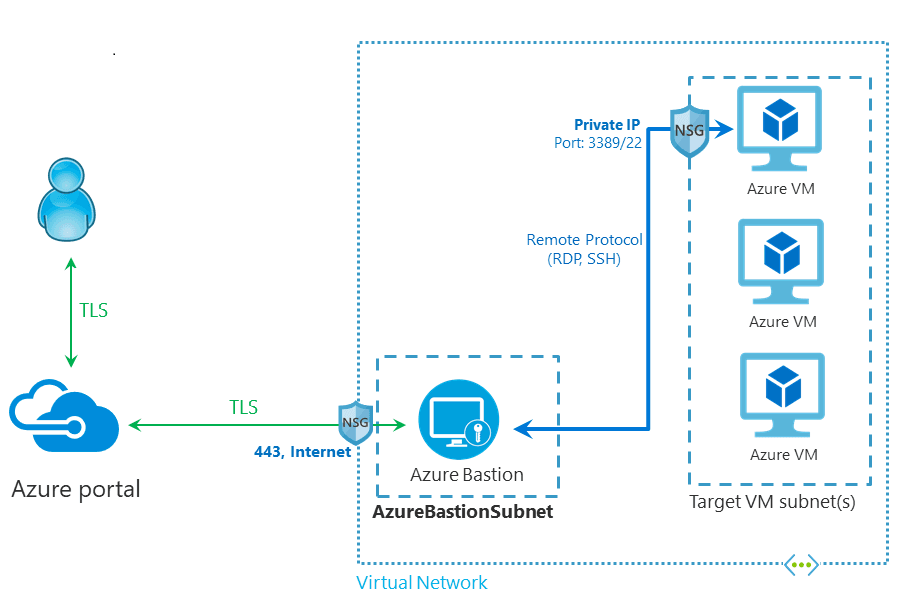
Bastion provides secure RDP and SSH connectivity to all of the VMs in the virtual network in which it is provisioned. Using Azure Bastion protects your virtual machines from exposing RDP/SSH ports to the outside world, while still providing secure access using RDP/SSH.
https://docs.microsoft.com/en-us/azure/bastion/bastion-overview
Explanation
No - You don't need an RDP or SSH client to access the RDP/SSH to your Azure virtual machine in your Azure portal. Use the Azure portal to let you get RDP/SSH access to your virtual machine directly in the browser.
Azure Bastion
Azure Bastion is a service you deploy that lets you connect to a virtual machine using your browser and the Azure portal. The Azure Bastion service is a fully platform-managed PaaS service that you provision inside your virtual network. It provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS. When you connect via Azure Bastion, your virtual machines do not need a public IP address, agent, or special client software.

Bastion provides secure RDP and SSH connectivity to all of the VMs in the virtual network in which it is provisioned. Using Azure Bastion protects your virtual machines from exposing RDP/SSH ports to the outside world, while still providing secure access using RDP/SSH.
https://docs.microsoft.com/en-us/azure/bastion/bastion-overview
Question 16 Single Choice
Scenario: Mercs for Money is a collection of mercenaries gathered together by Wade Wilson who organized the group and is now a successful Professional Services enterprise. Looking to improve the operations of the organization, Wade has contracted you to assist with several IT projects.
Justin Hammer is a new hire at Mercs for Money and he likes to show-off his vast knowledge about Azure, which many times is inaccurate. The team is in the break room and Justin is talking about how Azure AD is an identity and access management service.
Is Justin correct, is Azure AD an identity and access management service?
Explanation

Click "Show Answer" to see the explanation here
Yes - Azure Active Directory (Azure AD) is a cloud-based user identity and authentication service.
Microsoft 365 identity models and Azure Active Directory
Microsoft 365 uses Azure Active Directory (Azure AD), a cloud-based user identity and authentication service that is included with your Microsoft 365 subscription, to manage identities and authentication for Microsoft 365. Getting your identity infrastructure configured correctly is vital to managing Microsoft 365 user access and permissions for your organization.
https://www.microsoft.com/en-us/videoplayer/embed/RE2Pjwu
Explanation
Yes - Azure Active Directory (Azure AD) is a cloud-based user identity and authentication service.
Microsoft 365 identity models and Azure Active Directory
Microsoft 365 uses Azure Active Directory (Azure AD), a cloud-based user identity and authentication service that is included with your Microsoft 365 subscription, to manage identities and authentication for Microsoft 365. Getting your identity infrastructure configured correctly is vital to managing Microsoft 365 user access and permissions for your organization.

https://www.microsoft.com/en-us/videoplayer/embed/RE2Pjwu
Question 17 Single Choice
Scenario: You have been contracted by Wayne Enterprises, a company owned by Bruce Wayne with a market value of over twenty-seven million dollars. Bruce founded Wayne Enterprises shortly after he created the Wayne Foundation and he became the president and chairman of the company.
Bruce has come to you because his IT team is evaluating the implementation of single sign-on.
What is a benefit of single sign-on?
Explanation

Click "Show Answer" to see the explanation here
With single sign-on, a user signs in once and can then access a number of applications or resources.
Modern authentication and the role of the identity provider
Modern authentication is an umbrella term for authentication and authorization methods between a client, such as your laptop or phone, and a server, like a website or application. At the centre of modern authentication is the role of the identity provider. An identity provider creates, maintains, and manages identity information while offering authentication, authorization, and auditing services.
With modern authentication, all services, including all authentication services, are supplied by a central identity provider. Information that's used to authenticate the user with the server is stored and managed centrally by the identity provider.
With a central identity provider, organizations can establish authentication and authorization policies, monitor user behaviour, identify suspicious activities, and reduce malicious attacks.
https://www.microsoft.com/en-ca/videoplayer/embed/RE4Kdt9?postJsllMsg=true&autoCaptions=en-ca
As you see in the video, thanks to modern authentication, the client communicates with the identity provider by giving an identity that can be authenticated. When the identity (which can be a user or an application) has been verified, the identity provider issues a security token that the client sends to the server.
The server validates the security token through its trust relationship with the identity provider. By using the security token and the information that's contained within it, the user or application accesses the required resources on the server. In this scenario, the token and the information it contains is stored and managed by the identity provider. The centralized identity provider is supplying the authentication service.
Microsoft Azure Active Directory is an example of a cloud-based identity provider. Other examples include Twitter, Google, Amazon, LinkedIn, and GitHub.
Single sign-on
Another fundamental capability of an identity provider and “modern authentication” is the support for single sign-on (SSO). With SSO, the user logs in once and that credential is used to access multiple applications or resources. When you set up SSO between multiple identity providers, it's called federation.
https://docs.microsoft.com/en-us/azure/active-directory/develop/authentication-vs-authorization
Explanation
With single sign-on, a user signs in once and can then access a number of applications or resources.
Modern authentication and the role of the identity provider
Modern authentication is an umbrella term for authentication and authorization methods between a client, such as your laptop or phone, and a server, like a website or application. At the centre of modern authentication is the role of the identity provider. An identity provider creates, maintains, and manages identity information while offering authentication, authorization, and auditing services.
With modern authentication, all services, including all authentication services, are supplied by a central identity provider. Information that's used to authenticate the user with the server is stored and managed centrally by the identity provider.
With a central identity provider, organizations can establish authentication and authorization policies, monitor user behaviour, identify suspicious activities, and reduce malicious attacks.

https://www.microsoft.com/en-ca/videoplayer/embed/RE4Kdt9?postJsllMsg=true&autoCaptions=en-ca
As you see in the video, thanks to modern authentication, the client communicates with the identity provider by giving an identity that can be authenticated. When the identity (which can be a user or an application) has been verified, the identity provider issues a security token that the client sends to the server.
The server validates the security token through its trust relationship with the identity provider. By using the security token and the information that's contained within it, the user or application accesses the required resources on the server. In this scenario, the token and the information it contains is stored and managed by the identity provider. The centralized identity provider is supplying the authentication service.
Microsoft Azure Active Directory is an example of a cloud-based identity provider. Other examples include Twitter, Google, Amazon, LinkedIn, and GitHub.
Single sign-on
Another fundamental capability of an identity provider and “modern authentication” is the support for single sign-on (SSO). With SSO, the user logs in once and that credential is used to access multiple applications or resources. When you set up SSO between multiple identity providers, it's called federation.
https://docs.microsoft.com/en-us/azure/active-directory/develop/authentication-vs-authorization
Question 18 Single Choice
Scenario: The Red Lion National Bank is an offshore firm managed by Felix Manning and Wilson Fisk. The bank is migrating to Microsoft Azure and has hired you as an Expert Consultant to oversee their IT team and to assist as needed.
The IT team is implementing Network Security Groups (NSGs) to filter traffic based on IP address, protocol, and port. Wilson is concerned that NSGs may not be the correct solution for the job.
Can NSGs filter traffic based on IP address, protocol, and / or port?
Explanation

Click "Show Answer" to see the explanation here
Yes - You can use an Azure network security group to filter network traffic to and from Azure resources in an Azure virtual network. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources. For each rule, you can specify source and destination, port, and protocol.
Network security groups
You can use an Azure network security group to filter network traffic to and from Azure resources in an Azure virtual network. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources. For each rule, you can specify source and destination, port, and protocol.
Security rules
A network security group contains zero, or as many rules as desired, within Azure subscription limits. Each rule specifies the following properties:
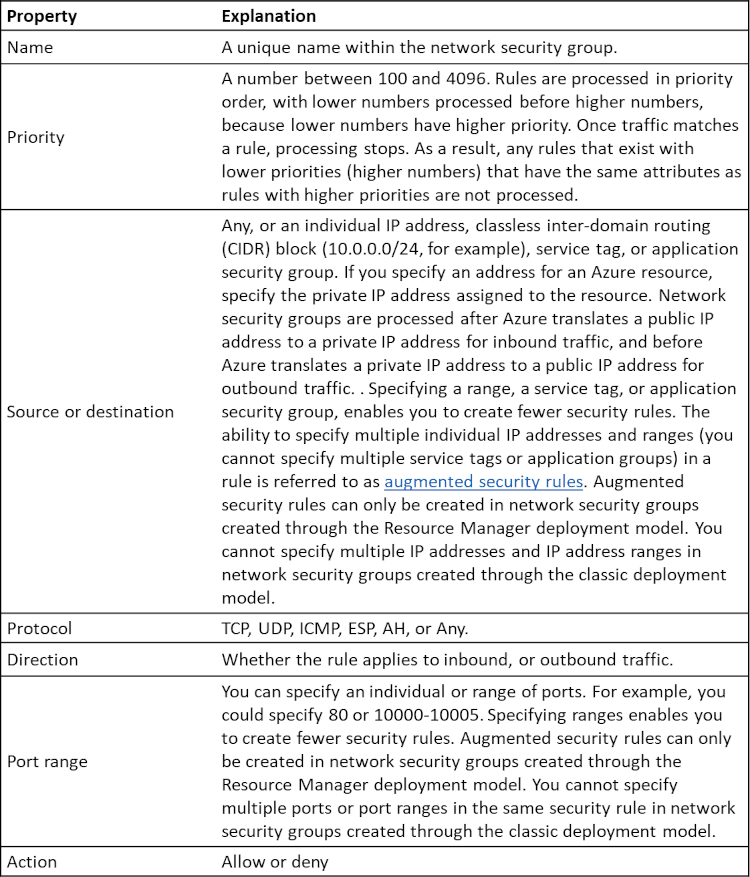
Network security group security rules are evaluated by priority using the 5-tuple information (source, source port, destination, destination port, and protocol) to allow or deny the traffic. You may not create two security rules with the same priority and direction. A flow record is created for existing connections. Communication is allowed or denied based on the connection state of the flow record. The flow record allows a network security group to be stateful. If you specify an outbound security rule to any address over port 80, for example, it's not necessary to specify an inbound security rule for the response to the outbound traffic. You only need to specify an inbound security rule if communication is initiated externally. The opposite is also true. If inbound traffic is allowed over a port, it's not necessary to specify an outbound security rule to respond to traffic over the port.
Existing connections may not be interrupted when you remove a security rule that enabled the flow. Traffic flows are interrupted when connections are stopped and no traffic is flowing in either direction, for at least a few minutes.
There are limits to the number of security rules you can create in a network security group.
https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
Explanation
Yes - You can use an Azure network security group to filter network traffic to and from Azure resources in an Azure virtual network. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources. For each rule, you can specify source and destination, port, and protocol.
Network security groups
You can use an Azure network security group to filter network traffic to and from Azure resources in an Azure virtual network. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources. For each rule, you can specify source and destination, port, and protocol.
Security rules
A network security group contains zero, or as many rules as desired, within Azure subscription limits. Each rule specifies the following properties:

Network security group security rules are evaluated by priority using the 5-tuple information (source, source port, destination, destination port, and protocol) to allow or deny the traffic. You may not create two security rules with the same priority and direction. A flow record is created for existing connections. Communication is allowed or denied based on the connection state of the flow record. The flow record allows a network security group to be stateful. If you specify an outbound security rule to any address over port 80, for example, it's not necessary to specify an inbound security rule for the response to the outbound traffic. You only need to specify an inbound security rule if communication is initiated externally. The opposite is also true. If inbound traffic is allowed over a port, it's not necessary to specify an outbound security rule to respond to traffic over the port.
Existing connections may not be interrupted when you remove a security rule that enabled the flow. Traffic flows are interrupted when connections are stopped and no traffic is flowing in either direction, for at least a few minutes.
There are limits to the number of security rules you can create in a network security group.
https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
Question 19 Single Choice
An organization's data is constantly growing and users are storing and sharing data in new directions. For security and compliance administrators, the task of discovering, protecting, and governing sensitive data is one that never ends. The growth of data, also represents challenges for data consumers who might be unaware of a data source.
For data producers, those who are responsible for producing and maintaining information assets, creating and maintaining documentation for data sources is complex and time-consuming. Restricting access to data sources and ensuring that data consumers know how to request access is an ongoing challenge.
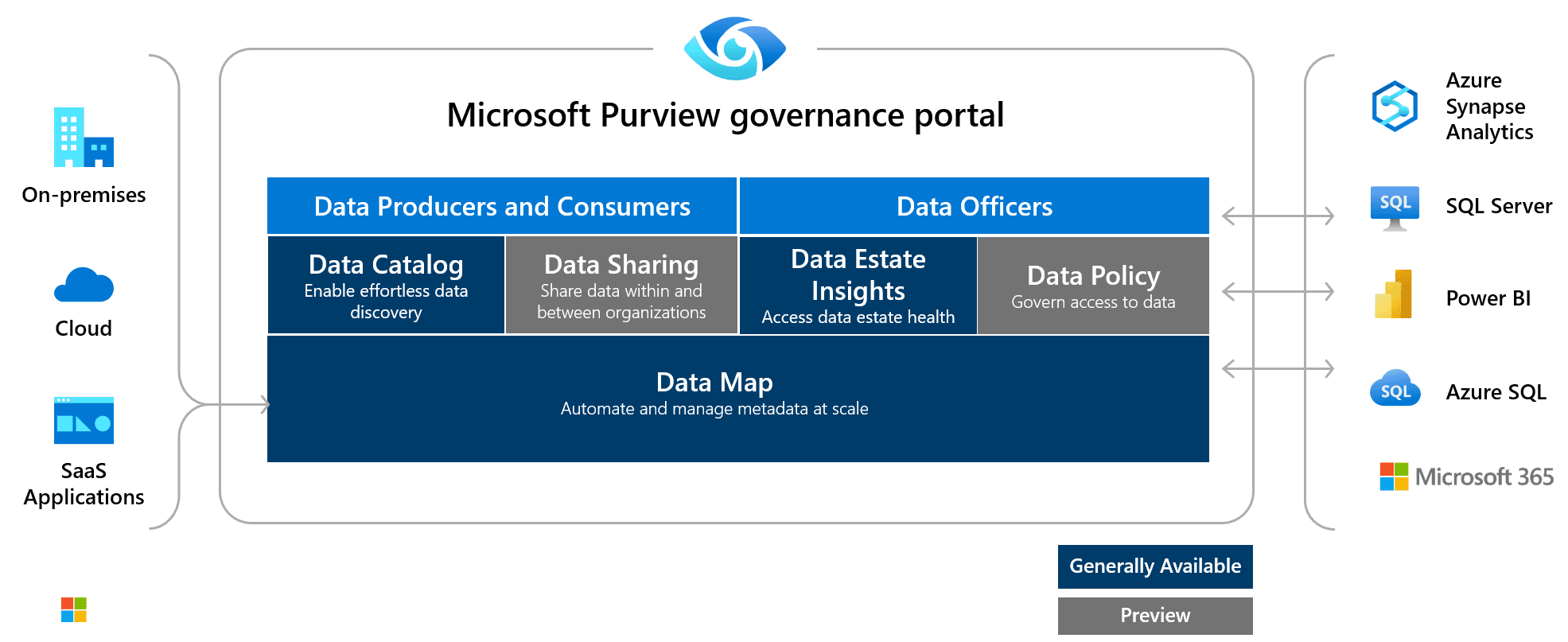
Which application in the Microsoft Purview governance portal is used to capture metadata about enterprise data, to identify and classify sensitive data?
Explanation

Click "Show Answer" to see the explanation here
Microsoft Purview Data Map is able to capture metadata about enterprise data, to identify and classify sensitive data.
Microsoft Purview Data Catalogue enables business and technical users to quickly and easily find relevant data.
Microsoft Purview Data Estate Insights provides a bird’s eye view of what data is actively scanned, where sensitive data is, and how it moves.
Microsoft Purview Data Sharing enables organizations to securely share data both within your organization or cross organizations with business partners and customers.
Access policies in Microsoft Purview enable you to manage access to different data systems across your entire data estate. For example, if a user needs read access to an Azure Storage account that has been registered in Microsoft Purview, you can grant this access directly in Microsoft Purview by creating a data access policy through the Policy management app in the Microsoft Purview governance portal.
Microsoft Purview governance portal
Microsoft Purview is designed to address the challenges associated with the rapid growth of data and to help enterprises get the most value from their information assets.
The Microsoft Purview governance portal provides a unified data governance service that helps you manage your on-premises, multicloud, and software-as-a-service (SaaS) data. The Microsoft Purview governance portal allows you to:
Create a holistic, up-to-date map of your data landscape with automated data discovery, sensitive data classification, and end-to-end data lineage.
Enable data curators to manage and secure your data estate.
Empower data consumers to find valuable, trustworthy data.
Data Map
Microsoft Purview Data Map provides the foundation for data discovery and data governance. By scanning registered data sources, Azure Purview Data Map is able to capture metadata about enterprise data, to identify and classify sensitive data. Microsoft Purview supports Azure data sources and various data source categories including databases, file storage, and applications and services from third parties.
Data Catalogue
With the Microsoft Purview Data Catalogue, business and technical users can quickly and easily find relevant data using a search experience with filters based on various lenses like glossary terms, classifications, sensitivity labels and more.
Data Estate Insights
With the Microsoft Purview Data Estate Insights, data officers and security officers can get a bird’s eye view and at a glance understand what data is actively scanned, where sensitive data is, and how it moves.
Data Sharing and Data Policy
Microsoft Purview Data Sharing enables organizations to securely share data both within your organization or cross organizations with business partners and customers.
Access policies in Microsoft Purview enable you to manage access to different data systems across your entire data estate. For example, if a user needs read access to an Azure Storage account that has been registered in Microsoft Purview, you can grant this access directly in Microsoft Purview by creating a data access policy through the Policy management app in the Microsoft Purview governance portal.
https://learn.microsoft.com/en-us/azure/purview/use-microsoft-purview-governance-portal
Explanation
Microsoft Purview Data Map is able to capture metadata about enterprise data, to identify and classify sensitive data.
Microsoft Purview Data Catalogue enables business and technical users to quickly and easily find relevant data.
Microsoft Purview Data Estate Insights provides a bird’s eye view of what data is actively scanned, where sensitive data is, and how it moves.
Microsoft Purview Data Sharing enables organizations to securely share data both within your organization or cross organizations with business partners and customers.
Access policies in Microsoft Purview enable you to manage access to different data systems across your entire data estate. For example, if a user needs read access to an Azure Storage account that has been registered in Microsoft Purview, you can grant this access directly in Microsoft Purview by creating a data access policy through the Policy management app in the Microsoft Purview governance portal.
Microsoft Purview governance portal
Microsoft Purview is designed to address the challenges associated with the rapid growth of data and to help enterprises get the most value from their information assets.
The Microsoft Purview governance portal provides a unified data governance service that helps you manage your on-premises, multicloud, and software-as-a-service (SaaS) data. The Microsoft Purview governance portal allows you to:
Create a holistic, up-to-date map of your data landscape with automated data discovery, sensitive data classification, and end-to-end data lineage.
Enable data curators to manage and secure your data estate.
Empower data consumers to find valuable, trustworthy data.
Data Map
Microsoft Purview Data Map provides the foundation for data discovery and data governance. By scanning registered data sources, Azure Purview Data Map is able to capture metadata about enterprise data, to identify and classify sensitive data. Microsoft Purview supports Azure data sources and various data source categories including databases, file storage, and applications and services from third parties.
Data Catalogue
With the Microsoft Purview Data Catalogue, business and technical users can quickly and easily find relevant data using a search experience with filters based on various lenses like glossary terms, classifications, sensitivity labels and more.
Data Estate Insights
With the Microsoft Purview Data Estate Insights, data officers and security officers can get a bird’s eye view and at a glance understand what data is actively scanned, where sensitive data is, and how it moves.
Data Sharing and Data Policy
Microsoft Purview Data Sharing enables organizations to securely share data both within your organization or cross organizations with business partners and customers.
Access policies in Microsoft Purview enable you to manage access to different data systems across your entire data estate. For example, if a user needs read access to an Azure Storage account that has been registered in Microsoft Purview, you can grant this access directly in Microsoft Purview by creating a data access policy through the Policy management app in the Microsoft Purview governance portal.
https://learn.microsoft.com/en-us/azure/purview/use-microsoft-purview-governance-portal
Question 20 Single Choice
Scenario: The Brand Corporation is the science and research branch of the Roxxon Corporation which is managed by Melinda May and Phil Coulson. Melinda and Phil have decided to use Azure for the company to increase its efficiencies and security. Melinda hired you as an advisor to guide many projects to ensure their success.
After hearing of a breach at Wayne Enterprises, Melinda and Phil have asked the security team to improve identity security within Roxxon.
What should they implement immediately to provide the greatest protection to user identities?
Explanation

Click "Show Answer" to see the explanation here
Multifactor authentication would be the best to implement immediately as it dramatically improves the security of an identity.
Different authentication methods of Azure AD
Legacy applications have relied on a single form of authentication, most often a password. However, passwords are problematic for users, and easily compromised. Multifactor authentication requires more than one form of verification, such as a trusted device or a fingerprint scan, to prove that an identity is legitimate. It means that, even when an identity’s password has been compromised, a hacker can't access a resource.
Multifactor authentication dramatically improves the security of an identity, while still being simple for users. The extra authentication factor must be something that's difficult for an attacker to obtain or duplicate.
https://www.microsoft.com/en-ca/videoplayer/embed/RE4zhD7?postJsllMsg=true&autoCaptions=en-ca
Azure Active Directory multifactor authentication works by requiring:
Something you know – typically a password or PIN and
Something you have – such as a trusted device that's not easily duplicated, like a phone or hardware key or
Something you are – biometrics like a fingerprint or face scan.
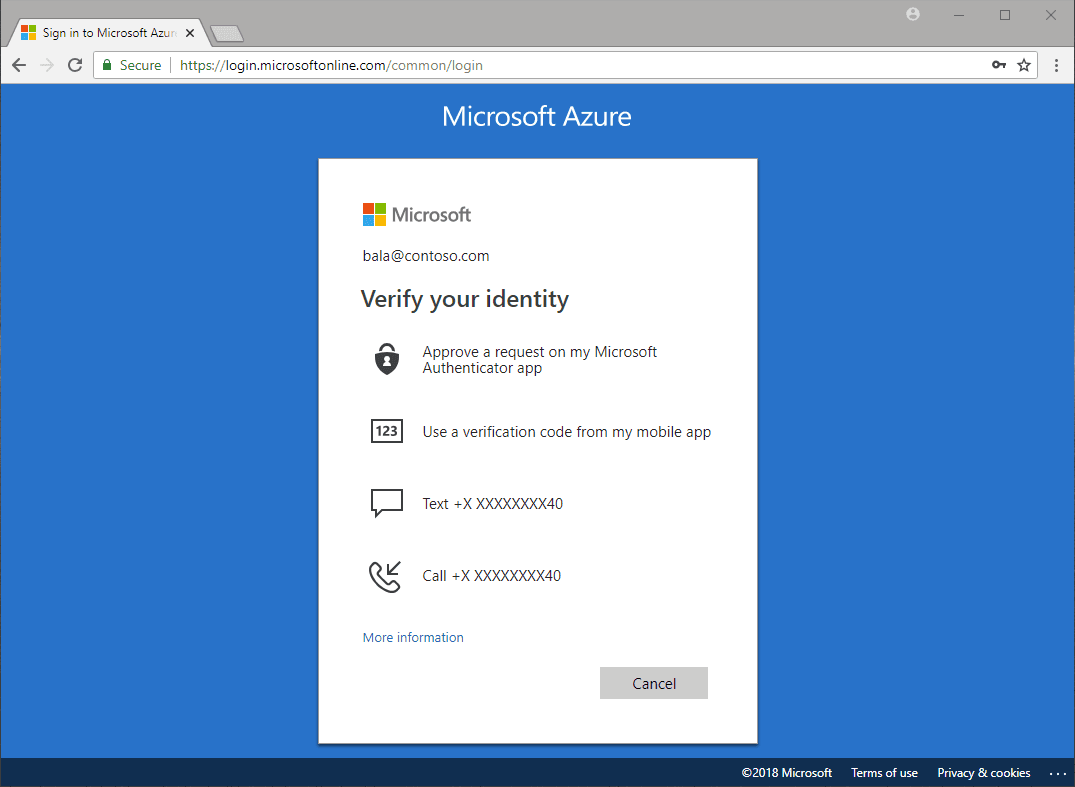
Multifactor authentication verification prompts are configured to be part of the Azure AD sign-in event. Azure AD automatically requests and processes multifactor authentication, without you making any changes to your applications or services. When a user signs in, they receive a multifactor authentication prompt, and can choose from one of the additional verification forms that they've registered.
An administrator can require certain verification methods, or the user can access their MyAccount to edit or add verification methods.
The following extra forms of verification can be used with Azure Active Directory multifactor authentication:
Microsoft Authenticator app
SMS
Voice call
OATH Hardware token
Security defaults and multifactor authentication
Security defaults are a set of basic identity security mechanisms recommended by Microsoft. When enabled, these recommendations will be automatically enforced in your organization. The goal is to ensure that all organizations have a basic level of security enabled at no extra cost. These defaults enable some of the most common security features and controls, including:
Enforcing Azure Active Directory multifactor authentication registration for all users.
Forcing administrators to use multifactor authentication.
Requiring all users to complete multifactor authentication when needed.
Security defaults are a great option for organizations that want to increase their security posture but don’t know where to start, or for organizations using the free tier of Azure AD licensing. Security defaults may not be appropriate for organizations with Azure AD premium licenses or more complex security requirements.
Explanation
Multifactor authentication would be the best to implement immediately as it dramatically improves the security of an identity.
Different authentication methods of Azure AD
Legacy applications have relied on a single form of authentication, most often a password. However, passwords are problematic for users, and easily compromised. Multifactor authentication requires more than one form of verification, such as a trusted device or a fingerprint scan, to prove that an identity is legitimate. It means that, even when an identity’s password has been compromised, a hacker can't access a resource.
Multifactor authentication dramatically improves the security of an identity, while still being simple for users. The extra authentication factor must be something that's difficult for an attacker to obtain or duplicate.
https://www.microsoft.com/en-ca/videoplayer/embed/RE4zhD7?postJsllMsg=true&autoCaptions=en-ca
Azure Active Directory multifactor authentication works by requiring:
Something you know – typically a password or PIN and
Something you have – such as a trusted device that's not easily duplicated, like a phone or hardware key or
Something you are – biometrics like a fingerprint or face scan.
Multifactor authentication verification prompts are configured to be part of the Azure AD sign-in event. Azure AD automatically requests and processes multifactor authentication, without you making any changes to your applications or services. When a user signs in, they receive a multifactor authentication prompt, and can choose from one of the additional verification forms that they've registered.
An administrator can require certain verification methods, or the user can access their MyAccount to edit or add verification methods.
The following extra forms of verification can be used with Azure Active Directory multifactor authentication:
Microsoft Authenticator app
SMS
Voice call
OATH Hardware token

Security defaults and multifactor authentication
Security defaults are a set of basic identity security mechanisms recommended by Microsoft. When enabled, these recommendations will be automatically enforced in your organization. The goal is to ensure that all organizations have a basic level of security enabled at no extra cost. These defaults enable some of the most common security features and controls, including:
Enforcing Azure Active Directory multifactor authentication registration for all users.
Forcing administrators to use multifactor authentication.
Requiring all users to complete multifactor authentication when needed.
Security defaults are a great option for organizations that want to increase their security posture but don’t know where to start, or for organizations using the free tier of Azure AD licensing. Security defaults may not be appropriate for organizations with Azure AD premium licenses or more complex security requirements.